This website uses cookies to ensure you get the best experience on our website. Learn more
Common ransomware attack types: How they work & tips for prevention
Table of Contents
Think of ransomware attacks as a form of digital kidnapping. Cybercriminals use encryption to lock you out of your files or devices, effectively holding them hostage until a ransom is paid. Like traditional kidnappers, their primary motive is financial gain. According to the State of Ransomware 2024 report from Sophos, 59% of organizations surveyed were hit with ransomware attacks in 2024, with an average initial ransom demand of $2 million.
But paying the ransom doesn’t guarantee recovery. According to research by Kaspersky, only about 25% of victims who pay actually regain full access to their data. In other words, prevention is your best defense.
To protect yourself, it’s essential to recognize the warning signs of an attack. This post will walk you through how common ransomware attack types typically operate, so you can spot and stop them before they bring your system to a standstill.
What are ransomware attacks?
Ransomware attacks are types malware (malicious software) that block access to your computer system or encrypt your data until a fine, called ransom, is paid. If the ransom is paid, you receive a decryption key to retrieve your files or the attacker unlocks your files for you. However, if the payment is not made, the malicious actor may publish your data online, on the dark web, or block access to your files forever.
Ransomware attacks are often linked to credential security issues and poor password hygiene. They are also spread through other means, including:
- Phishing emails
- Software vulnerabilities
- Fake websites
In the past, attackers usually announced data exfiltration immediately, to put pressure on payments. But with changing times comes shifting ransomware tactics. More recently, attackers have started delaying public announcements, motivating companies to pay up to avoid public embarrassment.
How does a ransomware attack work?
Individual ransomware attack types work in slightly different ways, but in general, all ransomware attacks follow a typical pattern:
- Initial access: Attackers gain entry through phishing emails, malicious attachments, compromised websites, or by exploiting unpatched software vulnerabilities. Common tactics include tricking users into clicking a link or downloading malware-laced files.
- Malware installation: Once the system is breached, attackers silently install ransomware which begins to operate in the background. It may disable security software or use legitimate system tools to avoid detection.
- File encryption: The ransomware encrypts files on the infected device and often across the broader network, including shared drives and cloud-connected storage.
- Ransom demand: The victim receives a ransom note demanding payment, most often in cryptocurrency, in exchange for the decryption key. This typically includes instructions on how to pay, with threats of permanent data loss or increased ransom if the victim doesn’t pay up promptly.
- Aftermath: Even if the victim pays the ransom, there’s no guarantee the attackers will restore all files. Victims may face extended downtime, data breaches, financial losses, and the need for costly recovery and security improvements.
Common ransomware attack types
Locker Ransomware
In this ransomware attack type, a hacker or ransomware gang uses malware to block access to certain system functions or files. Attackers typically gain entry through social engineering tactics, like phishing emails or harvested credentials. Once inside, they lock users out of their devices or key functions and demand a ransom for restored access.
Unlike certain other ransomware variants that encrypt or destroy data, locker ransomware doesn’t usually target individual files or spread across an entire network. Instead, it restricts access to the device’s interface — sometimes partially disabling the keyboard or mouse — while leaving the data itself untouched. Because the underlying files are not encrypted or corrupted, it’s often easier to detect and remove locker ransomware without paying the ransom.
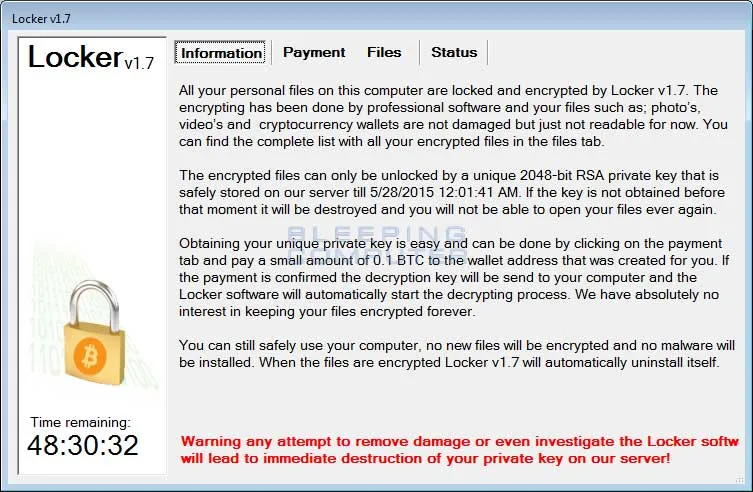
Locker ransomware is encrypted with an advanced encryption system called AES (Advanced Encryption Standard). If you don’t know the code, this can be nearly impossible to break. However, if you’ve backed up your files, you can usually easily retrieve them without paying the ransom.
