This website uses cookies to ensure you get the best experience on our website. Learn more
Passwordless realities of Entra ID (formerly Azure AD) Temporary Access Pass
Table of Contents
One of the new movements in authentication technology is called passwordless authentication. With passwordless authentication, end-users can use other means to sign in aside from the traditional password. Microsoft’s Temporary Access Pass for Microsoft Entra ID (formerly Azure Active Directory) allows users to securely log in without a password. It is a time-limited passcode that an Entra ID (formerly Azure AD) admin issues to an end-user.
The Temporary Access Pass is a mechanism that meets strong authentication requirements and can be used to onboard other authentication mechanisms, including passwordless authentication. Temporary Access Pass is also an excellent way for users who have lost their FIDO2 security key or 2-factor authentication app to regain access to their account.
Let’s look at how to use Microsoft’s Temporary Access Pass and some important considerations for introducing this to your network.
Create a Temporary Access Pass
There are a few steps involved to enable and use Temporary Access Pass. This process includes two steps:
- Create a Temporary Access Pass policy
- Create the Temporary Access Pass for end-users
Create a Temporary Access Pass policy
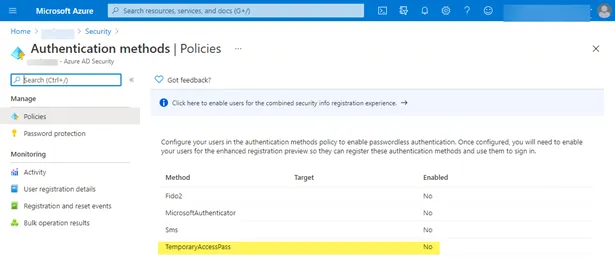
Before creating a Temporary Access Pass for an Entra ID (formerly Azure AD) user, you must first enable the Temporary Access Pass policy. The policy defines settings, such as the lifetime of passes created in the tenant or the users and groups who can use a Temporary Access Pass to sign in. It is enabled in Entra ID (formerly Azure AD) security options. Navigate to Microsoft Entra ID (formerly Azure Active Directory) in the Azure Portal. Click Security > Authentication methods. As you can see below, Temporary Access Pass is not enabled.
In the Details for the Temporary Access Pass configuration, set Enable to Yes. You can also define which users to which the policy applies. As you will notice, you can configure other aspects of the Temporary Access Pass policy. It includes:
- Minimum lifetime
- Maximum lifetime
- Default lifetime
- One-time use
- Length
After saving the policy changes, the Temporary Access Policy is now showing as enabled.
We are now ready to enable a user to login with a Temporary Access Pass.
Create the Temporary Access Pass for end-users
Since the policy is now created, the Temporary Access Pass can be enabled for selected end-users. It can be enabled using both the Azure Portal GUI as well as PowerShell. Let’s first see how to do this with the Azure GUI. In Azure A in the Azure Portal, browse to the user, select Authentication methods > Add authentication method. If you see a ribbon that notes you need to enable preview features, do this. Under the Add authentication method blade that pops out from the right of the screen, click the drop-down and select Temporary Access Pass (Preview).
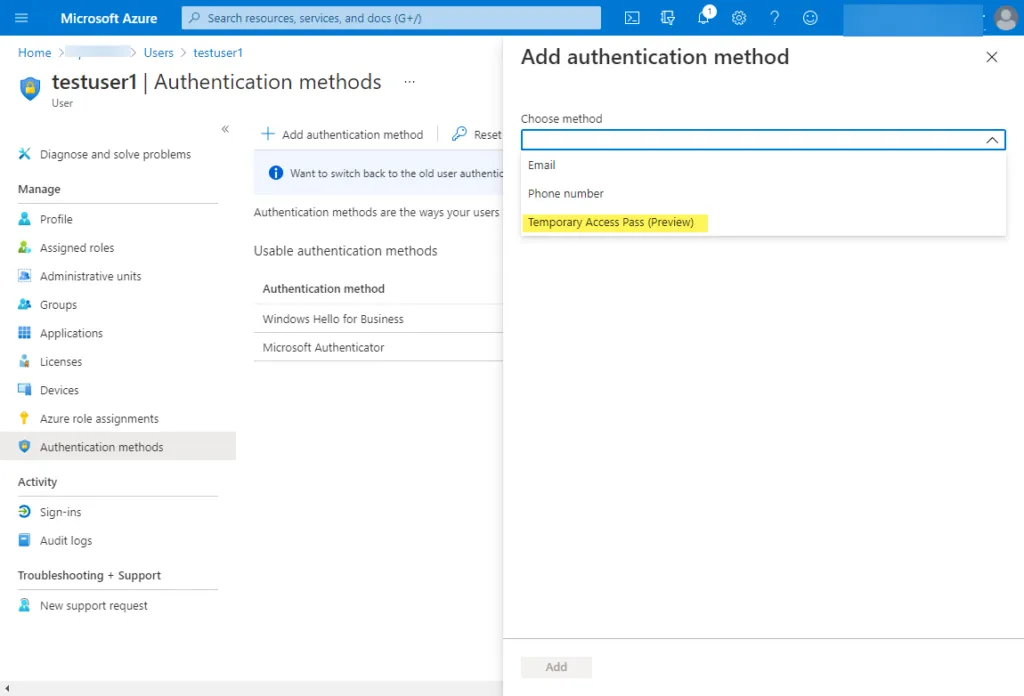
You can customize additional features of the new authentication method, including delaying the start time and how long the activation lasts. There is also the option for a One-time use that can be flagged.
