This website uses cookies to ensure you get the best experience on our website. Learn more
Password Policy Compliance Report in Specops Password Auditor
Table of Contents
Organizations looking to evaluate how well their existing password policies measure up against different compliance standards may benefit from running a free scan with Specops Password Auditor. One of the reports Password Auditor provides is the Password Policy Compliance report.
In this post, we’ll walk through what the report looks like, and what the scoring indicators mean.
What the Password Policy Compliance report looks like
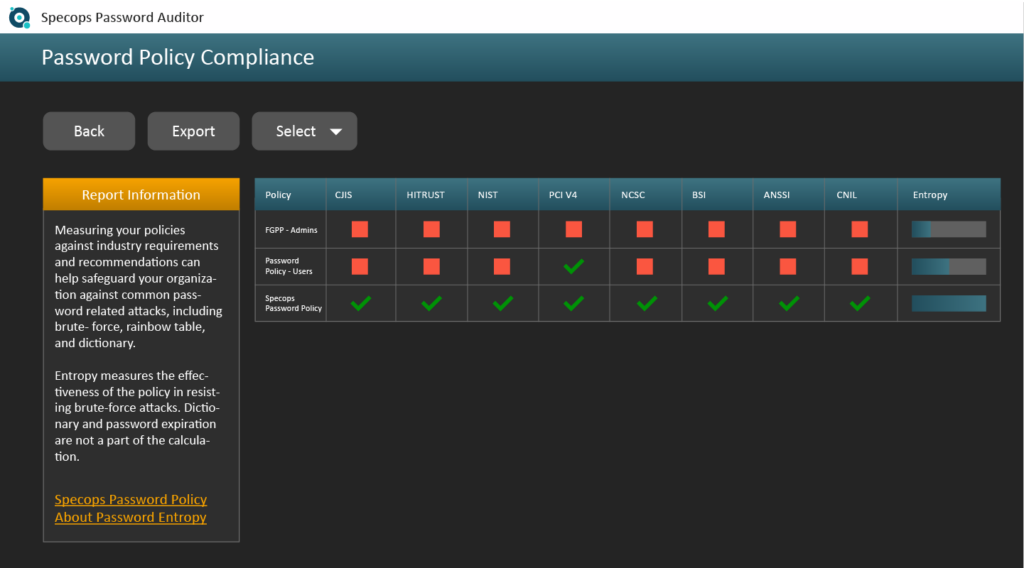
The Password Policy Compliance report in Specops Password Auditor provides an overview of the policies in your Active Directory (or the part of your AD you defined at the start of your scan). Password Auditor will provide results for the Default Domain Password Policy, any Fine-Grained Password Policies , as well as any Specops Password Policies (if installed).
Red, Yellow, Green
The table provides an indicator of how compliant each password policy is against a set of well-known regulatory and industry standards:
- Red = non-compliant. This means the policy did not meet any of the password requirements outlined by the standard.
- Yellow = partially compliant. This means the policy meets at least one but not all of the password requirements outlined by the standard.
- Green = full compliant. This means the policy meets all of the password requirements outlined by the standard.
Entropy
The entropy column is not specifically related to the outlined compliance standards. Instead, it is a measure of how “strong” the passwords allowed by the different policies are. You can read more about the entropy calculation we use.
What are the different compliance standard requirements and recommendations?
The Password Policy Compliance report gives an overview of how your password policies compare against the following standards:
While there is some overlap in what each standard requires, no two are exactly the same. Below you can find the details of the standards we’re using to provide the red/yellow/green score in the table.
CJIS
The scores in the CJIS column are measured against the basic password standards outlined here:
- Minimum length = 8
- Maximum age = 90 days
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords = Yes
- Password history = 10
- Disallow incremental passwords = Yes
If complying with CJIS recommendations is on your list, you may also be interested in our CJIS password policy requirements article.