Crypto ransomware
Crypto ransomware — or encryptors — is one of the most common and destructive ransomware attack types. Like Locker ransomware, crypto hackers use compromised credentials, system vulnerabilities, weak passwords, and phishing to infiltrate systems.
However, unlike locker ransomware, which blocks access to a device’s interface, crypto ransomware encrypts valuable files such as documents, photos, and videos, while leaving basic system functions untouched. Victims can still use their device and see their files, but cannot access them.
Crypto hackers often add a countdown to their ransom demand: “If you don’t pay the ransom by the x deadline, all your files will be deleted“. Because many users lack proper data backups (whether in the cloud or on external drives), the consequences of a crypto ransomware attack can be devastating, often resulting in significant data loss and operational disruption.
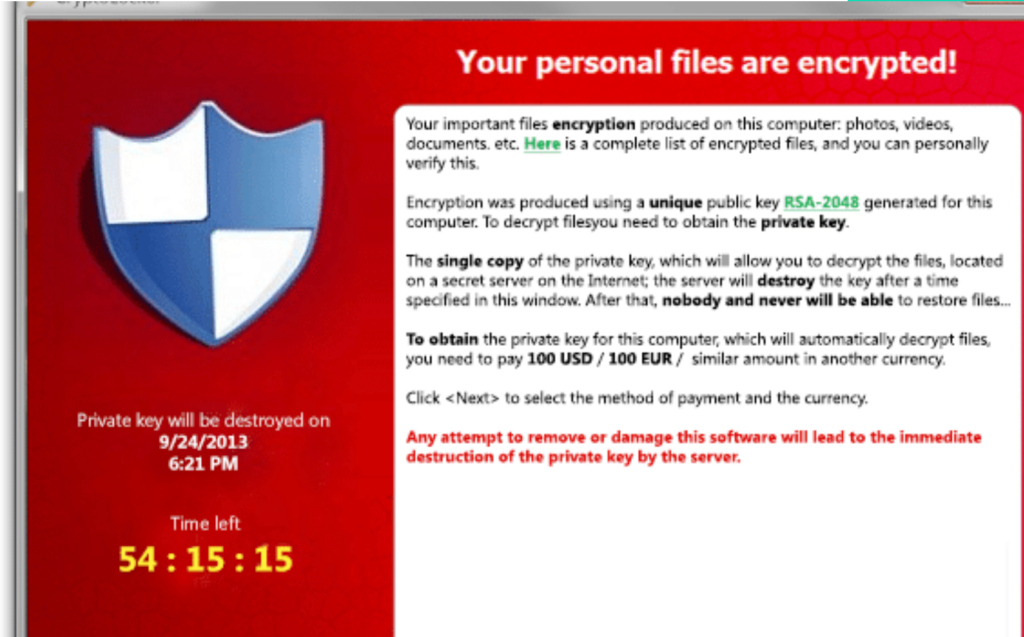
Scareware
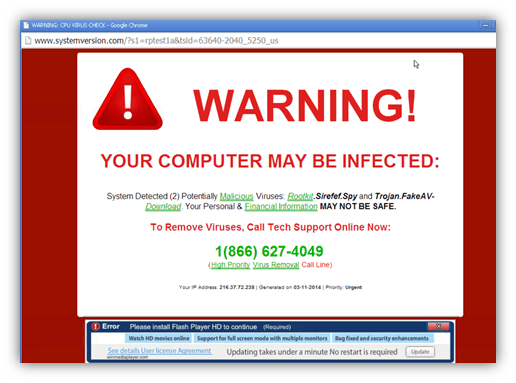
Just as its name suggests, scareware relies on fear and intimidation rather than actual system damage to manipulate victims. It typically appears in the form of fake antivirus alerts or system warnings, claiming that the computer is infected with malware or that illegal activity has been detected. These messages urge users to take immediate action, usually by purchasing fake software or paying a fee to “fix” the problem.
