Specops Software released an update to its Specops Authentication platform today. The platform secures password resets, password changes, and encryption key recovery with multi-factor authentication (MFA) that supports various third-party MFA options including Symantec VIP. The updated version allows... Read More
Blog
How to evaluate breached password detection services
Keeping tabs on breached passwords is a must for those embroiled in the IT security battle. According to the 2020 Data Breach Investigations Report, 80% of data breaches in 2020 stemmed from stolen or brute-forced credentials. The stakes are... Read More
NIST Password Reset Guidelines
Passwords are necessary for authentication to different types of technology systems used in businesses today. Yet, they are a dangerous form of information from a security perspective. To strengthen password security, organizations want to take note of password best... Read More
Impact of running Specops Password Policy on Active Directory
We are often asked about the technical impact of using our solutions on Active Directory (AD), and other services. In this blog post, we will look at the impact of Specops Password Policy and Breached Password Protection. See part... Read More
Impact of running Specops Password Auditor on Active Directory
Many organizations use Specops Password Auditor (SPA), Specops Password Policy (SPP), and Breached Password Protection (BPP) to help improve the security and password hygiene of their Active Directory (AD). They often run SPA first. Why not? It’s free (download... Read More
What is the California default password law?
Passwords have become a subject of scrutiny, not only in IT security operations, but even extending out into new legislative mandates that have brought passwords into clear focus. California’s Senate Bill 327 (SB-327) was enacted in 2018 and became... Read More
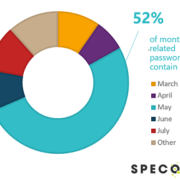
Predictable passwords: which seasons and months are most common in compromised passwords?
Summer reigns supreme among passwords. Today, on international #ChangeYourPasswordDay, Specops Software has released the latest breached password analysis data. “There is an ongoing debate about whether passwords should be changed at regular intervals, since forcing users usually results in... Read More
Hybrid Entra ID (formerly Azure AD) environments and third-party password tools
Can we leverage third-party password tools like Specops Password Policy in hybrid Azure AD environments? The answer is yes, and this blog will explain how. Read More
Active Directory Account Lockout Policy
We’ve touched on the critical importance of password management, and Account Lockout Policy builds on this further. Most failed login attempts are accidental—a user enters their password incorrectly, which happens from time to time. We’re human. However, user accounts... Read More
Introduction to Active Directory banned password lists
Cloud security has become a chief concern for security admins as platforms increase in popularity. These solutions are used daily and host a vast array of resources that teams must be able to securely access from anywhere. These remote... Read More