This website uses cookies to ensure you get the best experience on our website. Learn more
German Federal Office for Information Security password guidance
Table of Contents
The German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI) is an agency responsible for information security for the German federal government. The BSI is also the central certification body for IT systems. This means that any IT product or system that is to be used by the federal government, must meet the security standards of the BSI.
One of the common pain points for IT security is authentication and the password. What specific guidance does the BSI offer in regards to password security?
BSI password security recommendations
The BSI password security recommendations help organizations achieve a best practice stance for password policies in their environments. Password recommendations can be found in the IT-Grundschutz Kompendium (ORP.4.A23), and include the following:
- The password MUST be so complex that it is not easy to guess
- The password MUST not be so complicated the user is unable to use the password regularly with a reasonable amount of effort
- IT systems or applications SHOULD ONLY prompt you to change your password with a valid reason
- Timed password expiration SHOULD be avoided
- Action MUST be taken to detect and prevent the use of compromised passwords
- Old passwords MUST no longer be used after a password change
Default Active Directory password policies are not enough
The BSI password recommendations align with other high-profile cybersecurity guidance from Microsoft and the National Institute of Standards and Technology (NIST). This guidance includes the recommendation to detect breached or compromised passwords.
NIST Special Publication 800-63B, section 5.1.1.2:
When processing requests to establish and change memorized secrets, verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly used, expected, or compromised. For example, the list MAY include, but is not limited to:
- Passwords obtained from previous breach corpuses.
Native Microsoft Active Directory Domain Services (ADDS) functionality is limited in features. Without third-party password tools, organizations cannot detect breached or otherwise compromised passwords.
Breached Password Protection with Specops Password Policy
Breached password protection is an essential component of today’s password security best practices, and rightfully so. According to the 2020 IBM Cost of a Data Breach report, “stolen or compromised credentials were the most expensive cause of malicious data breaches.”
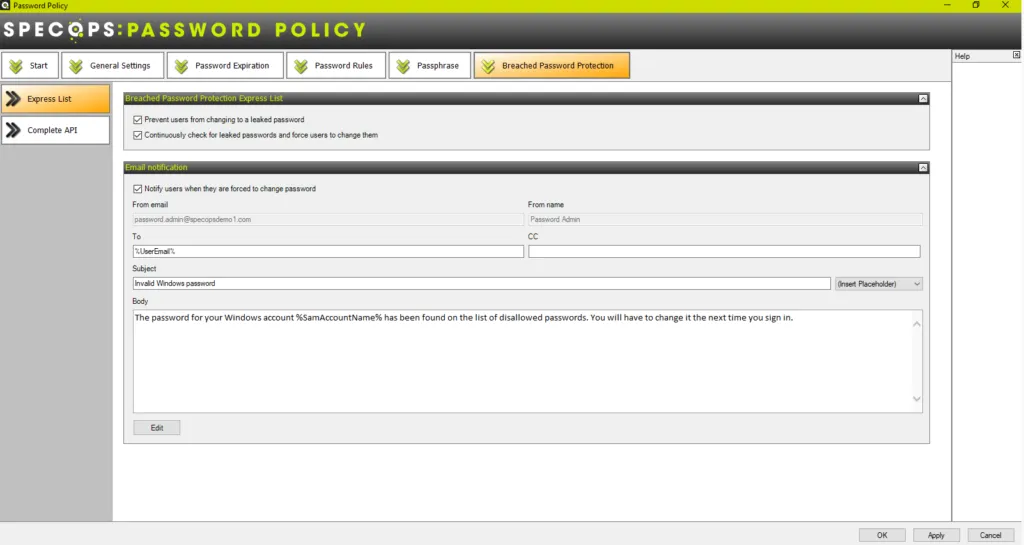
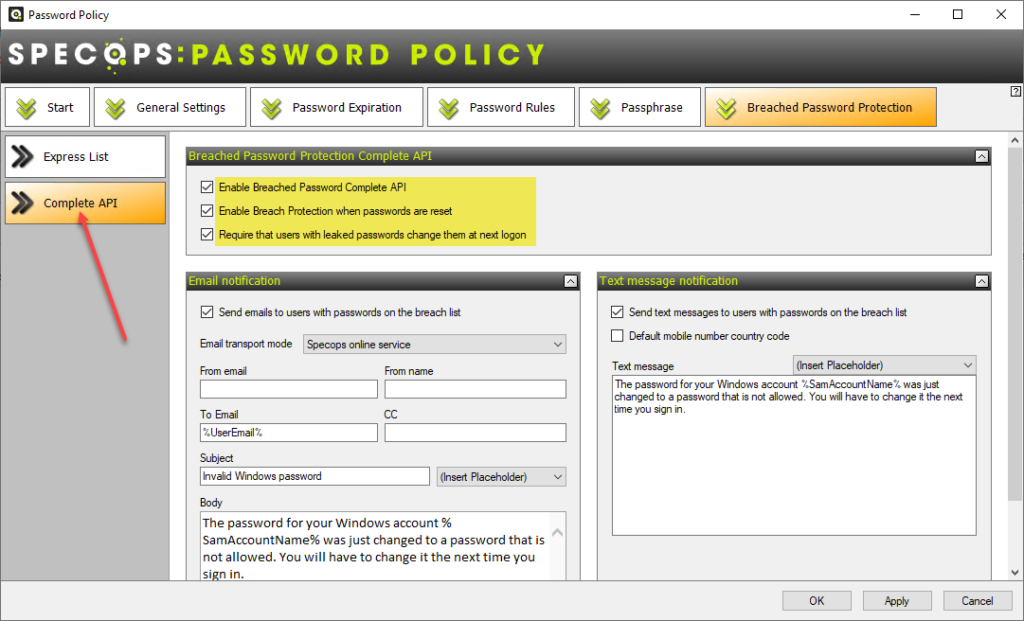
Specops Password Policy is a robust password security solution that enables breached password protection in Active Directory. As you see below, there are two configuration options for preventing the use of compromised passwords:
- Express List – A subset of the Breached Password Protection database that can be downloaded locally and checked. However, in cases where Internet connectivity is limited or not desired, this provides the option of checking a local copy of the breached password database for user password changes
- Complete API – Using the Complete API approach, organizations can have passwords checked against the full Specops breached password database. This option provides the most robust protection, checking passwords against over 4 billion compromised passwords.
Both options prevent users from using a breached password. They also provide the ability to force users to change passwords if the passwords become breached. With the Complete API option, users can optionally receive a text message noting the breach event and the need to change their password.
The Breached Password Protection provided by the Specops Password Policy provides a wealth of other great features to control and enforce password security in Active Directory environments. These include:
- Custom password dictionary lists to help prevent targeted attacks
- Passphrase support
- Blocking the use of character substitutions, keyboard patterns, display names, consecutive characters, incremental passwords, etc.
- Customizable dynamic feedback at password change and informative client messages when a user fails to meet password policy rules, reducing calls to the service desk
- Length-based password expiration with email notifications to encourage the use of longer passwords
- Regular Expressions to further customize requirements
With Specops Password Policy and Breached Password Protection, companies can block over 4 billion compromised passwords in Active Directory. These compromised passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC. Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk.
Learn more about the Breached Password Protection features in Specops Password Policy, and request a fully-featured trial version by contacting us.
(Last updated on September 19, 2024)

