This website uses cookies to ensure you get the best experience on our website. Learn more
Is your SSO login protected enough?
Table of Contents
Today, many organizations use more systems than ever, spanning on-premises and cloud environments. As a result, employees are tasked with remembering more and more passwords as the number of systems and services continues to grow. Single Sign-On (SSO) is a technology many organizations are leveraging to help ease the pain of using multiple systems. How does Single Sign-On work? What do companies need to do to ensure their SSO security is protected adequately?
What is Single Sign-On (SSO)?
The overall challenge with multiple systems and services for end-users is remembering various passwords for each system or online service. Many users may use the same password everywhere, which is risky. Also, they often choose weak and easily guessed passwords that may have even previously been breached . Single Sign-On (SSO) is an authentication mechanism that allows users to log in with a single username and password to ALL the systems they must use.
Single Sign-On leads to many advantages in the overall authentication process, including:
- Improve the workflow for end-users – Users do not have to remember and reset forgotten passwords. The login process is seamless with SSO and “just works” for most use cases where users access resources connected to the centralized SSO authentication mechanism. SSO covers a lot of sign-in use cases but will still leave some gaps.
- Reduce support calls – When fewer users struggle to remember passwords, and potentially lockout user accounts to various services, the less time the helpdesk spends supporting end-users.
- Bolster security – The beauty of the SSO solution is it centralizes the authentication process by using a central identity and access management platform. However, it also means the resources the users are accessing don’t have access to the credentials but instead are using a unique authentication token to validate the user as legitimate. It helps to reduce the likelihood of effective phishing attempts, etc.
- Speed up access time for business-critical resources – Due to the seamless, centralized access and elimination of the user needing to enter credentials for each resource they access, it speeds up access time, improving productivity.
- Meet compliance requirements and compensating controls – SSO helps to “check the right boxes” regarding today’s compliance regulations, including centralized reporting, auditing, robust authentication protocols, and easy revocation of account access when needed.
SSO and Active Directory – Good and Bad
Password protections in SSO providers are lacking, which is why orgs often turn to AD. However, AD alone still isn’t enough and organizations need 3rd party tools like compromised password check and better end-user messaging like Specops Password Policy with Breach Password Protection.
Many companies use Microsoft Active Directory Domain Services (AD DS) as their centralized directory of user credentials. It is also generally the centralized directory of user credentials serving as the “source of truth” for Single Sign-On (SSO) authentication. In addition, many organizations federate their Active Directory user database to access external entities using SSO, meaning the passwords assigned to Active Directory users are the password used as the underlying password for the SSO connection between services.
It means the overall security of the SSO solution can be either strengthened or weakened depending on the strength of the Active Directory password assigned to the user account. Attackers know that many organizations are using Active Directory as their centralized identity and access management directory for user credentials. As a result, they heavily target Active Directory and Active Directory user accounts.
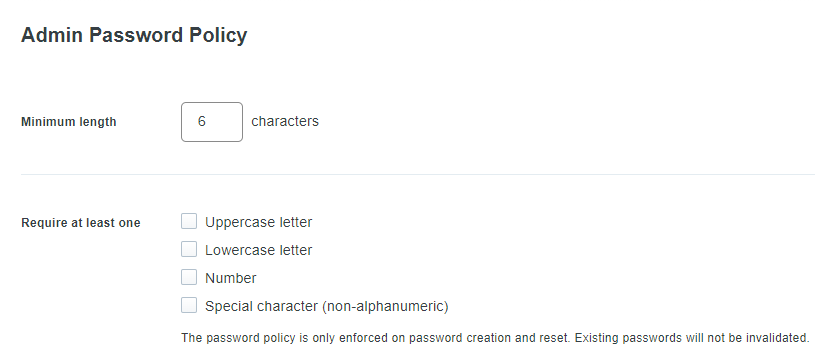
Even the Note Duo Security’s default password policy for Administrators. You can only configure the basics:
• Minimum length
• Require (uppercase letter, lowercase letter, number, special character (non-alphanumeric)
OKTA has more options, but it does not check for breached passwords or block against incremental passwords and other common types of weak or breachable passwords.
Linking your Single Sign-On configuration to Active Directory, while common, emphasizes the need to ensure you have best practice recommendations implemented to secure Active Directory, including password policy recommendations. However, if these protections are put in place, Active Directory can provide an extremely secure source for SSO credentials.
Since all the SSO-linked services and accounts will stem from the login credentials contained in Active Directory, you want your AD passwords to be as secure as possible. Traditional Active Directory password policies have not changed in the past two decades and are lacking in current password policy recommendations. NIST suggests the following password policy recommendations:
- Implement a lockout threshold after a specified number of failed logins – In Active Directory, this is known as an Account Lockout Policy. It allows setting a specified number of failed login attempts before the account is locked out.
- Use two-factor authentication – Two-factor authentication exponentially increases password security, requiring multiple “factors” to be used before authentication is successful
- Do check passwords for compromised or breached passwords – Many passwords are compromised before a user even creates them. Massive lists of compromised passwords are available to attackers who use them in brute force and other attacks to find accounts using the same compromised passwords. Active Directory has no native means to check passwords for breached status.
- Check passwords against lists of disallowed passwords – Disallowing common or weak passwords helps to prevent users from setting passwords that might pass the requirements of the assigned password policy but are inherently weak due to breached, common character substitutions, or other characteristics.
