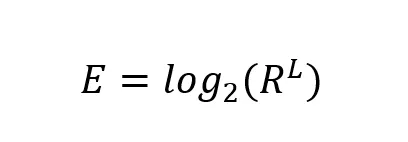This website uses cookies to ensure you get the best experience on our website. Learn more
All About Password Entropy
This article takes a look at the Password Entropy calculation in Specops Password Auditor.
What is entropy?
Entropy is a concept borrowed from information theory. In the password context, entropy can be summarized as: how many guesses would it take to guess a password with brute-force guessing?
In Specops Password Auditor, we calculate the password entropy of your password policies with this formula:
Let’s take a look at what’s in this formula.
To calculate entropy, we need to start with these two measurements
L – The required length of the password
R – The required range of characters
For example, if a password only has to contain lower case letters, R = 26. If the password must contain lower, upper and digits, R = 62 (26 + 26 + 10)
A password space for a password can then be calculated as RL. The password space is a measurement of the total number of possible passwords that can be created using a certain value for L and R. As you can imagine this is a very large number. For example, with L = 10 and R = 62, the password space is 839,299,365,868,340,224. Since such numbers are a bit unwieldy, entropy is defined as the binary logarithm, log2, of this value. The binary logarithm can also be read as the number of bits required to express the number. This leads to the full formula for entropy (E): E = log2(RL).
In the example above with L = 10 and R = 62, entropy comes out to ≈ 60.
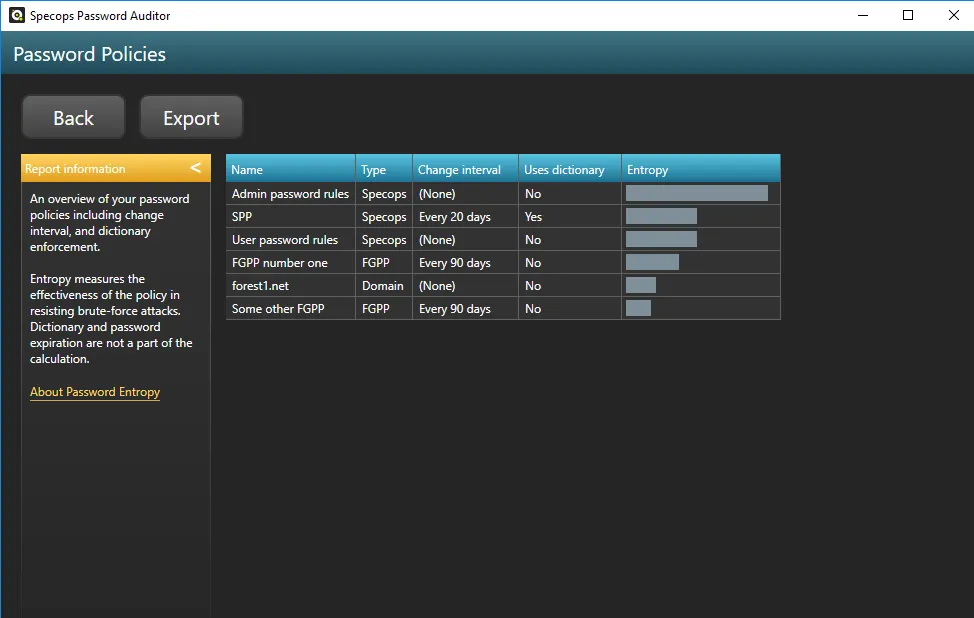
In Specops Password Auditor, we visualize this calculation with bar graphs.
The scale shown in Password Auditor is 1-100. Any entropy score 100 or above is shown as a full bar.
Is entropy enough?
Password entropy, or a difficult to guess password, is one measure of password strength. However, in today’s attack reality, a password policy with a high password entropy score is not enough.
A long and complex password is difficult to guess only if an attacker isn’t using a stolen set of credentials that that password is found on to attack your network with. A strong password is only strong until it is leaked.
In addition to entropy, a strong password policy should also require:
- Breached password check
- Custom dictionary check for tailored attacks
Custom dictionaries can help prevent attacks that are attempting to guess passwords related to your organization (preventing the use of company name, product name, local sports teams, etc.). Breached password lists can help prevent against credential stuffing attacks and are recommended by almost every standard industry body.
Implementing entropy + more
Microsoft alone has some limitations on what it can require in terms of entropy.
| Specops | Microsoft FGPP | |
| 5/5 character types | Yes | Only 3/5 character types |
| Disallow consecutive identical characters | Yes | No |
| Disallow common character types at the beginning | Yes | No |
| Passphrase support | Yes | No |
With a tool like Specops Password Policy, you can pair all of these recommended password security best practices (entropy, custom dictionary, leaked lists) with simple end-user messaging. Specops Password Policy also offers length-based password aging to help reward users for longer (and harder to guess) passwords.
And if you haven’t already run a read-only scan with Specops Password Auditor, you can download it here to find out how many passwords in your Active Directory environment are weak or leaked and more.
(Last updated on September 15, 2023)