After clicking the Add button, you will see the Temporary Access Pass displayed as well as the URL the end-user must visit to activate it.
Creating a Temporary Access Path is best accomplished in code using PowerShell. Microsoft has documented an example of using PowerShell to create a Temporary Access Pass for a user. This is a great way to create a Temporary Access Path in bulk.
Using the Temporary Access Path
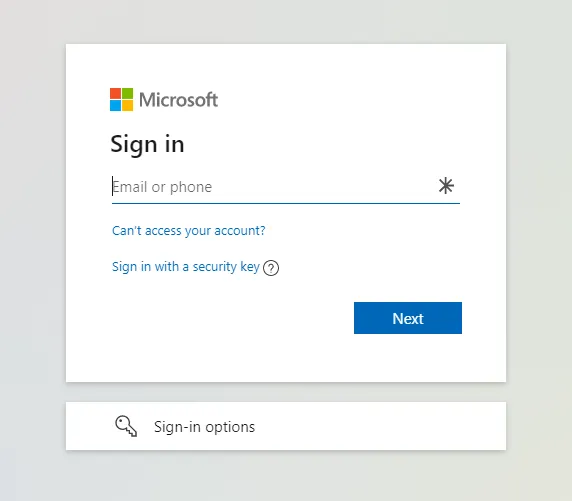
How is the Temporary Access Path used? By browsing to the URL provided in the Temporary Access Path creation dialog, the end-user will be prompted to log in. The URL is https://aka.ms/mysecurityinfo. They will log in using their username@domain.onmicrosoft.com username as an example.
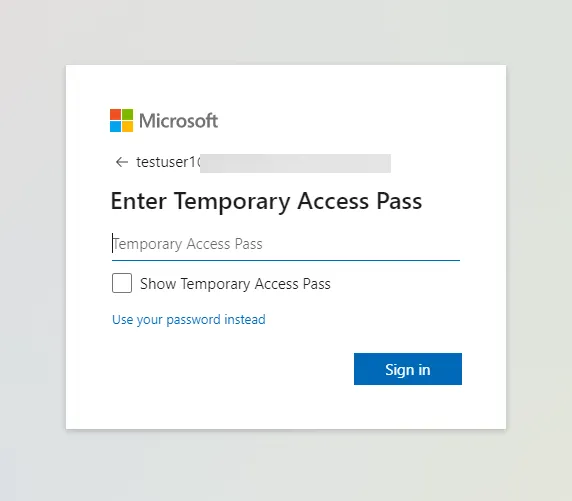
Next, they enter the Temporary Access Pass given to them by the administrator.
Once logged in, they will see the security information details of the Temporary access pass.
Limitations of the Temporary Access Pass
There are two important considerations if you are introducing Temporary Access Pass to your environment.
The first, is the security of your service desk. The Temporary Access Pass is a way for users to login when their other authentication method fails. How do they access that code? They call the IT service desk. Without secure user authentication at the service desk, this scenario opens up a vulnerability to a social engineering attack. Rather than rely on insecure methods like employee ID, make sure you are using a service like Specops Secure Service Desk to enforce strong user authentication at the IT service desk.
The second, is that the Temporary Access Pass does not get rid of the Active Directory password. Active Directory passwords are still at work in background for most users. Whether it’s the back-up to a forgotten Windows Hello for Business pin or the authentication method for your user’s VPN connection, the Active Directory password is still required. So, while the Temporary Access Pass may minimize the use of Active Directory passwords, the need to secure them with a solution like Specops Password Policy is still critical.
Some tips for securing your AD passwords:
- Enforce the creation of long passwords (Easy to do with length-based password aging in Specops Password Policy)
- Continuously check for the use of known leaked passwords (Block over 4 billion with Specops Breached Password Protection)
- Secure password resets whether self-service or at the service desk (Use Specops uReset to lift the password reset burden from your service desk and Specops Secure Service Desk to secure the rest of your service desk calls)
Solutions like Temporary Access Pass can help minimize the footprint of passwords but it’s important to secure the network you have today – and that still includes the AD password.
(Last updated on February 24, 2025)