- Don’t allow the use of incremental passwords – Many users simply increment their Active Directory passwords. Preventing incremental passwords is a great way to prevent the practice of simply adding a number to a password to make it unique. Unfortunately, this is not a built-in feature of the Active Directory password policy.
- Prefer length over complexity – Simply requiring the addition of a special character does not make a password more secure as hackers know the common patterns and substitutions that users commonly use. Instead, preferring length over complexity, such as using passphrases or length-based password aging, is a better option for password security posture.
- Proactively monitor passwords – Continuous monitoring of passwords is necessary. Even if a password is not compromised today, it could become compromised tomorrow.
Protecting SSO with Specops
For organizations whose SSO “source of truth” is Active Directory, implementing strong password policies and breached password protection is a must. Also, creating password policies that go beyond the capabilities of the built-in Active Directory Password Policies or the password protections available within SSO solutions, such as blocking incremental passwords and custom lists of words, helps to ensure users are not creating weak and otherwise easily guessable passwords.
Specops Password Policy allows businesses to implement robust password policies quickly, without deviating from using Active Directory Password Policies. Instead, Specops integrates with Active Directory Group Policies companies are already using and adds the additional functionality needed to meet current security challenges. Note the following features of Specops Password Policy:
- Create custom dictionary lists to block customizable words that relate specifically to your organization
- Prevent the use of more than 4 billion compromised passwords
- Breached Password Protection includes passwords observed to be attacked “right now”
- Find compromised passwords in your environment and remediate these
- Intuitive end-user client messaging at failed password change, including real-time, dynamic feedback at password change
- Length-based password expiration with customizable email notifications
- Block user names, display names, specific words, consecutive characters, incremental passwords, and reusing part of the current password
- Granular, GPO-driven targeting for any GPO level, computer, user, or group population
- Passphrase support
- Over 25 languages supported
- Use Regular Expressions to customize blocking rules for passwords further
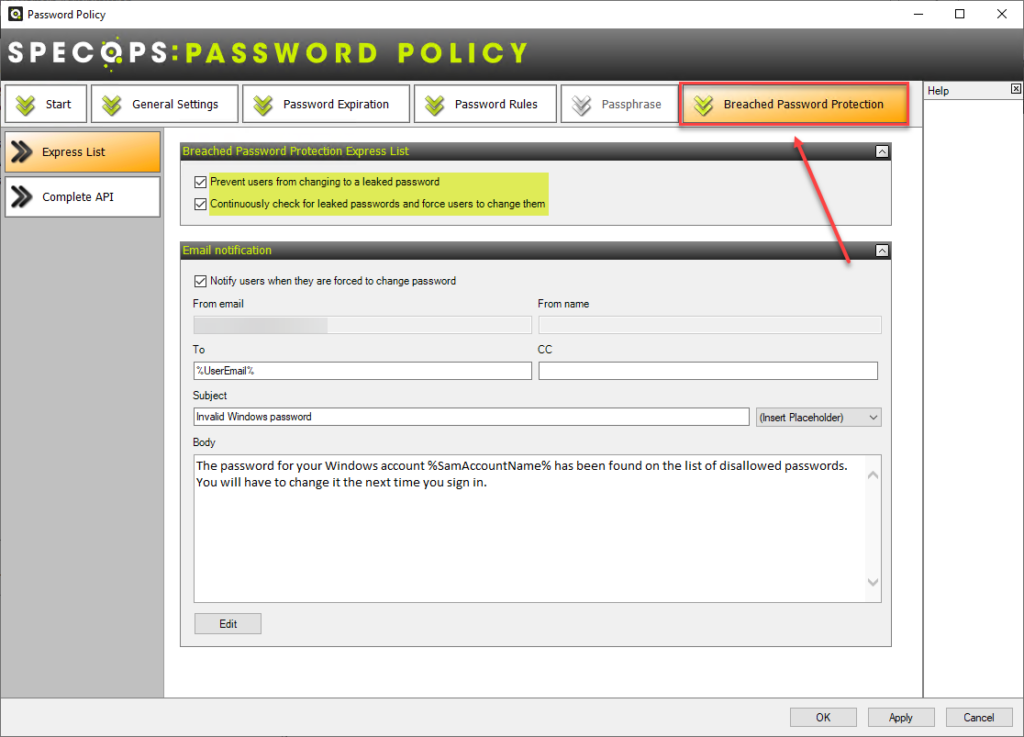
Below, Specops Breached Password Protection enables IT admins to prevent users from changing to a compromised password and continuously checks for compromised passwords. You can then force users to change passwords found to be compromised.
SSO final notes
Single Sign-On (SSO) provides many advantages for organizations managing dozens of services and systems for end-users. However, businesses must protect and secure the source of their SSO logins, such as Active Directory. Traditional Active Directory Password Policies offer little protection against password compromises today involving breached passwords and other vulnerabilities.
Using Specops Password Policy, businesses can bolster the central password policies housed in Active Directory Group Policy and use the framework of Group Policies already in place in the organization to not reinvent the wheel. Additionally, with the continuous breached password protection offered by Specops, companies have the protection needed to strengthen their password security posture. By extension, it strengthens the security of their SSO technologies tied to Active Directory Domain Services.
(Last updated on September 26, 2024)