This website uses cookies to ensure you get the best experience on our website. Learn more
CNIL password guidance
Data privacy has become a priority for global businesses due to sweeping regulations such as the General Data Protection Regulation (GDPR). At the same time, other regulatory bodies continue to enforce local data privacy laws. In France, for example, the data protection authority is the Commission nationale de l’informatique et des libertés (CNIL).
The CNIL provides cybersecurity guidance related to collecting, storing, and using personal data. Naturally, securing passwords is an important part of the guidance.
What is the CNIL?
The CNIL is a governing regulatory body that enforces data privacy mandates, including the French Data Protection Act. The French Data Protection Act was put into force in 1978 and has had several amendments to address newer challenges, and to align with the GDPR. Additionally, the CNIL governing body can investigate and sanction organizations based on infringements.
CNIL password guidance
Most business systems need a password to access them. In the guidance found in the Deliberation no. 2017-012 of 19 January 2017 on the adoption of a recommendation relating to passwords, the CNIL provides various Cases related to password use. The recommendations are based on whether or not authentication is solely based on just the password, or if other authentication factors are involved.
- Case no. 1 – Password alone
- Password minimum of 12 characters
- Upper-case letters, lower-case letters, numbers, and special characters
- Case no. 2 – Password and restricting account access
- Password minimum of 8 characters
- Password must include three out of 4 categories of characters (upper-case letters, lower-case letters, numbers, and special characters)
- Case no. 3 – Password and additional information
- Password minimum of 5 characters
- Authentication must involve additional information including information provided on its own account by the data controller or by the person concerned, or any technical parameter that is unique to the computer terminal used by the person concerned (IP address, MAC address, user agent, etc.),
- Case no. 4 – Password and equipment held by the person concerned
- Password should be at least 4 numbers long and can only involve a hardware device held by the person. This includes SIM cards, chip cards, and devices containing an electronic certificate that can be unlocked using a password token
Other important password recommendations from the CNIL include:
- The CNIL recommends that the password be systematically renewed if it is compromised.
- In all cases, the CNIL feels that the user should never be given the password in plain text, especially by e-mail.
- The CNIL recommends that the data controller impose a password-renewal requirement at a relevant and reasonable frequency, which is based in particular on the password complexity required, the data processed, and the risks to which the password is exposed. It also recommends that the data controller enable the persons concerned to change their passwords themselves. In that case, the rules on password creation shall apply.
Meeting the CNIL password guidelines
Businesses typically use Microsoft Active Directory as the means to enforce password policies. However, the default Active Directory password policy is relatively basic. It has no built-in means to easily provision password lists or check for breached passwords in the environment.
Specops Software provides tools that allow organizations to handle password risks. Specops Password Auditor is an exploratory tool that allows companies to gain visibility to passwords used in the environment, including weak passwords, reused passwords, and breached passwords. With Password Auditor, organizations also audit existing password policies and see how these measure up to industry standards.
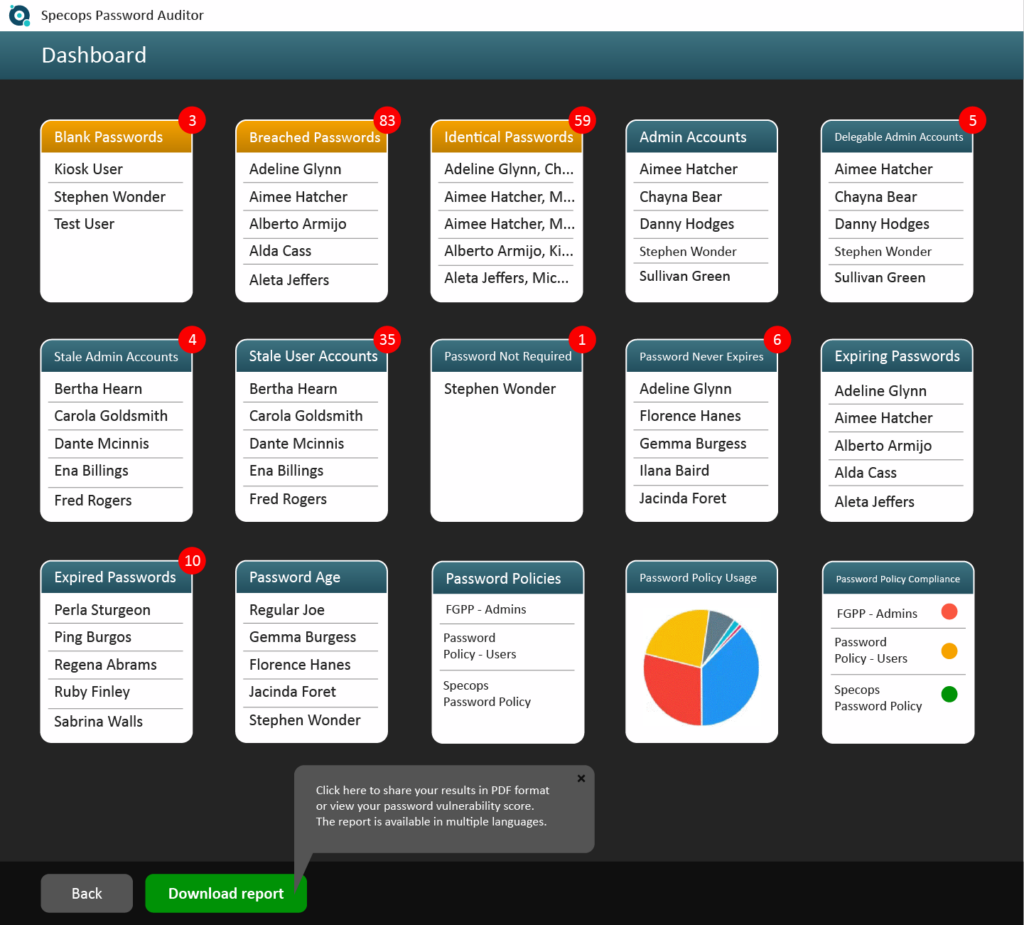
For organizations who want more than information gathering, Specops Password Policy allows organizations to enforce compliance requirements, block leaked passwords, and help users create stronger passwords. It integrates into existing Active Directory Group Policies, allowing businesses to target specific users and computers with dictionary and passphrase settings.
Specops Password Policy provides interesting abilities such as requiring different password change intervals based on the password complexity, custom password dictionaries, and breached password protection. As defined by CNIL, if a password is breached, it should be changed. Specops provides a proactive approach that protects your environment from breached passwords.
Align with the French data protection authority’s password guidance, learn more about Specops Password Policy here.
(Last updated on October 30, 2023)

