This website uses cookies to ensure you get the best experience on our website. Learn more
Weak Windows passwords blamed for recent rise in Purple Fox attacks
Table of Contents
Purple Fox is malware that was first discovered in 2018 but has seen a recent rise in proliferation as hackers take advantage of a new attack method: weak passwords used over the SMB protocol.
SMB (Server Message Block) is a protocol (mainly) used by Windows computers to communicate with other network devices like printers and file servers. Active Directory users on Windows computers utilize the SMB protocol with their Active Directory password.
Purple Fox first appeared in 2018 using phishing and exploit attack methods – both methods that required some sort of user interaction to initiate. The new SMB attack method is of concern to security professionals because it means that Purple Fox no longer requires user interaction to propagate.
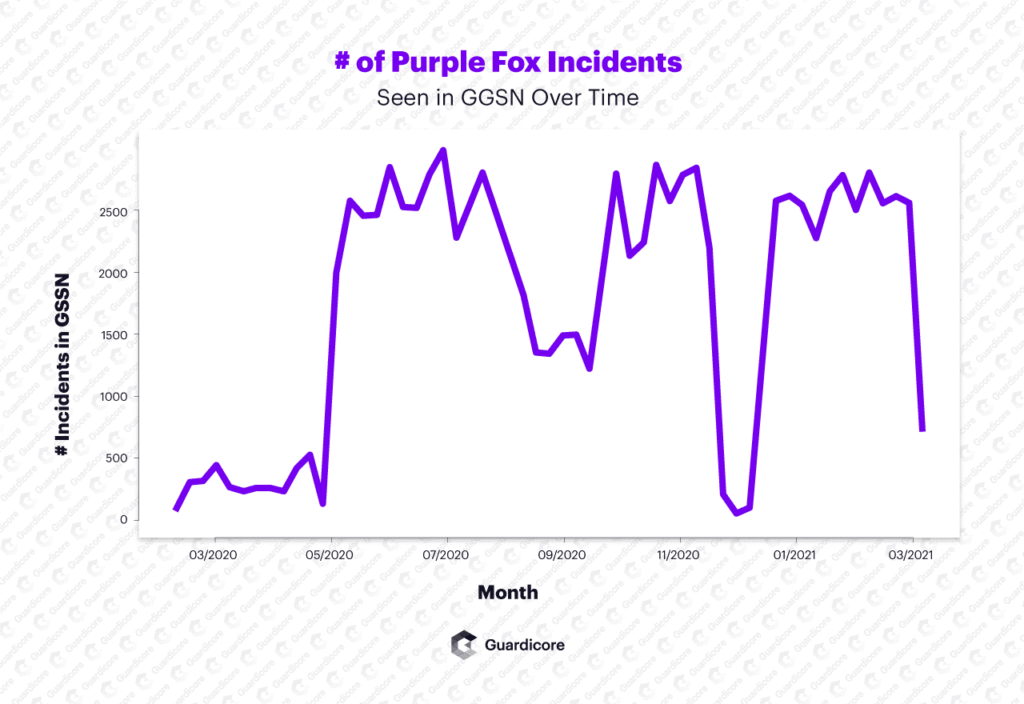
The Specops research team has been collecting data on what the SMB attacks look like using a global honeypot system, including what passwords these attackers are using.
Top 20 Passwords in SMB Attacks
- 123
- Aa123456
- password
- 1qaz2wsx
- 12345678
- a123456
- password1
- abc123
- 111111111
- welcome
- 1234567890
- 111111
- 654321
- 123456789a
- princess
- 1q2w3e4r
- 888888
- dragon
- 112233
- iloveyou
The Specops team analyzed over 250,000 attacks on the SMB protocol over a period of 30 days. “Password” was found used in attacks over 640 times in that period.
“The data tells us that these passwords are weak and again the password is the weakest link in IT security,” said Thorbjörn Sjövold, Head of Research at Specops Software. “Your organization’s weak passwords are a payday waiting to happen for SMB password brute force attackers.”
IT departments can protect against this new attack method by securing their Active Directory passwords with a solution like Specops Password Policy. Specops Password Policy makes it easy for IT admins to enforce stronger passwords that match any complexity requirements, reward users for longer passwords with length-based password aging and prevent the use of known breached passwords with Breached Password Protection.
Find out how many of your organization’s passwords are weak and/or leaked with a free read-only scan by Specops Password Auditor.
(Last updated on November 5, 2024)