Unlike crypto or locker ransomware, scareware often doesn’t encrypt files or lock users out of their systems. In many cases, it simply floods the screen with persistent pop-ups or fake system scans to create a false sense of urgency. While scareware is generally less harmful than other ransomware attack types, it can still trick users into making unnecessary payments or downloading additional malicious software.
Fortunately, because it doesn’t typically alter or destroy files, scareware can often be removed with the help of antivirus tools.
Leakware
Leakware, also known as doxware, is a type of ransomware attack that threatens to publish or leak a victim’s sensitive data unless they pay a ransom. Instead of simply encrypting files or locking a system, leakware adds psychological pressure by targeting personal or embarrassing information, like financial records, business documents, or even private photos. The goal is to manipulate victims into paying out of fear that their data will be made public or sold on the dark web.
This tactic is particularly effective against organizations that handle sensitive information, like healthcare providers or businesses with intellectual property. Unlike some other ransomware attack types, leakware can cause reputational damage and loss of customer trust, even if the files themselves remain accessible. Because of this, the impact of a leakware attack often extends far beyond the immediate ransom demand.
Ransomware as a Service (RaaS)
Ransomware as a service (RaaS) is a model that allows cybercriminals with limited technical expertise to launch ransomware attacks using tools developed by more experienced threat actors. Affiliates pay to access ready-made ransomware and, in return, earn a percentage of each successful ransom payment. The fees depend on the ransomware’s complexity and features, and generally, there’s an entry fee to become a member.
Once an affiliate successfully infects a system and collects payment, a pre-agreed portion of the ransom is sent to the RaaS provider. This model mimics the gig economy, making it harder for cybersecurity professionals to trace specific attacks back to the developers of the ransomware itself.
RaaS operations often go beyond just providing malware; many include access to leak sites on the dark web where stolen data can be published to increase pressure on victims. This is a tactic known as double extortion. These platforms function much like Software-as-a-Service (SaaS) businesses, with ransomware creators offering their tools on a subscription basis and providing technical support, updates, and even dashboards to manage attacks.
This commercialization of cybercrime has significantly lowered the barrier to entry, contributing to the rise and scale of ransomware incidents worldwide.
Examples of ransomware attacks
Wannacry Ransomware
WannaCry Ransomware is a crypto-ransomware worm that attacks Windows OS. WannaCry, also known as WannaCrypt, WannaCryptor, and Wanna Decryptor, spreads using EternalBlue, an exploit that had been discovered by the National Security Agency (NSA). It’s a form of malware that can spread from PC to PC across networks (hence the “worm” component) and then once on a computer it can encrypt critical files (the “crypto” part). The perpetrators then demand ransom payments to unlock those files.
WannaCry is one of the first examples of a worldwide ransomware attack. It began with a cyber attack on May 12, 2017, that affected hundreds of thousands of computers in as many as 150 countries, including systems in the National Health Services of England and Scotland, FedEx, the University of Montreal, and Honda. Taking advantage of the vulnerable version of the Server Message Block (SMB) protocol, it ultimately infected approximately 200,000+ machines in more than 150 countries.
Unlike phishing attacks, computer users don’t have to click on a link or open an infected file. WannaCry just looks for other vulnerable systems to enter (like weak passwords or stolen credentials), then it copies and executes the program again, and again, and again. The only way for an infected user to access WannaCry encrypted files is if they have an external backup copy of those files. It has been reported that even though some organizations paid the Bitcoin ransom, none of the encrypted files were returned.
Robinhood – Baltimore Ransomware Attack
During the Baltimore ransomware attack of May 7, 2019, the American city of Baltimore, Maryland had its servers largely compromised by a variant of ransomware called Robinhood. Baltimore became the second U.S. city to fall victim to this new variant of ransomware after Greenville, North Carolina, and was the second major US city with a population of over 500,000 people to be hacked by ransomware two years after Atlanta was attacked the previous year.
