This website uses cookies to ensure you get the best experience on our website. Learn more
SolarWinds hack explained: Weak password “solarwinds123” cause of SolarWinds Hack
When you look at many of the high-profile breaches that have taken place in recent years, many of them had a common denominator – weak or compromised passwords. Weak passwords are easily compromised and can lead to significant breach events that can disrupt the operations of an entire organization, including ransomware attacks, supply chain attacks, and many others. In addition, users may choose passwords that have already been breached. For example, a high-profile breach and cyberattack that made headlines at the end of 2020 was the SolarWinds attack, a sophisticated supply chain attack with tremendous fallout. According to Microsoft Corp President Brad Smith, the SolarWinds attack is “the largest and most sophisticated attack the world has ever seen“. A breached password may have played a part in the massive cybersecurity incident involving SolarWinds.
What is SolarWinds?
So, what is SolarWinds? SolarWinds is a software company that specializes in systems and network management and monitoring tools. Many of these are used in systems and network management across many enterprise organizations.
What is SolarWinds Orion?
The most popular of these tools produced by SolarWinds is the Orion Network Management System (NMS). SolarWinds Orion is a fully-featured solution that has many capabilities allowing IT admins to monitor, manage, and control servers, network devices, workstations, Software-as-a-Service (SaaS), hybrid, and other infrastructure in a single management console. According to SolarWinds, Orion has the following features:
- It can allow NPM users to connect with and correlate NetFlow, configuration, application, server, and virtual infrastructure data to help resolve complex hybrid network performance issues
- It helps to perform root cause analysis
- Provides shared messaging, alerting, and troubleshooting insights between systems
Being an NMS solution, Orion houses credentials and connection information for business-critical and sensitive infrastructure. It means it is a central point of compromise for an attacker. If the solution is successfully compromised, any system the NMS can interact with, manage, configure, and control, attackers can also.
The SolarWinds Supply Chain Attack
The news of the SolarWinds attack came on the heels of information from Reuters about the U.S. Treasury Department being compromised as attackers had infiltrated internal email traffic. In the initial reports, the U.S. government detailed it believed Russia to be behind the attack. It is also believed the attack was closely related to the attack on FireEye, a well-known cybersecurity company that has contracts with the government and many commercial contracts.
The SolarWinds supply chain attack was carried out by a malicious update from one of SolarWind’s own servers. The update was signed with a legitimate digital certificate bearing the SolarWinds name. The update containing the legitimate SSL certificate from SolarWinds points to a supply chain attack. However, it appears the certificate itself was not compromised as, again, it was a legitimate certificate.
However, it does indicate the threat actors were deploying the malicious update through SolarWind’s own channels. It is where things get a bit unclear as to the source of the compromise. According to SolarWinds, they believe their build environment was compromised. The following statement from SolarWinds details this information:
Based on its investigation to date, SolarWinds has evidence that the vulnerability was inserted within the Orion products and existed in updates released between March and June 2020 (the “Relevant Period”), was introduced as a result of a compromise of the Orion software build system and was not present in the source code repository of the Orion products. SolarWinds has taken steps to remediate the compromise of the Orion software build system and is investigating what additional steps, if any, should be taken. SolarWinds is not currently aware that this vulnerability exists in any of its other products.
SolarWinds currently believes that:
- Orion products downloaded, implemented, or updated during the Relevant Period contained the vulnerability;
- Orion products downloaded and implemented before the Relevant Period and not updated during the Relevant Period did not contain the vulnerability;
- Orion products downloaded and implemented after the Relevant Period did not contain the vulnerability; and
- Previously affected versions of the Orion products that were updated with a build released after the Relevant Period no longer contained the vulnerability; however, the server on which the affected Orion products ran may have been compromised during the period in which the vulnerability existed.
SolarWinds Compromised password
Another interesting development in the search for how attackers could introduce the supply chain compromise was the discovery of a compromised SolarWinds password existing on a private Github repository from June 2018 to November 2019. An intern working for SolarWinds had set the password solarwinds123 on an account that was interestingly granted access to the company’s update server.
It has not been made evident whether the breached password played a part in the supply-chain attack affecting some 18,000 businesses with the compromised version of the Orion security platform. However, it is difficult to dismiss the possibility of the compromised password playing into the supply chain attack at some point.
One thing is clear, regardless of the exact connection between the breached credentials and the supply-chain attack, compromised credentials introduce tremendous risk in an organization and must be avoided at all costs.
Bolster Active Directory passwords with Breached Password Protection
Active Directory is arguably the most commonly used Identity and Access Management (IAM) solution used in the enterprise today. Organizations have been using Microsoft Active Directory for decades to secure and grant access to internal and even external resources. In addition, many businesses are using it as the source of Single Sign-On (SSO) to federate access to external third-party services and solutions. The weaknesses inherently found in Active Directory for protecting passwords extend to any solution that uses AD as a source for SSO.
