Specops Key Recovery
Specops Key Recovery is a self-service solution for unlocking computers encrypted or managed by Symantec Endpoint Encryption or Microsoft BitLocker. A user who is locked out at the pre-boot authentication screen can use Specops Key Recovery to unlock their computer, without calling the helpdesk. For added security, users are verified with multi-factor authentication. The solution supports a number of authentication factors, including Symantec VIP, and Mobile Code (SMS) (sending a one-time code to a mobile device).
Specops Key Recovery currently supports:
- Symantec Endpoint Encryption (version 11 and higher)
- BitLocker managed by Symantec Endpoint Encryption (version 11 and higher)
- BitLocker
Central concepts
Pre-boot authentication screen
When a user powers on a computer with full-disk encryption, the pre-boot authentication screen will appear. Windows may not boot up until the user has correctly confirmed their identity on this screen.
Authentication
Authentication is the process of verifying the identity of a user. Typically, this requires the user to make a claim about their identity by entering their username and password.
Enrollment
Users are required to enroll with Specops Authentication. The enrollment process will vary for each type of identity service. To enroll with a personal identity service such as Google, users will need to follow the link from the Specops web application to the Google web page, and log in with the email address and password associated with their Google account.
Multi-factor authentication
Multi-factor authentication requires more than one method of authentication from independent categories of credentials: something you know (i.e. password), something you have (i.e. Mobile device), and something you are (i.e. Fingerprint). Specops uReset goes beyond two-factor authentication by supporting a broad range of identity services that can be used to increase security and flexibility. The solution not only supports common authenticators, such as questions and answers, and mobile verification codes, but also various digital identity services ranging from personal identity services (e.g. LinkedIn) to company identity services (e.g. salesforce.com), in addition to higher trust methods such as Smart Cards. The Specops multi-factor authentication model is dynamic. Users can choose which identity services they want to combine for enrollment and authentication, as long as they meet the requirements of the policy. Users enrolled with more identity services than required for their authentication will have authentication choice. This guarantees that end-users will always have the ability to satisfy the authentication policy, even if an identity service is unavailable (e.g. not having their mobile phone nearby).
Administrators can select, based on role and security policy, which identity services/authenticators they want to extend to end-users to verify their identity when resetting or unlocking their accounts. Such flexibility can ensure that varying security and flexibility needs are met. For example:
- For users that have a low-level security clearance, but a high flexibility need, such as students, IT admins can allow them to authenticate with a few personal identity services such as their Google ID.
- For users that have a higher level security clearance, such as financial aid administrators or senior level executives, IT admins can assign policies that enforce a higher number, or a stronger combination of identity services. This approach provides administrators with the flexibility they need to enforce policies that translate to greater security and efficiency.
Policy
A policy contains the rules required for enrollment and multi-factor authentication. A policy controls what identity services can be used, and how many must be used to verify the identity of end-users. The system administrator is responsible for configuring the rules in the policies.
Identity services
Identity services enable users to securely identify themselves when signing in. Identity services fall into multiple categories, including: username and password, social (LinkedIn, Tumblr), and higher trust (Google Authenticator, Microsoft Authenticator, Duo Security).
To use various identity services to authenticate users, the identity service must be configured (enabled) in Authentication Web, and the user affected by the policy must enroll with the identity service. Once a user has enrolled, they can use the identity service to authenticate. Specops Authentication uses data from user objects in Active Directory to read and write information used in the system.
Below is a list of all the standard identity services available in Specops Authentication.
Standard
- Specops Fingerprint: Specops Fingerprint enables users to enroll and authenticate using devices with fingerprint scanners, such as smartphones and tablets. Users can press their finger to the fingerprint scanner on their device to instantly identify themselves. Users can also use Face ID to authenticate, if they own an iPhone X and above. In order to use this identity service, users must have the app installed on their mobile device.
