This website uses cookies to ensure you get the best experience on our website. Learn more
How to get decision makers to sign-off on your password security project
Table of Contents
While IT administrators often innately understand the cost of not addressing a cybersecurity project, it can be hard to get non-IT management to understand why certain projects should be prioritized.
In their July 2018 survey, Spiceworks and AT&T found 60% of C-Level Execs believe current solutions keep them completely or very safe versus only 29% of IT pros.
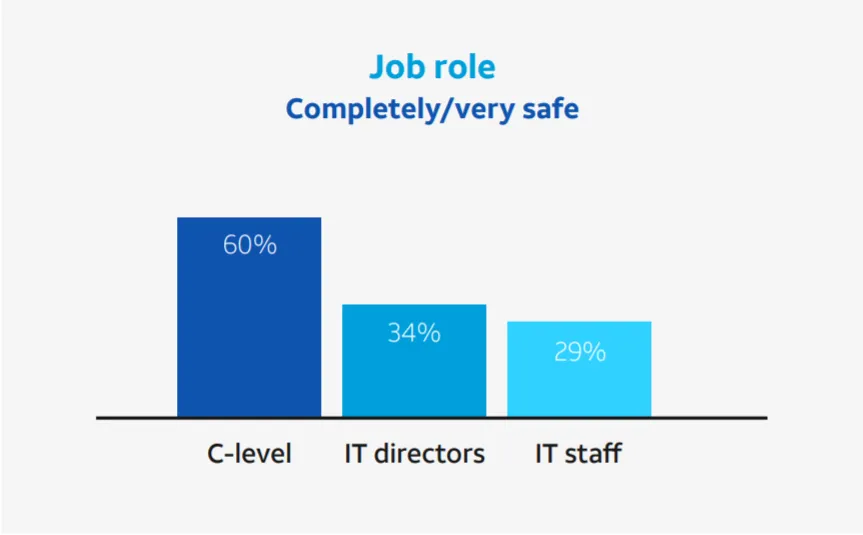
Additionally, just 53% of IT decision-makers felt business leaders understand the importance of security in all aspects of the business—and for those organizations with in-house-only security management, it was just 39%.
Executives can view cybersecurity projects like insurance policies – trying to get by with “enough” and not too worried about the consequence of not doing more.
So how can an IT administrator break through this perception?
There are a few tactics that IT departments have taken to successfully secure budget for their cybersecurity or password security projects.
- Introducing fear
- Making the business case
- Outlining compliance requirements
- Increasing peer pressure
Let’s take a look at how to use each of these.
Fear
When we talk about introducing fear as a tactic for getting a password security project approved, we’re not suggesting creating unreasonable fear.
The reality of what could happen if a particular cybersecurity vulnerability is not taken care of is a scary one.
What’s one of the scariest scenarios for your organization? Are you a hospital whose compromised system could mean patient deaths? Are you an investment firm whose trades would be frozen? Are you a business with a confidential merger in the works whose competitive edge would be lost if word got out?
Combine this with the how easy it can be to break in. No hacking needed – with easily accessible lists of billions of common or compromised passwords, hackers don’t have to hack to break in. Akamai, an internet infrastructure firm, found nearly 30 billion documented credential stuffing attack attempts in 2018 .
The most effective who use this tactic also introduce specifics from your own environment to drive the point home. Take the scariest scenario and then show your decision maker how easy it would be for an attacker to gain access to exactly that. Then drive home how common these attacks are.
Business Case
Another tactic that can help is turning the password vulnerability problem into a financial one.
Not sure how to articulate the cost of a possible breach? From lost business to regulatory fines and remediation costs, data breaches have far reaching consequences. The Ponemon Institute found that the average total cost of a data breach was USD $3.92 million in 2019.