The city of Baltimore spent spent about $10 million on recovery efforts because of this 2019 ransomware attack, not including an $8.2 million loss in revenues such as taxes, fees, and fines.
SamSam
SamSam ransomware is a custom infection used in targeted attacks, often deployed using a wide range of exploits or brute-force tactics. SamSam ransomware attacked the State of Colorado’s 300 services, all databases, applications, and 1300 computers.
The first known version of SamSam ransomware appeared in late 2015. Also known as Samas or SamsamCrypt, the type targets organizations within multiple industries, including critical infrastructure establishments from the healthcare and public health sectors, the transportation sector, and the education sector. SamSam uses either vulnerabilities in remote desktop protocols (RDP), Java-based web servers, or file transfer protocol (FTP) servers to gain access to the victims’ network or brute force weak passwords to obtain an initial foothold.
SamSam specializes in targeted ransomware attacks, breaking into networks and encrypting multiple computers across an organization before issuing a high-value ransom demand. The group is believed to be behind the attack on the city of Atlanta in March, which saw numerous municipal computers encrypted.
Darkside Ransomware
DarkSide is a ransomware gang that operates as a Ransomware-as-a-Service (RaaS) operation that sells its services to affiliate malware gangs on the dark web. DarkSide ransomware is a relatively new ransomware strain that threat actors have been using to target multiple large, high-revenue organizations resulting in the encryption and theft of sensitive data and threats to make it publicly available if the ransom demand is not paid.
DarkSide ransomware performs brute force attacks and exploits known vulnerabilities in the remote desktop protocol (RDP) to gain initial access. After initial access, DarkSide ransomware performs validation on the machines to infect. DarkSide ransomware collects information about computer names and system languages in its initial code execution.
Ryuk Ransomware
Ryuk ransomware first emerged in August 2018 and quickly gained notoriety for targeting large, high-value organizations such as businesses, hospitals, and government agencies. Unlike opportunistic ransomware attacks that aim for volume, Ryuk is highly targeted and human-operated, with attackers tailoring each campaign to the victim’s network. Once inside, Ryuk can identify and encrypt network resources, delete shadow copies, and disable Windows System Restore, making recovery nearly impossible without external backups.
The attackers behind Ryuk engage in what the security industry calls “big game hunting,” demanding ransoms typically ranging from $100,000 to $500,000 or more. Their operations are stealthy and sophisticated, often beginning with phishing emails and followed by manual, multi-stage intrusions. Microsoft and other cybersecurity experts classify Ryuk as part of a broader trend where ransomware tactics mirror those of advanced persistent threat (APT) actors, focusing on precision, persistence, and high financial returns.
How to prevent ransomware attacks
How do you keep your company information safe from the clutches of digital kidnappers? While no solution is 100% foolproof, there are proven strategies that significantly reduce your risk. Here are five key strategies to prevent ransomware attacks and minimize their impact:
1. Back up your data
Backups are your strongest line of defense against ransomware attacks. But simply having backups isn’t enough — they must be cyber-resilient, meaning they’re encrypted, immutable (unchangeable), and regularly tested to ensure reliability and speed during recovery.
When backing up your data, follow these best practices:
- Back up everything: Include system and application files, databases, virtual machines, and data stored on SaaS platforms.
- Test regularly: Perform backup and recovery tests at least once a month to verify that everything restores correctly.
- Follow the 3-2-1-1 strategy: This advises storing four separate copies of your data — two stored locally in different formats, one stored offline, and one saved in an immutable format. Immutable data can’t be altered as there is no key to “unlock” it with, like with encrypted data. IDC now recommends that you store one copy of your data on immutable storage or in the cloud.
Cyber-resilient backups make it possible to recover without paying the ransom, provided they’re implemented and maintained correctly.
