This website uses cookies to ensure you get the best experience on our website. Learn more
How to unlock active directory account lockouts
Table of Contents
There is no question that one of the most common tasks that helpdesk and IT admins carry out on a daily basis is user account management. Specifically, triaging user account issues like unlocking active directory accounts in an Active Directory domain environment takes a tremendous amount of time in across most environments.
Now that a majority of users have been working from home since the beginning of the year due to the global pandemic, helpdesk staff have been bombarded by a number of support issues on top of normal user account management tasks. One of the most common types of user account issues that are experienced by end users is an account lockout. Accounts can become locked out for a number of different reasons. How can a locked Active Directory account be unlocked? How can helpdesk staff securely triage password resets and account lockouts over the phone with remote end users?
Why are Active Directory accounts locked out?
The check of an AD account lockout status showed that an account was indeed locked. You may wonder why an Active Directory account can even be locked out? When an account is locked out this means that Active Directory has seen a specified number of incorrect passwords attempted for the user account in question that have exceeded the threshold for locking the account out.
This is commonly seen with normal end user “fat fingering” of passwords or having the “Caps lock” key turned on when entering the password. When an account is locked out, even trying the right password will fail since the lockout basically renders the account unable for use during the specified account lockout duration.
An account lockout threshold is configured in an Active Directory Account Lockout Policy and is part of the normal security mechanisms that are generally in place in the enterprise for helping to secure Active Directory accounts. By default, the Account Lockout Policy is configured with a setting of “0 invalid logon attempts” which means it will tolerate infinite bad password attempts.
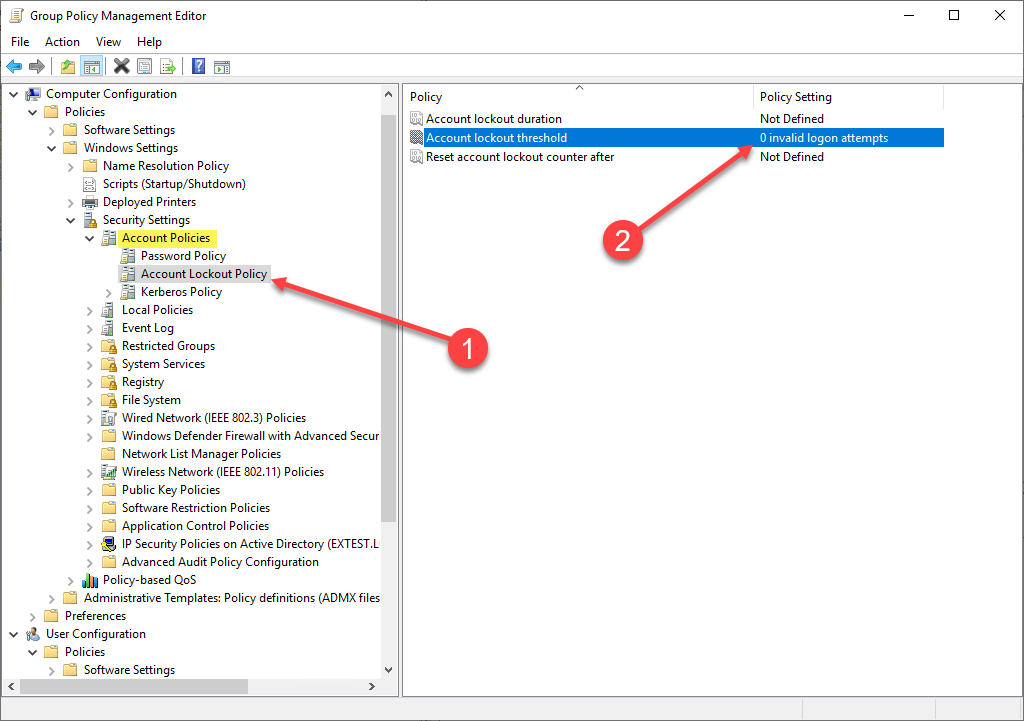
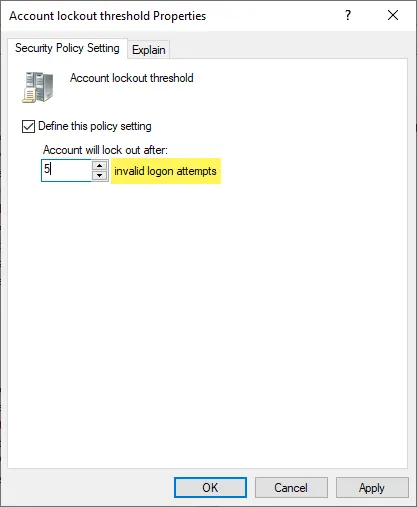
In most environments, an Account Lockout Policy will be configured anywhere from 3 to 10 invalid logon attempts. Below, we are setting a threshold of 5 invalid login attempts.
The Active Directory help page for the Account lockout threshold states this:
“This security setting determines the number of failed logon attempts that causes a user account to be locked out. A locked-out account cannot be used until it is reset by an administrator or until the lockout duration for the account has expired. You can set a value between 0 and 999 failed logon attempts. If you set the value to 0, the account will never be locked out.