- Specops Authenticator: Users can authenticate using the Specops Authenticator app. Users scan a QR code or enter a secret. Specops Authenticator then provides users with a six-digit one-time password, which must be entered in order to successfully authenticate.
- Mobile Code (SMS): Users will receive a one-time six-digit password via an SMS message, which must be entered in order to successfully authenticate.
- Email: the user’s email is used as an identity service by sending a code to the registered email address that the user then has to input in the field on screen. Email does not require enrollment, since it references the email address in the email attribute in AD (or any other attribute if it is overridden); it can only be used with domains associated with Specops Authentication.
- Personal Email: the user’s email is used as an identity service by sending a code to the registered email address that the user then has to input in the field on screen. Personal Email has to be registered at enrollment by the user and they may use any email address of their choosing.
- Trusted Network Locations: Trusted Network Locations is an identity service that allows administrators to designate certain IP ranges as Trusted Network Locations.
- Manager Identification: When a user authenticates using Manager Identification, an email or SMS message is sent to their manager. Their manager must then approve the authentication request. Administrators can customize the notification that is sent, by adding custom information to the request notification. To make use of Manager Identification, each user must have a manager assigned to them in Active Directory, and manager accounts must have an email address/mobile phone number associated with their profile in order to receive authentication requests from users.
- Secret Questions: Users can select questions from a predetermined list and specify the answers to them. They must then answer these questions in order to authenticate successfully.
3rd Party
Note
In most cases, enrollment with third party identity services needs to be handled by users individually.
- PingID: With PingID, users can authenticate using the PingID mobile app.
- Duo Security: With Duo Security, users can authenticate using the Duo Security mobile app.
- Freja: With Freja, users can authenticate using the Freja mobile app.
- Okta Users can enroll and authenticate using their Okta account credentials. This can be done through the Okta app and by sending codes via text message.
- RSA SecurID Users can use their RSA Authenticator to authenticate.
- Symantec VIP: Users can authenticate using the Symantec VIP mobile app.
- Google Authenticator: Google Authenticator is an app that generates one-time passwords. A secret is generated and presented in the form of a QR code that the user scans. Google Authenticator then provides users with a six-to-eight-digit one-time password, which must be entered in order to successfully authenticate.
- Microsoft Authenticator: Microsoft Authenticator is an app that generates one-time passwords. A secret is generated and presented in the form of a QR code that the user scans. Microsoft Authenticator then provides users with a six-to-eight-digit one-time password, which must be entered in order to successfully authenticate.
- SITHS eID (Sweden): SITHS eID is a smart card-based authentication service, which enables employees (such as medical professionals) of authorities, municipalities, and county councils in Sweden to electronically identify themselves.
-
Mobile BankID (Sweden): If users have the Mobile BankID app, they can use this to verify their identity.
Note
Users will have to scan a QR code in the Mobile BankID app in order to authenticate with this identity service.
-
Yubikey: The Yubikey is a hardware authentication device. Users can authenticate by generating One Time Passwords (OTP) with their Yubikey (only if the Yubikey supports Yubico OTP as a security function). For more information on Yubikey, refer to the Yubikey page.
- Passkeys: Users can authenticate with passkeys they have already set up on their device. Passkeys are digital credentials (authenticators), tied to a user account and a website or application. Some examples of passkeys are Windows Hello, Yubikey, Bitwarden and any authentication app such as Google Authenticator.
- Entra ID: allows Specops Authentication to integrate with Microsoft Authentication Libraries. Microsoft Authenticator can be used to authenticate with Specops Authentication without using a password.
Federated
- Google: Users can enroll and authenticate using their Google account credentials.
- Microsoft Live: Users can enroll and authenticate using their Microsoft Live account credentials. Microsoft Live credentials are used to sign in to the Microsoft Cloud, including: Outlook, Office Online, OneDrive, Skype, Xbox Live, and the Microsoft store.