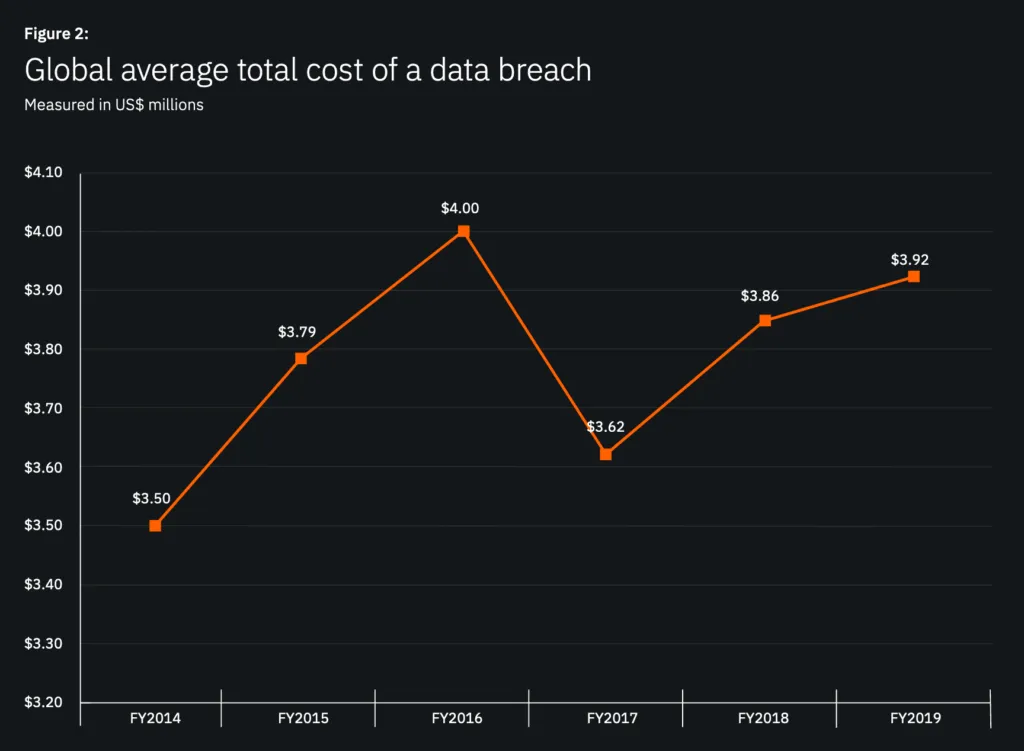
That average total cost was higher if your company was in the United States ($8.19 million) or in the healthcare industry ($6.45 million).
Of course, that’s before you factor in the harder to estimate costs including the impact on your company’s reputation, trust in the brand, or other competitive losses.
Compliance
Some decision makers may be more risk-friendly until it comes to compliance needs driven by regular audit or supply chain requirements.
Start with outlining which set of standards you are legally required to comply. Whether it’s NCSC, NIST, PCI, or something else.
Then outline the specifics of how you are not currently in compliance and how your project can help fulfill that requirement.
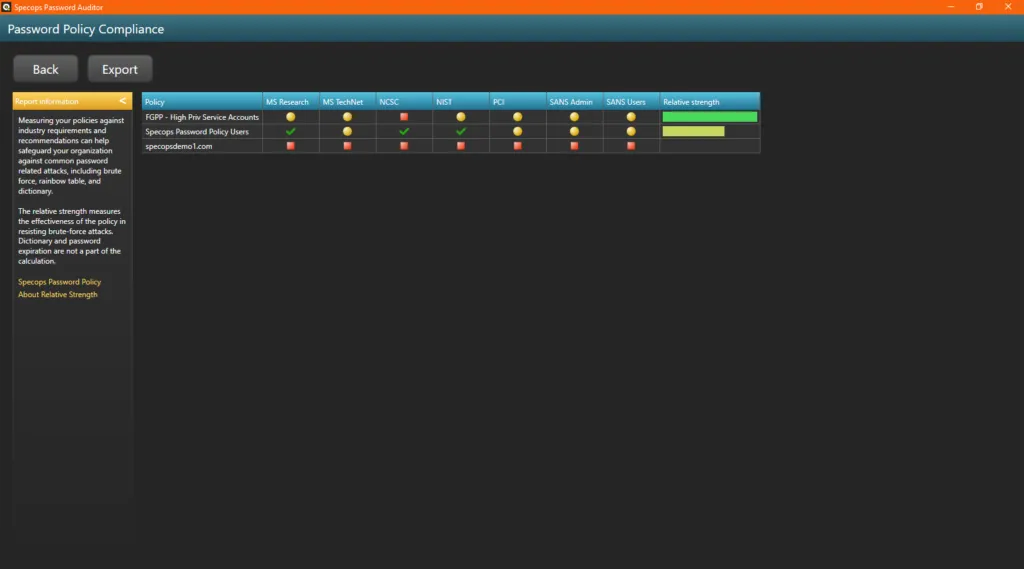
Specops Password Auditor has a great compliance report that makes this analysis part easy for your password security projects.
Peer Pressure
If all else fails, peer pressure can be effective.
How much of your IT budget is devoted to security? Does it match up with your industry? If not, sharing what your peers are spending could help you in making the case for your project.
Gartner noted in 2019 that across industries, average spending on cybersecurity is 5% to 8% of the overall technology budget. In manufacturing, 2% to 4% of the budget is average, though other sectors spend much more. Financial-services firms, for example, spend 10% to 15% of their information-technology budgets on cybersecurity.
Make It Real
Combining the above tactics with some real metrics on how your organization’s password vulnerabilities fair will take this conversation from a theoretical one to a more pressing one.
Find out in minutes how many of your organization’s password are weak or known to be compromised by running your own Specops Password Auditor scan.
Specops Password Auditor is a free read-only tool that scans your Active Directory for password-related vulnerabilities. The results include several interactive reports for you to explore as well as an exportable executive summary PDF report you can share with decision makers who may not share your technical background.
Have you run your (free) Specops Password Auditor scan yet? Find out what your password vulnerability score is today: https://specopssoft.com/product/specops-password-auditor/
(Last updated on September 30, 2024)