However, Active Directory is showing its age in protecting against modern threats as it lacks the tools and features allowing businesses to protect against threats such as breached passwords. In reality, Active Directory password policies have not changed in decades, offering the same basic password policies since Windows Server 2000. Below is an example of Group Policy settings on a Windows Server 2022 server, the latest Windows Server available from Microsoft.
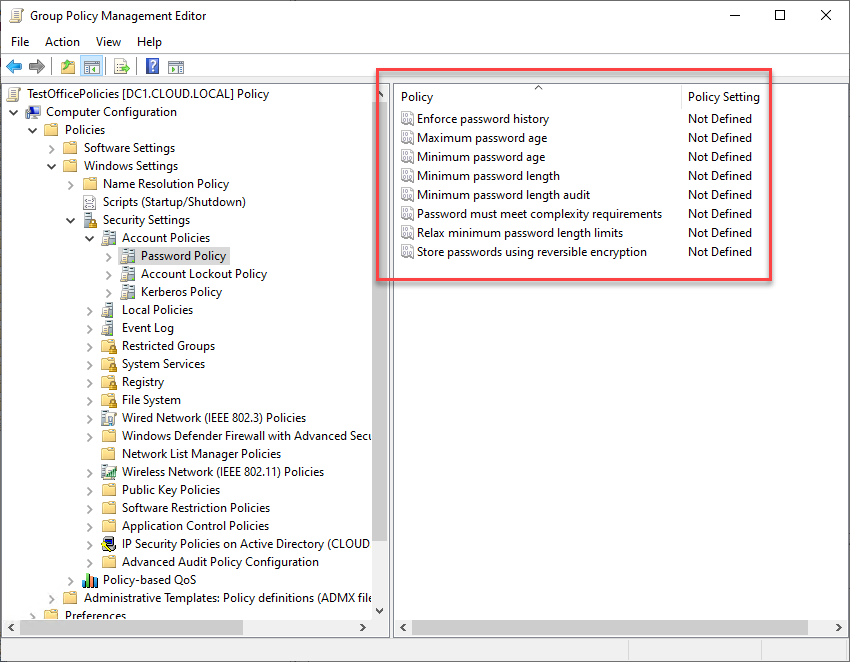
IT admins are challenged to protect user passwords against such threats as:
- Incremental passwords
- Complex but easily guessable passwords
- Breached passwords
- Passwords relevant to the business or business name
Specops Password Policy is a robust solution that integrates with existing Active Directory Group Policies, adding modern cybersecurity features that help protect passwords from being breached. Specops Password Policy adds Breached Password Protection to Active Directory. It allows IT admins to find all breached passwords configured in Active Directory and prevent end-users from choosing breached passwords when they set a new password for their account.
With Specops Password Policy, organizations get continuous breached password protection. Specops employs honeypots worldwide to gather information about accounts attackers are targeting “right now.” This information is used to update the Breached Password Protection continuously, and the billions of passwords in the Specops breached password database.
Specops Password Policy with Breached Password Protection provides visibility to breached passwords and allows IT admins to remediate the situation quickly in situations where passwords have been exposed. Note the following features:
- Block commonly compromised passwords
- Prevent more than 4 billion compromised passwords with Breached Password Protection, including known breached lists as well as passwords being used in attacks happening right now
- Find and remove compromised passwords in your environment
- Informative end-user client messaging at failed password change reduces calls to the helpdesk
- Dynamic feedback at password change with the Specops Authentication client
- Length-based password expiration with customizable email notifications
- Block user names, display names, specific words, consecutive characters, incremental passwords, and password reuse
- Granular, GPO-driven targeting for any GPO level, computer, user, or group population
- Passphrase support
- Over 25 languages supported
- Allows using regular expressions to filter passwords
Learn more about how Specops Password Policy with Breached Password Protection can help you secure passwords in your environment here: Specops Password Policy with Breached Password Protection
(Last updated on August 19, 2022)
Related Articles
-
Ransomware Attacks 101 – from Wannacry to Darkside
Think of ransomware attacks as virtual kidnapping. Ransomware actors use encryption to hold your devices’ functions and files hostage or lock you out of your system. Then they request a ransom for its release. These actors are mostly motivated by financial gain, like kidnappers. However, paying a ransom doesn’t guarantee you get some or all…
Read More -
Ransomware Prevention Best Practices
A thriving industry of holding data hostage has emerged out of the malicious software known as ransomware. The FBI’s Internet Crime Complaint Center (IC3) states in its Internet Crime Report for 2020 that it received a record number of ransomware complaints that year. Attributing the rise in cybercrime to the organizational chaos caused by the…
Read More -
Block These Recently Leaked VPN Passwords to Prevent Ransomware Attacks [new data]
Worried about ransomware attacks? Recent attack news indicates you should be looking to secure your VPN connections. Last week, we learned that thousands of Fortinet VPN passwords had been leaked on the dark web by a former ransomware operator. The Specops research team obtained the leaked data and is sharing the results of their analysis….
Read More


