This website uses cookies to ensure you get the best experience on our website. Learn more
How to create a fine-grained password policy in AD
Table of Contents
For the first eight years of Active Directory, the only native way of having multiple password policies in your AD forest, was to have multiple domains. When Windows Server 2008 arrived on the scene, Microsoft introduced the concept of fine-grained password policies (FGPP), which allowed different policies within the same domain.
Traditionally, the Default Domain Policy is where the standard password policy settings are configured. It is somewhat strangely done under the Computer Configuration area of that GPO, posing a problem when wanting to apply different password policies to different users. So, to move away from using Group Policy, the concept of a Password Settings Container in AD, and applying the FGPP’s by AD security group, rather than a GPO linked to an OU, was introduced.
The original interface to configure FGPP was horrible. You had to use scary tools such as Adsiedit.msc, or helpful third party tools such as Specops Password Policy. However, with the advent of Server 2012, a different configuration tool (written in PowerShell) was introduced – Active Directory Administrative Center (ADAC), which is what we are going to use to evaluate what FGPP can offer you. We’ll walk through what you can (and can’t!) do with FGPP in AD.
Accessing the Active Directory Administration Center to Adjust Fine-Grained Password Policies
You can find ADAC under the Windows Administrative Tools. Please find here also a detailed guide on how to check password complexity requirements in active directory.
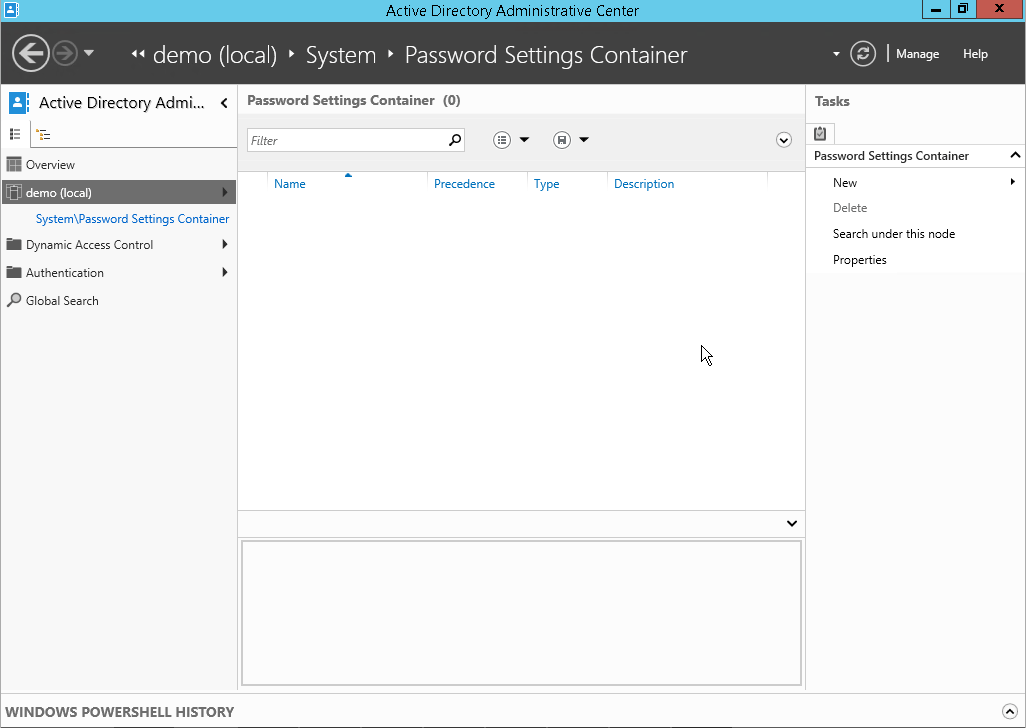
If you have domain admin level privileges, you will see “system\Password Settings Container” underneath your domain name on the left.
If you select that link you will see that you can choose New>Password Settings on the right.