Failed password attempts against workstations or member servers that have been locked using either CTRL+ALT+DELETE or password-protected screen savers count as failed logon attempts.
Default: 0.”
As stated in the description of the setting, there is another complimentary setting that goes along with the Account lockout threshold. This setting is the Account Lockout Duration. The account lockout duration defines how long the account is locked out. Typically, many organizations will set this to a period of time that is long enough to help bolster security and at the same time short enough to allow the account to unlock itself so the user can try to login again with the correct password.
The hope here is that an attacker would only get a few tries before the password is locked out. Then the account is locked out long enough that it would impede any progress to try and crack the user’s password. However, there are techniques that attackers use to successfully break into accounts such as password spraying. This involves trying only a few passwords against a large number of accounts. Also, databases of breached passwords provide very commonly used passwords that are often found configured on at least a few accounts in an environment.
How to unlock Active Directory account lockouts – steps
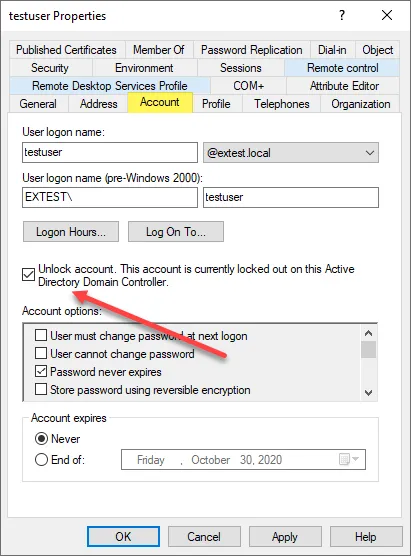
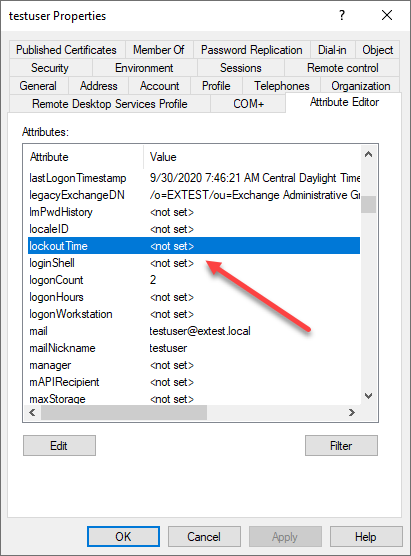
For helpdesk teams that are a few ways that accounts can be unlocked for those accounts that have been flagged with the account lockout attributes. The account below is currently not locked out. As you can see the lockedTime is not populated.
Accounts are generally unlocked with the following processes:
- The account duration expires
- The account is manually unlocked in ADUC
- The account is unlocked via PowerShell
Account duration interval change
The first unlock process is what we talked about earlier. The account duration interval is part of the account lockout policy. Once the interval has elapsed, the account is unlocked and can once again be used to login.
Manually unlocking in ADUC
The second way is what many admins may already be familiar with. This is simply using Active Directory Users and Computers (ADUC) to unlock the locked user account. This is found on the Account tab of the user account properties.

Account unlock via PowerShell
Using PowerShell, you can more find and unlock user accounts that are locked out in Active Directory. You can find accounts that are locked out with the following cmdlet:
Import-module Active DirectorySearch-ADAccount -LockedOut
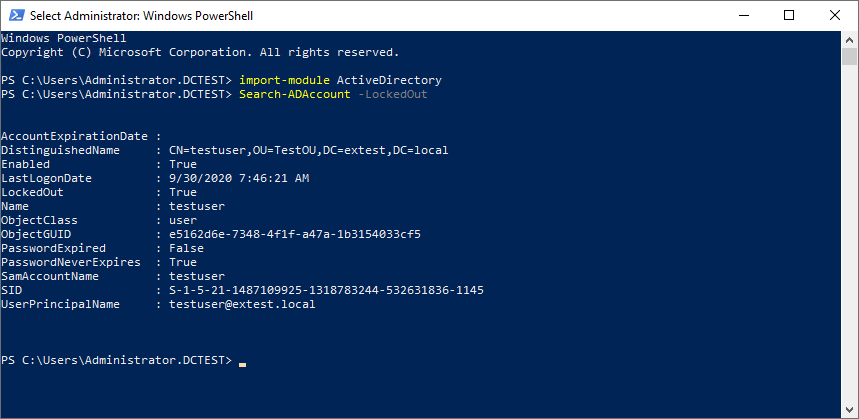
To unlock the locked accounts in Active Directory, you can use the unlock-ADAccount cmdlet and pipe in the cmdlet above.
Search-ADAccount -LockedOut | unlock-ADAccount
Once helpdesk technicians are familiar with using PowerShell for these types of operations, they generally find it to be much less cumbersome than using the ADUC GUI.
Secure Password Resets and Unlocks
Even with PowerShell and other scriptable utilities, the process to unlock accounts still involves a helpdesk technician or IT admin to perform the work of unlocking the user account. With many users now working remotely they are generally less accessible and are forced to call in to triage account issues. This can present security issues as helpdesk technicians may have no good way to verify the identity of the user calling in.