HITRUST
The scores in the HITRUST column are measured against the HITRUST recommendations outlined here:
- Minimum length = 8
- Maximum age = 90 days
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords = Yes
- Password history = 4
- Disallow incremental passwords = Yes
- Complexity = 2 of digit, lower, special
NIST
The scores in the NIST column are measured against the recommendations outlined here:
- Minimum length = 8
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords: Yes
- Disallow incremental passwords: Yes
If complying with NIST recommendations is on your list, you may also be interested in our NIST password standards article.
PCI V4
The scores in the PCI column are measured against the recommendations outlined here:
- Minimum length = 12
- Maximum age = 90 days
- Use passphrase = Yes
- Password history = 4
- Complexity = digit, lower
The PCI requirements do not speak to blocking the use of compromised passwords like what is possible with a solution like Specops Password Policy with Breached Password Protection.
If complying with PCI V4 recommendations is on your list, you may also be interested in our What’s new in PCI DSS V4.0 article.
NCSC
The scores in the NCSC column are measured against the recommendations outlined here:
- Minimum length = 8
- Use passphrase = Yes
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords: Yes
If complying with NCSC recommendations is on your list, you may also be interested in our How to configure the NCSC password list in AD article.
BSI
The scores in the BSI column are measured against the recommendations outlined here:
- Minimum length = 8
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords = Yes
- Password history = 4
- Complexity = 2 of digit, lower, special, and upper
If complying with BSI recommendations is on your list, you may also be interested in our German Federal Office for Information Security password guidance article.
ANSSI
The scores in the ANSSI column are measured against the recommendations outlined here:
- Minimum length = 15
- Use passphrase = Yes
- Disallow passwords from dictionary = Yes
- Disallow compromised passwords = Yes
- Password history = 4
- Complexity = 3 of digit, lower, special, and upper
CNIL
The scores in the CNIL column are measured against the CNIL recommendations outlined here:
- Minimum length = 12
- Disallow compromised passwords = Yes
- Complexity = Lower, upper
Next Steps
After running the Specops Password Auditor scan, you will see what policies are compliant with the password policy standards that are important to your organization. Depending on what your results look like, you might want to take action and craft a plan to update your policies.
If you are trying to comply with more modern password policy recommendations, you might want to look at a tool like Specops Password Policy with Breached Password Protection. The solution enables you to check Active Directory passwords against a list of compromised passwords.
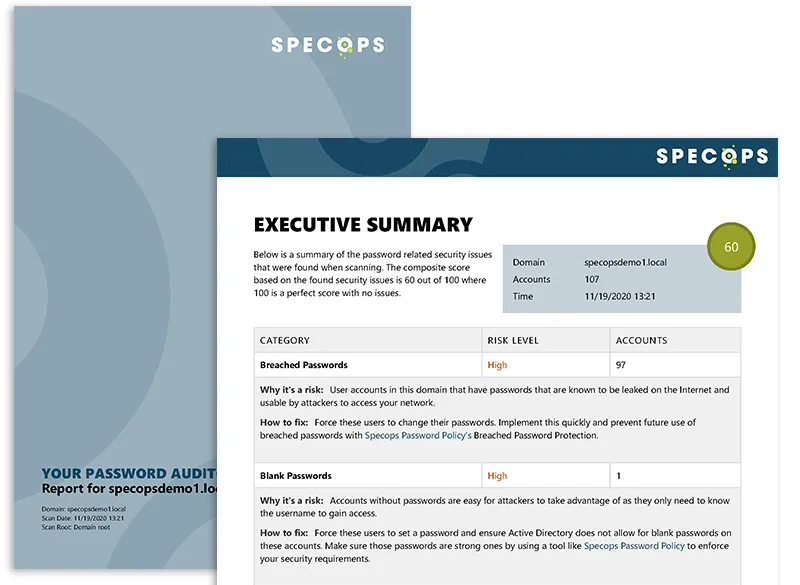
Need help advocating for budget or sign-off? Try exporting your results to PDF within Specops Password Auditor. That PDF is an Executive Summary that summarizes the problem for non-technical colleagues or those who didn’t run the scan themselves.
(Last updated on April 8, 2025)