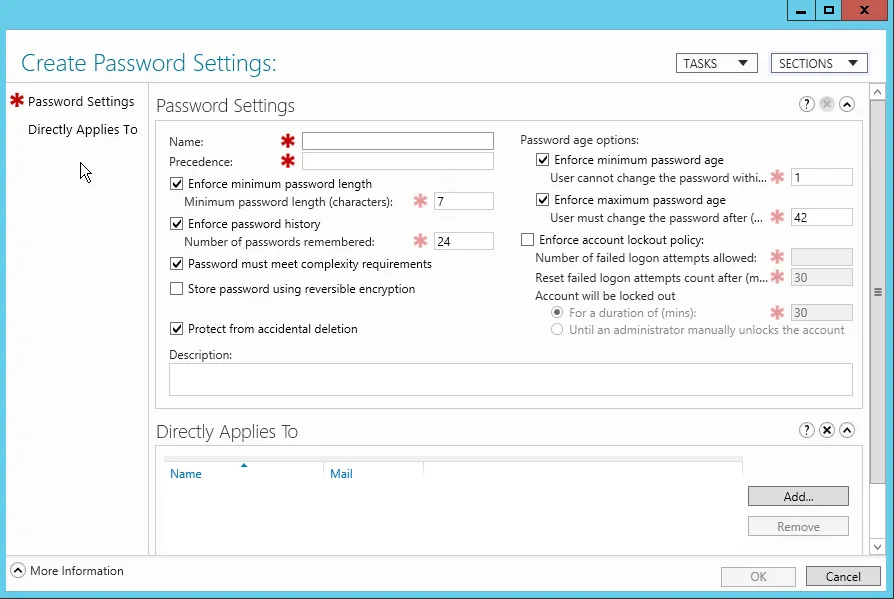
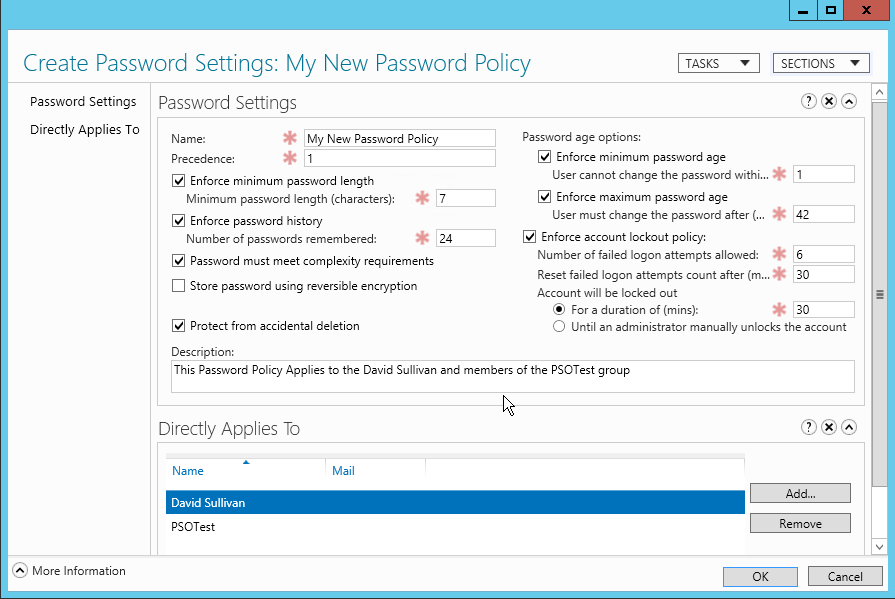
The following configuration interface will be launched.
