This website uses cookies to ensure you get the best experience on our website. Learn more
Remote desktop protocol TCP port 3389 security risks and vulnerabilities
Table of Contents
There is no question that we’ve seen businesses scrambling to meet the needs of the distributed workforce. Many different remote access technologies allow businesses to provide the connectivity needed for remote employees to access business-critical applications. Remote Desktop Protocol (RDP) over TCP port 3389 is an extremely popular, easy to configure, and standard way to provide remote access capabilities to remote workers.
While RDP TCP port 3389 provides an easy way to connect remotely to corporate resources, it is notorious for many security vulnerabilities, including ransomware. What is Remote Desktop Protocol over TCP port 3389? What security vulnerabilities do you need to be aware of when using it? How can these vulnerabilities be overcome?
What is Remote Desktop Protocol TCP port 3389?
Remote Desktop Protocol (RDP) is a protocol that provides the ability to access a desktop computer remotely. When you think about “remote desktop,” many remote desktop protocols that provide similar functionality are available today. However, RDP is the protocol found in many enterprise environments Since it is a Microsoft technology and many organizations rely heavily on Windows Server and Windows client technologies, it is easy to see why it is the most common remote desktop access protocol in use today.
The most common RDP use cases, include:
- Provide a bastion host with applications into an environment that mimics local resources.
- Provide a common office environment for employees or contractors working from home and need to access systems for daily tasks
- Provides remote servers, regardless of their location, the ability to provide maintenance, set up, and troubleshooting.
Environments running Microsoft Windows Server and Windows client operating systems rely on Remote Desktop Protocol (RDP) for remote access, system administration, remote app functionality, and other robust capabilities provided by the tool. Since the Remote Desktop Protocol is built into Windows Server and client operating systems, it requires no additional download to use.
Below is an example of the Remote Desktop Connection built into the Windows 10 operating system.
What exactly does the term remote desktop mean anyway? Instead of physically sitting in front of the keyboard, monitor, and mouse of a Windows Server or client operating system, you can use “remote desktop” to remotely access the desktop. While hundreds or even thousands of miles away from the actual server or desktop, using RDP, you can perform the same functions as if you were sitting in front of the console.
Below is an example of remoting into a remote domain controller using the Remote Desktop Connection utility. As shown, the desktop displays in the same way as the console session of the Windows Server computer.
Remote Desktop Protocol vulnerabilities
Remote Desktop Protocol has historically been extremely vulnerable to various forms of attack that have allowed hackers to compromise and breach environments. Is the protocol itself secure? Unlike HTTP and FTP which are unencrypted, Remote Desktop Protocol (RDP) is transmitted over an encrypted channel. This prevents an attacker being able to “listen” to network traffic and compromise sensitive data.
However, there are RDP vulnerabilities to note. These include:
- Security vulnerabilities
- Misconfiguration
- Brute force attacks
1. Security vulnerabilities
There have been issues with Remote Desktop Protocol (RDP) encryption and vulnerabilities with the earlier versions in legacy Windows operating systems. However, in the past two years or so, there have been critical vulnerabilities found in how Microsoft implements the Remote Desktop Protocol. For example, BlueKeep is a security vulnerability noted in CVE-2019-0708. It allows an attacker to connect to an unpatched target system using RDP and then send special packets that allow remote code execution.
Businesses must keep Windows Servers and clients patched with the latest security patches to avoid falling victim to vulnerabilities from unpatched security flaws presented by the BlueKeep vulnerability and others.
2. Misconfiguration
Remote Desktop Protocol (RDP) is widely misconfigured and implemented incorrectly in production environments. Often, RDP servers are exposed directly to the Internet as this is a quick and easy way to provide remote access to distributed workers. Remote Desktop Protocol (RDP) servers should never be directly exposed to the Internet, where TCP port 3389 can be reached directly. This is a recipe for disaster.
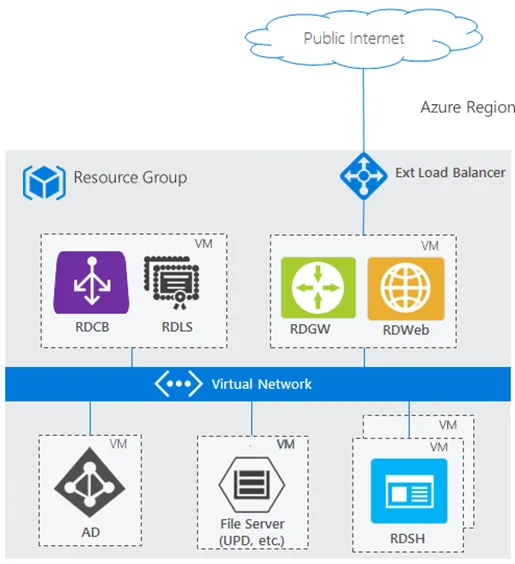
Instead, Microsoft recommends RDP is implemented with a Remote Desktop Services Gateway server. When the RDS Gateway Server sits in front of the backend RDP session host server, the RDP protocol is tunneled over an SSL HTTPS connection. This configuration dramatically improves the security of an RDP implementation.
Below is the reference architecture from Microsoft for implementing a basic Remote Desktop Services implementation with an RDP server in the backend. Note how the RDP server is not exposed to the public Internet directly.
3. Brute force attacks
Attackers look for exposed RDP servers on the Internet as these can be easy targets for brute force attacks. Additionally, attackers may conduct password spraying attacks on RDP servers and try known breached credentials on exposed servers. Many organizations find that monitoring RDP servers reveals hundreds if not thousands of failed log attempts on their servers from attackers, bots, ransomware attacks, and others!
A recent report noted that phishing emails and attacks on remote desktop services are the top two ways cybercriminals launch ransomware attacks.
“Meanwhile, attacks against RDP services, where cyber criminals brute force weak or default usernames and passwords – or sometimes gain access to legitimate credentials via phishing emails – remain extremely popular with ransomware groups, also accounting for 42 percent of attacks.”
Note the mention of weak or default usernames and passwords, and legitimate credentials. Protecting passwords against common forms of attack and compromise is extremely important to protect against ransomware attacks on business-critical data.
Enforce strong password policies and use breached password protection, avoid RDP TCP port 3389 security risk
It is imperative that businesses enforce strong password policies and proactively protect their environment from breached passwords. The challenge is that Microsoft Active Directory lacks modern password policy features to safeguard organizations from common forms of attack.
Specops Password Policy bolsters password policies as it adds the ability to protect your Active Directory passwords from breached passwords. In addition, it includes protection that incorporates live attack data into the breached password capabilities, providing continuous protection from the latest breached password sources. It also makes it easy to add custom disallowed password lists to Active Directory specific to your business.
While Active Directory can incorporate custom password filter .dlls, a developer must write the custom password filter .dlls. These then must be integrated correctly into AD. The overall process can present challenges without the proper skill sets in-house. Specops Password Policy allows integrating custom password filter lists with just a few clicks.
It also keeps end-users from setting passwords found on Breached Password lists on the dark web and elsewhere. Admins and end-users can be alerted if their password becomes breached.
Find out more about other open ports and their vulnerabilities, for example TCP port 21 vulnerabilities.
(Last updated on March 25, 2025)