Balancing security hygiene with user experience is an ever-evolving challenge. While traditional security wisdom has long mandated frequent password rotations, modern authentication frameworks (anchored by MFA, risk-based access, and continuous monitoring) have called those rigid schedules into question. In... Read More
Blog
The countries experiencing the most ‘significant’ cyber-attacks
Over the last decade, cyber security has rapidly become a concerning problem. Rightfully so, given how a cyber-attack can compromise an organisation’s key functions and processes within a matter of seconds, exposing sensitive data to opportunistic criminals. The impact... Read More
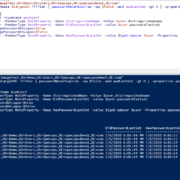
What’s Your Score? New Executive Summary Reports Available in Specops Password Auditor
Today’s release of Specops Password Auditor makes it easier for you to get sign-off on your password security project. “The IT admins we talk to understand the need for fixing the password vulnerabilities in their Active Directory environments,” said... Read More
How to get decision makers to sign-off on your password security project
While IT administrators often innately understand the cost of not addressing a cybersecurity project, it can be hard to get non-IT management to understand why certain projects should be prioritized. In their July 2018 survey, Spiceworks and AT&T found... Read More
Device encryption and compliance
Most companies want to protect data at rest on devices that are susceptible to theft. This will ensure that the data is inaccessible even if the hard drive is removed and replaced in another machine. Yet, lost and stolen... Read More
Common mistakes with endpoint encryption
Endpoint encryption is one of the cornerstones to securing data but it can introduce new challenges which can result in costly mistakes. Encryption is the process of changing information to make it unreadable without a proper authentication key. Administrators... Read More
Survey reveals the UK business sectors most lacking in cyber security training
Even before the Coronavirus outbreak, cyber security has always been one of the most challenging issues for business owners to grapple with – large and small. As cyber threats continue to rise, it’s no wonder that recent stats allude... Read More
Specops Password Reset price
Do you need a self-service solution to enable employee password resets in Active Directory? You are likely familiar with the cost-savings, usability, and security benefits of our password reset solution, now you need to know how much it costs.... Read More
Which authentication tools are users most comfortable with?
Authentication is the first line of defense in any organization’s cybersecurity strategy, but not all authentication tools offer the same level of security, convenience, or scalability. From traditional passwords to advanced biometric and adaptive authentication, businesses must carefully choose... Read More
These password breaches highlight the employee password reuse problem
Today, we’ve released the latest update to the Specops password list, a service that protects organizations from the use of known breached passwords in Active Directory. “Today’s update further supports our commitment to making the Specops Breached Password Protection... Read More