You have the same basic options in here, as you do in the Default Domain Policy:
- Name – Give it a decent name that reflects the group or individual that this policy will apply to
- Precedence – If there is more than one FGPP that applies to a user e.g. they are in multiple AD groups, then the precedence defines which policy should apply
- Minimum Password Length – All passwords should have a minimum number of characters
- Password history – The number of passwords that should be remembered by AD for each user so that they cannot be reused
- Complexity Required – 3 out of the 5 character types (upper, lower, digits, special and Unicode), must not contain the username
- Store Passwords with reversible encryption
- Protect from Accidental Deletion
- Minimum Password Age – Stops users changing their password multiple times on the same day so that they go past what was set in the Password History field and can re-use the same password again
- Maximum Password Age – When should the password expire
- Lockout Policy – How many times can the user enter the incorrect password before the account is locked out, and how long should they be locked out for
- Directly Applies to – Who should this policy apply to either a User or a Group, you cannot apply it to an OU
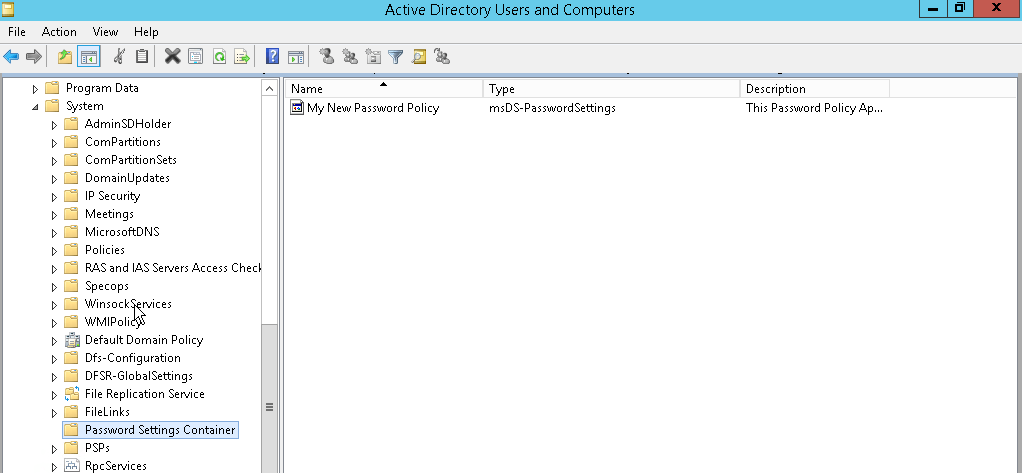
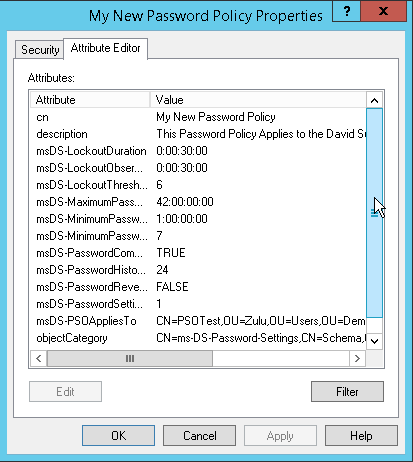
You can find the Password Settings Container in Active Directory Users and Computers.
If you have enabled Advanced Features, you will find it under the System container.
If there is an object in here, you can view its properties and configured settings under the Attribute Editor tab.
As you can see, it is not exactly “fine-grained” password policy. Complexity is either on or off. Interestingly, even Microsoft now regards the complexity settings as anti-security.
Configuring Fine-Grained Password Policies Using Powershell
In Active Directory, you can manage fine-grained password policies (PSOs) using Powershell, though the Active Directory PowerShell module must be installed on our computer in order to do so.
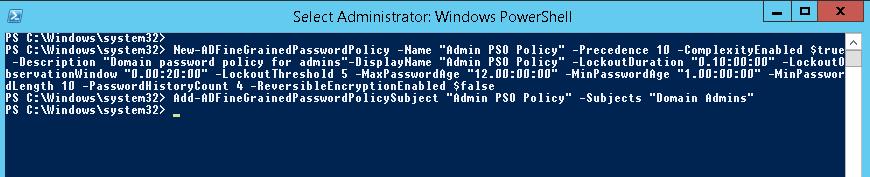
To create a new PSO, use New-ADFineGrainedPasswordPolicy cmdlet:
New-ADFineGrainedPasswordPolicy -Name “Admin PSO Policy” -Precedence 10 -ComplexityEnabled $true -Description “Domain password policy for admins”-DisplayName “Admin PSO Policy” -LockoutDuration “0.20:00:00” -LockoutObservationWindow “0.00:30:00” -LockoutThreshold 6 -MaxPasswordAge “12.00:00:00” -MinPasswordAge “1.00:00:00” -MinPasswordLength 8 -PasswordHistoryCount 12 -ReversibleEncryptionEnabled $false
Next, assign a password policy to a user group using:
Add-ADFineGrainedPasswordPolicySubject “Admin PSO Policy” -Subjects “Domain Admins”
Change the PSO policy settings using:
Set-ADFineGrainedPasswordPolicy "Admin PSO Policy" -PasswordHistoryCount:"12"
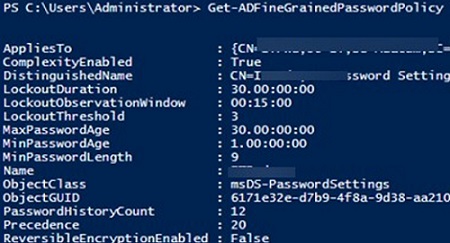
List all FGPP policies in a domain:
Get-ADFineGrainedPasswordPolicy -Filter *
Use the Get-ADUserResultantPasswordPolicy command to get the resulting password policy that applies to a specific user.