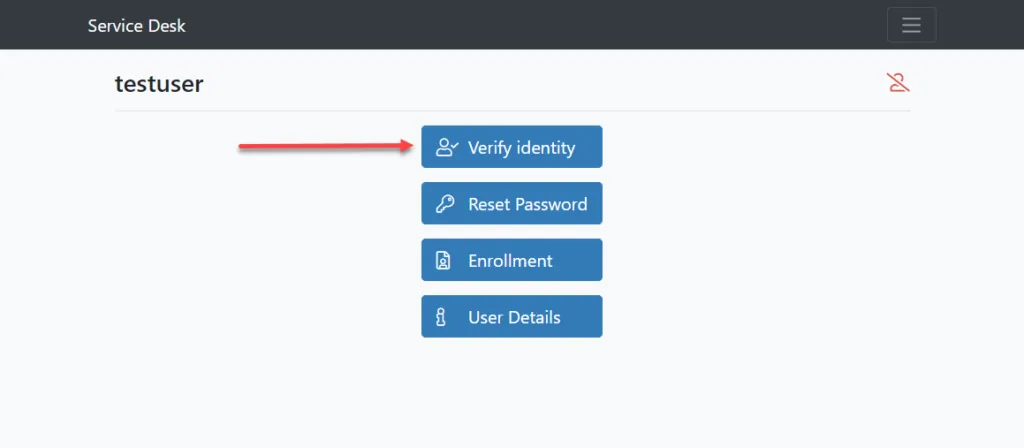
Specops Secure Service Desk provides a solution that allows helpdesk technicians to provide assistance to end users via human interaction in a secure way. When working with end users on the phone, service desk technicians can use the Secure Service Desk solution to verify their identity by enforcing the use of the identity services the end user has enrolled with. A mobile code linked to the user’s account in Active Directory is triggered by the helpdesk technician and sent to their mobile phone. In this way, identity can be safely identified.
Below, a helpdesk technician is triaging a user account issue and has the ability to verify the identity of the remote worker.
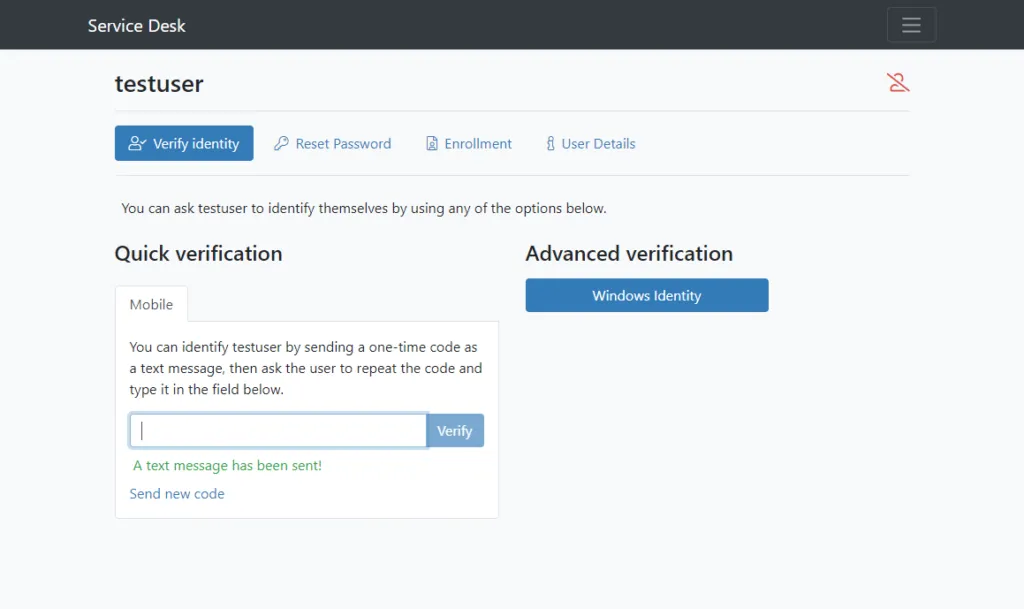
A one-time code is sent to the end user. The end user must repeat the code they receive back so the identity can be verified.
Wrapping Up
Unlocking Active Directory accounts that have been locked is a common process that is generally handled by IT support staff on a daily basis. End user account lockouts are common and are the result of attempting to login with the wrong password too many times. The account lockout policy that is defined in Active Directory specifies the threshold which triggers the account lockout.
Using Active Directory Users and Computers or by using PowerShell, helpdesk technicians can easily unlock an account that has been locked out due to the account lockout policy. However, with many workers now working remotely, account lockout triaging over the phone with the helpdesk opens up security risks related to verifying the end user’s identity. An attacker posing as a valid end user could call the helpdesk and request a password be reset. Using a solution like Specops Secure Service Desk effectively eliminates this possibility and forces the end user to verify their identity before a password reset operation can take place.
(Last updated on April 30, 2025)