- LinkedIn: Users can enroll and authenticate using their LinkedIn credentials.
Architecture and Design
Specops Key Recovery is a component of the Specops Cloud. Specops Authentication, another component of the Specops Cloud, is used to authenticate to Specops Key Recovery. Authentication rules for accessing Specops Key Recovery can be defined on the Admin pages in the Specops Cloud.
To read user information from Active Directory, the Specops Cloud communicates with the Gatekeeper. The Gatekeeper is installed on a server in your domain. The Gatekeeper reads user information from Active Directory, and manages all operations against Active Directory, such as reading/writing enrollment data.
Key recovery for Symantec Endpoint Encryption
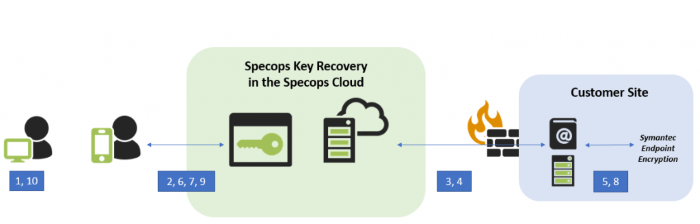
- The user forgets their password, and is locked out at the pre-boot authentication screen. The screen prompts the user to visit Specops Key Recovery on a mobile device.
- Specops Key Recovery (keyrecovery.specopssoft.com) redirects the user to Specops Authentication.
- Specops Authentication asks the Gatekeeper for the Group Policy Object that affects the user, and obtains the authentication rules to grant access to Specops Key Recovery. The authentication rules are displayed for the user. The user authenticates with various identity services to fulfill the policy, after which, the user is returned to Specops Key Recovery.
- Specops Key Recovery asks the Gatekeeper for a list of the user’s devices.
- The Gatekeeper asks Symantec Endpoint Encryption for the user’s devices, and a list is returned. The user’s computers are displayed on the key recovery page (keyrecovery.specopssoft.com).
- The user selects their locked computer from the list in Specops Key Recovery, and the browser is redirected to the recovery page.
- The user enters a sequence number on their mobile device and presses Continue. A key-pair is generated and the public key is sent with the sequence number to the Gatekeeper.
- The Gatekeeper asks Symantec Endpoint Encryption for a Recovery Key, based on the information the user has provided.
- Specops Key Recovery displays the Recovery Key to the user and instructs them to enter information on their locked computer.
- The user enters the Recovery Key on their locked computer. The computer then is unlocked.
Key recovery for BitLocker
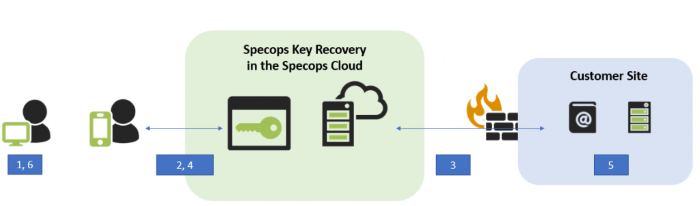
- The user forgets their password and navigates to Specops Key Recovery on a mobile device.
- Specops Key Recovery redirects to login.specopssoft.com.
- Specops Authentication asks the Gatekeeper for the Group Policy Object (GPO) that affects the user, and obtains the authentication rules to grant access to Specops Key Recovery. Authentication rules are displayed for the user and the user authenticates with various identity services, after which, they are returned to Specops Key Recovery.
- Specops Key Recovery asks the user to provide the first 8 characters of the Recovery Key ID, visible on their computer. The user enters the Recovery Key ID and presses Continue. A public key is generated and is sent together with the Recovery Key ID to the Gatekeeper.
- The Gatekeeper queries Active Directory to find the recovery password for the user’s computer. The recovery password is encrypted on the Gatekeeper, and then decrypted and displayed on the user’s mobile device.
- The user enters the recovery password on their locked computer. The computer is then unlocked.
