This website uses cookies to ensure you get the best experience on our website. Learn more
Guide to NCSC’s Cyber Essentials password policy compliance
Table of Contents
Recognized as the authoritative voice on information security in the UK, the National Cyber Security Centre (NCSC) is the UK’s weapon in securing IT. The NCSC consolidates and replaces existing expertise, and indicates the prioritization of cybersecurity on the national agenda. The NCSC’s approved accreditation scheme, Cyber Essentials, provides a standardized baseline for cyber security policies, controls, and technologies. Cyber Essentials is mandatory for government contracts that involve handling personal information, or provisioning certain products and services.
Passwords play an important role in the Cyber Essentials scheme as they are a common means of authenticating true users, while preventing unauthorized access. Two of the five controls in the UK Government’s Cyber Essentials scheme address password security requirements directly. The controls are designed to defend against common cyber attacks, such as phishing, and manual/automated password guessing. We’ll explain what you need about Cyber Essentials and how you can make sure your password policy is secure and compliant.
What is Cyber Essentials and its five key controls?
Cyber Essentials is a government-backed, industry-supported scheme designed to help organizations protect themselves against common cyber threats. The scheme focuses on five key controls:
- Firewalls: Ensuring that only safe and necessary network services are allowed.
- Secure configuration: Ensuring that systems are configured in the most secure way for the needs of the organization.
- User access control: Ensuring that only those who should have access to systems have access and at the appropriate level.
- Malware protection: Ensuring that virus and malware protection is installed and up to date.
- Patch management: Ensuring that the latest supported version of applications is used and all necessary patches are applied.
Why should UK IT teams care?
Cyber Essentials is not just a set of guidelines; it’s a roadmap to a more secure digital future. By adhering to these guidelines, UK IT practitioners can significantly enhance their organization’s cybersecurity posture, build trust, and stay ahead of the curve in an ever-changing digital landscape. Whether you’re a small business owner or a CISO at a large corporation, investing in Cyber Essentials is a smart move. It’s time to prioritize cybersecurity and make sure your organization is protected against the most common threats.
Enhanced security: By implementing the Cyber Essentials controls, organizations can significantly reduce their vulnerability to common cyber attacks. This proactive approach helps safeguard sensitive data and maintain operational integrity.
Compliance and trust: Adhering to Cyber Essentials demonstrates a commitment to cybersecurity best practices. This can enhance trust with customers, partners, and stakeholders, who increasingly prioritize data security when choosing service providers.
Cost-effective protection: The measures outlined in Cyber Essentials are designed to be cost-effective and straightforward to implement. This makes it accessible for organizations of all sizes, from small businesses to large enterprises.
Regulatory compliance: Many industries have specific regulatory requirements for cybersecurity. Meeting Cyber Essentials guidelines can help organizations comply with these regulations, avoiding potential fines and legal issues.
Competitive advantage: In an era where cybersecurity is a top concern, organizations that can demonstrate robust security measures have a competitive edge. Cyber Essentials certification can be a differentiator in the market.
Over the years, a few revisions have been made to the Cyber Essentials scheme, which we’ll cover in this blog.
What were the changes to Cyber Essentials in 2022?
The 2022 update to the Cyber Essentials Certification introduced several significant changes:
Cloud services: All cloud services, including Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS), must now be included in the scope of Cyber Essentials.
Passwords and two-factor authentication (2FA): From January 24, 2022, all administrative users of cloud services must have multi-factor authentication (MFA) applied. By 2023, all standard user accounts will also need MFA. In the meantime, user accounts require either a 12-character password or an 8-character password with technical controls to deny bad passwords.
Device declaration and BYOD: All devices, including Bring Your Own Device (BYOD), must be declared and have all controls applied, including declaring the make, model, and operating system of devices.
Thin clients: From 2023, all thin clients must be supported and receive security updates.
Remote workers: If a home network uses an ISP-provided router, it is out of scope. However, if the organization provides a router, it is in scope. Homeworker computers must have an active software firewall.
Routers and firewalls: These must have a minimum 8-character password and either 2FA or login restrictions to internal addresses or specific external IP addresses.
Cyber Essentials Plus: Changes include stricter requirements for patching operating systems and applications, and all critical and high vulnerabilities must be remediated regardless of attack vectors. There are also new tests for cloud services, including ensuring all administrator accounts have 2FA enabled.
How will Cyber Essentials be changing in April 2025?
In the upcoming April 2025 revision of the Cyber Essentials guidelines, significant updates are anticipated. Here’s a concise summary of what to expect:
Terminology updates: The guidelines will see a shift in terminology with ‘plugins’ being renamed to ‘extensions’ to better reflect their functionality. Additionally, the term ‘home working’ will be expanded to ‘home and remote working’ to more accurately represent working environments outside of traditional office spaces.
