This website uses cookies to ensure you get the best experience on our website. Learn more

Reduce vulnerabilities to the WannaCry/WannaCrypt Ransomware outbreak with Specops
Table of Contents
The first line of defense in this scenario is to run the latest Operating system(s) fully patched. The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack, however should be treated as a vulnerability as well.
WannaCrypt ransomware worm targets out-of-date systems
Microsoft Security Bulletin MS17-010 – Critical
MS17-010: Security update for Windows SMB Server: March 14, 2017
Microsoft Support SMB Management post
This String of ransomware uses a specific Remote code execution from Windows SMB 1.0, which was used for Windows XP/Server 2003 functionality. There have since been improvements in SMB 2.0 and SMB 3.0.
Protection against WannaCry/WannaCrypt ransomware: Removing or disabling SMB 1.0 from your corporate network
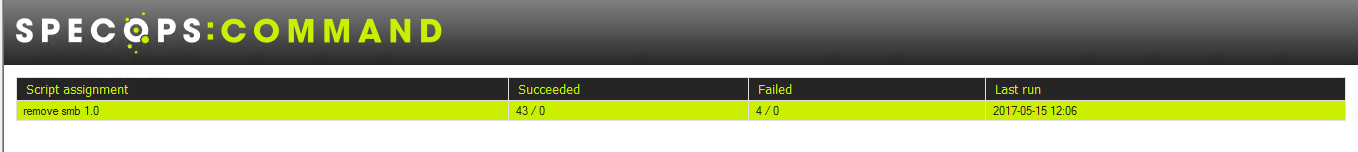
Removing this feature can be achieved using PowerShell. It is an effective method to return success feedback when running the script, and ensuring the command has been run on connected systems on your network.
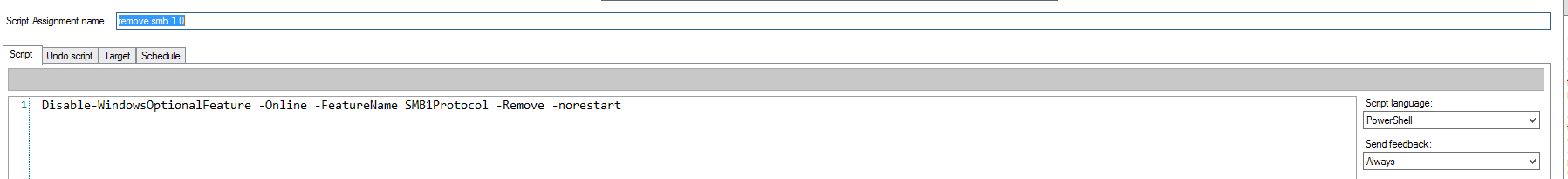
There are also ways to do this on your personal machine. You can turn off the Windows Feature ‘SMB1.0/CIFS File Sharing Support.’ As far as getting this disabled for your entire domain, it may take a bit more to deploy and enforce the following command:
Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol -Remove –norestart
<Or>
Remove-WindowsFeature FS-SMB1
Specops Command provides a platform to monitor and manage the actual command running in your workplace. Specops Command can schedule and execute this action and many more, and provide valuable feedback on execution of the command which can prove to be the type of response you need when minutes count.
Keep up your protection against WannaCry/WannaCrypt ransomware attacks. Download Specops Password Auditor, our free read-only password audit tool here.
Contact us today for a trial license to get through this deployment.
(Last updated on April 8, 2025)