2. Implement a Zero-Trust security model
The Zero-Trust Model is based on the principle of “never trust, always verify.” It assumes every device, user, and network request is potentially hostile until proven otherwise. A strong Zero Trust architecture includes:
- Strict identity verification for all users and devices
- Network segmentation to limit access and contain breaches
- Layer 7 (application layer) threat prevention
- Least privilege access policies — users and apps only get access to what they absolutely need
- Continuous monitoring and validation of all activity
When implemented correctly, Zero Trust architecture not only strengthens security but also reduces operational complexity. It minimizes the chances of lateral movement within your environment, which is one of the key tactics ransomware operators use after gaining entry. Integrating External Attack Surface Management (EASM) tools can further help identify and address hidden vulnerabilities across internet-facing systems.
3. Perform regular vulnerability scanning
Ransomware often exploits unpatched vulnerabilities in software or network configurations. In fact, according to the State of Ransomware 2024 report from Sophos, 32% of ransomware attacks in 2024 began with an unpatched vulnerability.
To stay ahead of these threats:
- Use automated vulnerability scanners to detect weak points in your network.
- Configure scans to run during low-traffic periods to avoid bandwidth issues.
- Prioritize alerts based on risk, and ensure patching workflows are in place to fix high-severity issues quickly.
- Consider using tools like our free Specops Password Auditor to scan Active Directory for password-related vulnerabilities.
Vulnerability scanning gives you the visibility to detect exploitable gaps before attackers can take advantage of them.
4. Apply patches and updates promptly
Along with social engineering tactics, outdated software and systems are a favorite entry point for many ransomware attack types. Cybercriminals frequently target known vulnerabilities in unpatched systems to gain access and deploy malware.
To reduce this risk:
- Apply security patches and firmware updates as soon as they are released.
- Automate patch management where possible to streamline updates.
- Retire legacy technologies that are no longer supported with security fixes.
One notorious example is the WannaCry ransomware attack. It compromised over 200,000 systems worldwide by exploiting the SMBv1 protocol—a 30-year-old service—via the EternalBlue exploit. Microsoft had released a critical patch just weeks earlier, but many organizations failed to apply it in time, resulting in massive disruption.
5. Train employees to recognize threats
No matter how advanced your cybersecurity tools are, a single click on a malicious link can open the door to ransomware. In fact, phishing emails remain one of the most common delivery methods for ransomware. That’s why employee awareness and training is just as important as technical defenses.
To strengthen employee awareness:
- Carry out regular cybersecurity training sessions to educate staff on phishing, suspicious links, social engineering tactics, and safe online behavior.
- Use simulated phishing campaigns to test and reinforce awareness in a real-world context.
- Teach employees how to recognize common red flags like unexpected attachments, urgent or threatening language, unfamiliar senders, or unusual URLs.
Stop attackers before they get in
Weak or stolen credentials are among the most common entry points for ransomware attacks. Once attackers gain initial access (often through brute-force or credential-stuffing) they can move quickly to deploy ransomware and lock down your network.
Specops Password Policy helps you close that door. Enforce strong, unique passwords or passphrases that resist cracking attempts, and automatically scan your Active Directory against a continuously updated database of over 4 billion compromised credentials. It’s a powerful first line of defense against credential-based ransomware attacks. Book a free demo today and start building ransomware resilience.
Frequently Asked Questions
Ransomware is a type of malicious software that encrypts or blocks access to a victim’s data or system until a ransom is paid, usually in cryptocurrency. It’s often delivered via phishing emails, malicious downloads, or by exploiting unpatched vulnerabilities.
The most common types of ransomware attack include crypto ransomware, locker ransomware, scareware, leakware, and Ransomware-as-a-Service (RaaS).
Most ransomware infections begin through phishing emails, malicious attachments, drive-by downloads, or remote desktop protocol (RDP) exploits. In some cases, attackers use stolen credentials or unpatched software vulnerabilities to gain access. They then execute malicious code that encrypts files or locks users out of their devices. Once the attack is underway, the victim receives a ransom note demanding payment (usually in cryptocurrency) in exchange for a decryption key or restored access. Some variants also steal data and threaten to publish it unless the ransom is paid (a tactic known as double extortion).
Security experts and law enforcement agencies strongly advise against paying the ransom. Paying does not guarantee that you’ll get your data back, and it encourages further attacks. Instead, focus on prevention, data backup, and incident response planning.
Last updated on November 14, 2025