Passwordless authentication: A major addition to the guidelines is the inclusion of passwordless authentication methods. These methods, which include biometric verification, security keys, one-time codes, and push notifications, aim to enhance security by eliminating traditional passwords.
Vulnerability fixes: The term ‘patches and updates’ will be updated to ‘vulnerability fixes’. This change broadens the scope to include all strategies used to address software vulnerabilities, such as patches, updates, registry fixes, configuration changes, and scripts.
For Cyber Essentials Plus, the changes are as follows:
- The term ‘illustrative’ will be removed from the Cyber Essentials Plus test specification document to clarify its purpose.
- The scope of the Cyber Essentials Plus assessment will be required to align with the Cyber Essentials self-assessment and must be verified by the Assessor.
- If the scope of the Cyber Essentials self-assessment does not encompass the ‘whole organization’, the Assessor must ensure that any subsets are properly segregated.
- Assessors are required to confirm that the sample size of devices has been accurately calculated according to the method prescribed by IASME.
- All verification evidence must be retained by the Certification Body for the duration of the certificate’s validity.
These updates aim to enhance the clarity, scope, and security measures of the Cyber Essentials frameworks, ensuring they remain effective tools in the evolving landscape of cybersecurity.
Cyber Essentials password requirements and guidance
The Cyber Essentials password policy guidance is covered in the Secure Configuration and User Access Control key controls. We’ll walk through both here.
What is Secure Configuration?
The objective of Secure Configuration is to ensure that computers and network devices are configured to reduce the level of inherent vulnerabilities. Devices should only provide the service required to fulfil their role. In addition to computers and network device requirements, the Secure Configuration control details password-based authentication. In a shift away from password complexity, the requirements place the technical password burden on systems, as opposed to relying on users following good practices. To achieve the certificate an applicant must fulfil the following (from the Cyber Essentials website – now NCSC):
- Protect against brute-force password guessing, by using at least one of the following methods:
- lock accounts after no more than 10 unsuccessful attempts
- limit the number of guesses allowed in a specified time period to no more than 10 guesses within 5 minutes
- Set a minimum password length of at least 8 characters
- Not set a maximum password length
- Change passwords promptly when the Applicant knows or suspects they have been compromised
- Have a password policy that tells users:
- how to avoid choosing obvious passwords (such as those based on easily-discoverable information like the name of a favorite pet)
- not to choose common passwords — this could be implemented by technical means, using a password deny list
- not to use the same password anywhere else, at work or at home
- where and how they may record passwords to store and retrieve them securely — for example, in a sealed envelope in a secure cupboard
- if they may use password management software — if so, which software and how
- which passwords they really must memorize and not record anywhere
The Applicant is not required to:
- Enforce regular password expiry for any account (we actually advise against this — for more information see The problems with forcing regular password expiry)
- Enforce password complexity requirements
What is User Access Control?
User Access Control ensures user accounts are assigned to authorized individuals only. Access should only be granted to those applications, computers, and networks that are actually required for the user to perform their role. You can reduce the risk of information being stolen or damaged by granting only as much access as needed. This technical control defines requirements of privileged accounts and processes for limiting access. The requirements include the following (from the Cyber Essentials website – now NCSC):
- Have a user account creation and approval process
- Authenticate users before granting access to applications or devices, using unique credentials (see Password-based authentication)
- Remove or disable user accounts when no longer required (when a user leaves the organization or after a defined period of account inactivity, for example)
- Implement two-factor authentication, where available
- Use administrative accounts to perform administrative activities only (no emailing, web browsing or other standard user activities that may expose administrative privileges to avoidable risks)
- Remove or disable special access privileges when no longer required (when a member of staff changes role, for example)
Cyber Essentials certification and accreditation bodies
The overall goal of the Cyber Essentials scheme is to help organizations guard against common cyber threats and show their commitment to cyber security. There are five accreditation bodies that can help with assessment and certification. The following accreditation bodies are listed on the NCSC’s website: APMG, CREST, IASME, IRM and QG Management Standards. The Cyber Essential certification is a stamp of approval that an organisation has put the most critical cyber security measures in place.
For more information about Cyber Essentials certification, check out the FAQ on the NCSC’s website. Remember, Cyber Essentials certification should be renewed annually to remain on the official register of certified businesses.