Get-ADUserResultantPasswordPolicy -Identity jsmith
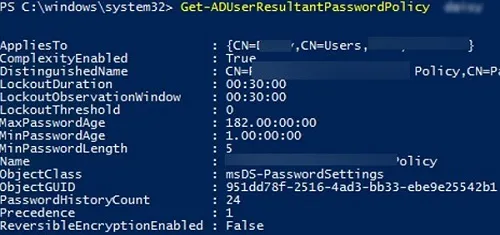
The name of the PSO that applies to the user is specified in the Name field.
You can display the list of PSO policies assigned to an Active Directory group using the Get-ADGroup cmdlet:
Get-ADGroup "Domain Admins" -properties * | Select-Object msDS-PSOApplied
To show the default password policy settings from the Default Domain Policy GPO, run the command:
Get-ADDefaultDomainPasswordPolicy
Limitations of Microsoft fine-grained password policy
We’ve walked through how to create a FGPP in your Active Directory, but it’s important to also understand the limitations. You’re unable to create custom dictionary lists, restricting your options to block certain words and phrases relevant to your organization. FGPP also lacks the ability to find and remove compromised passwords already in use, or to block passwords being used in current attacks taking place in real time.
You’ll have additional work to do to meet cybersecurity requirements, as there are no password policy templates for regulations such as NIST and NCSC. Nor are there any dedicated reporting options. Working with the out-of-the-box FGPP and Windows Client also add nothing for the end user, with no dynamic feedback for users at the password change stage and no option for you to customize notification messages.
Specops Password Policy: An improved option
While we still have to live with passwords there are more versatile, user friendly, and feature rich solutions available. Specops Password Policy comes with templates that allow you to follow the latest NIST and NCSC Cyber Essentials guidelines and gives true fine-grained control over any password policy requirements that you may need to apply to your organization. You can create an unlimited custom dictionary specific to your organization, on top of stopping people using weak passwords such as their names (full or partial), incremental passwords, or common character substitutions.
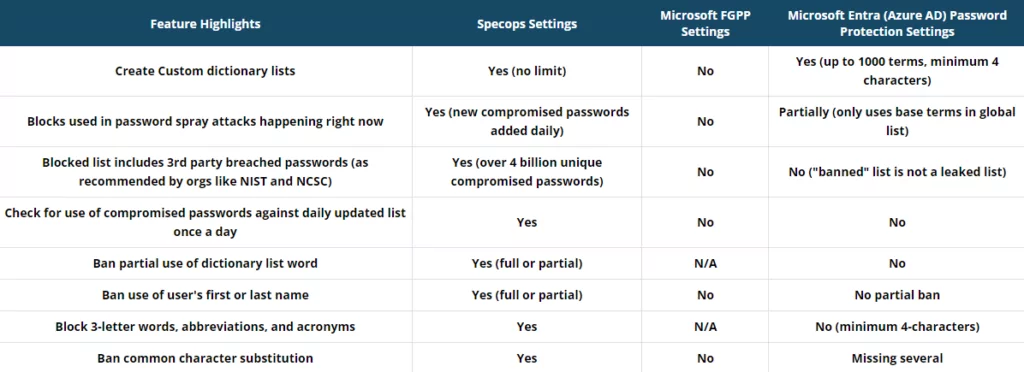
The Breached Password Protection (BPP) feature also continuously checks and blocks over 4 billion unique compromised passwords – including daily additions of passwords being used in live attacks, as well as passwords obtained by malware. Specops Password Policy also gives your users a better, more helpful experience, with customizable email notifications. Real-time dynamic feedback then guides users to create memorable, secure passphrases during password changes. Length-based aging also encourages users to create better passwords, as longer more secure passphrases will not have to be changed as often as shorter, weaker ones.
(Last updated on April 30, 2025)