STOCKHOLM – Today, Specops Software announced the addition of the latest HaveIBeenPwned (HIBP) password list update, v7, to its Breached Password Protection database. Over 226 million passwords from over 23,000 hacked databases are in HIBP v7, a collection of... Read More
News and Research
How to change the Active Directory password hash method
Passwords are generally associated with all aspects of securing technology systems. In most environments, passwords are secured using a password hash. Password hashes can impact how vulnerable an organization’s passwords are to an attacker, or in a data leak that... Read More
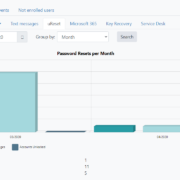
SSPR registration guide
The benefits of using a self-service password reset (SSPR) solution can be quantified by the number of reduced password-related calls to the IT service desk. For many organizations, this means significant cost savings. Gartner Research estimates that each password... Read More
Find AD accounts using Password-Not-Required (blank password)
The landscape of passwords across an Active Directory environment can certainly be varied. Even with password policies in place there is still the potential for risky passwords assigned to user accounts in the environment. One such dangerous type of... Read More
Survey reveals why SMEs are decreasing their investment in cyber security
With recent industry research revealing that small and medium-sized enterprises (SMEs) are decreasing their investment in cyber security, we wanted to understand why – particularly in a digital age where we are increasingly dependent on technology. In a bid... Read More
£36m lost to fraud and cyber crime in 2020
In 2019, an estimated 1.94 billion people purchased goods or services online – and that number is growing year-on-year. However, those shopping online must be wary when making any online purchases, as our latest research has found that £36,262,000 has... Read More
Specops supports PingID to secure password resets
Stockholm, November 17, 2020 – Specops Software released an update to its Specops Authentication platform today. The platform secures password resets, password changes, and encryption key recovery with multi-factor authentication (MFA). The introduction of PingID authentication advances security for... Read More
The holidays most likely to be found in your passwords [new data]
STOCKHOLM – Holidays are often a joyous time of year and new data seems to indicate people like to celebrate with their passwords. Today, Specops Software released an update to the Breached Password Protection list and a recent analysis... Read More
How to audit password changes in AD
Windows Server provides native tools for changing user passwords and auditing password changes in AD. However, they are somewhat lacking. Third-party tools such as Specops uReset can make the process easier and more secure. ADUC There are two main... Read More
How to unlock active directory account lockouts
There is no question that one of the most common tasks that helpdesk and IT admins carry out on a daily basis is user account management. Specifically, triaging user account issues like unlocking active directory accounts in an Active... Read More