Build a Cyber Essentials compliant policy
If you are planning for Cyber Essentials accreditation you will need to make sure your password policy is up to the challenge. Shift the password burden away from your users, and place it instead on the technical systems. For example, you could use a password deny list to stop leaked passwords, lock accounts after repeated login attempts, and stop periodic password expirations. You should also limit the number of users who have privileged access, and use those accounts for only the task that is required of them.
A third party tool like Specops Password Policy can significantly aids organizations in complying with Cyber Essentials by making it easy to set up robust password security measures. It integrates seamlessly with Active Directory and continuously scans for over 4 billion unique compromised passwords. The Specops Authentication Client also offers dynamic feedback to users, helping them create stronger passwords, and sends customizable notifications when compromised passwords are detected.
Additionally, it includes compliance templates that align with Cyber Essentials we well as other standards such as NIST, CJIS, NCSC, and ANSSI, ensuring that organizations meet necessary regulatory requirements. These comprehensive features help reduce your attack surface and support effective compliance with Cyber Essentials. Book a free trial of Specops Password Policy and see how it can fit in with your organization.
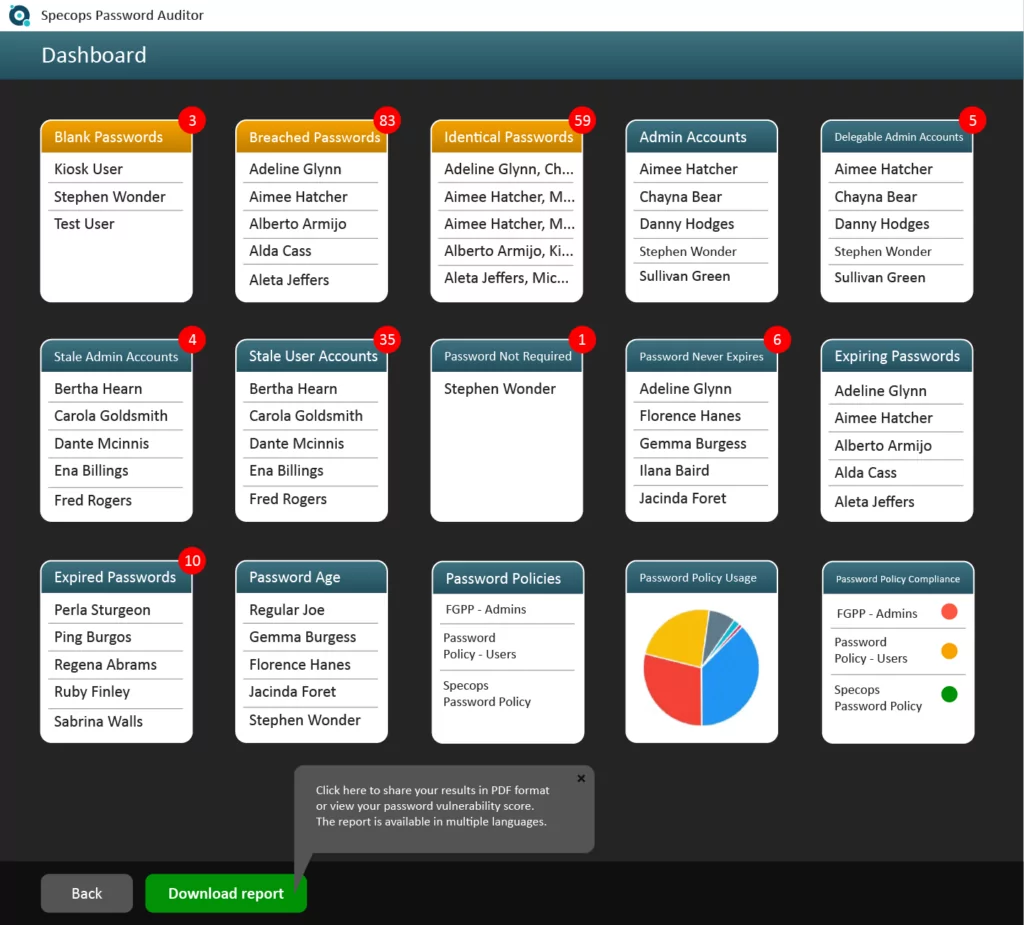
Try our free password auditor tool to detect breached passwords
Specops Password Auditor is a free read-only tool that can find password-related threats in your Active Directory. IT departments use the software to identify accounts using compromised passwords in their organization and the auditor also reports how the password settings in your organization compare with industry standards. Once you sign-up, you will receive a link to the downloadable Setup wizard. The entire installation process can be completed in just a few minutes. Download Specops Password Auditor for free.
(Last updated on April 24, 2025)


