This website uses cookies to ensure you get the best experience on our website. Learn more
Government of Canada password policy and best practices
Table of Contents
Governments worldwide document specific guidance related to cybersecurity and define best practices related to protecting business-critical resources from attack. The Government of Canada (GC) provides detailed password guidance best practices to keep passwords from being compromised. In this review of recommendations provided by the Government of Canada, we will look at the recommendations made and how these compare to other well-known guidance published by NIST and the NCSC (Cyber Essentials).
Why revisiting traditional password policies is needed
Traditional password policies have long been used to secure the use of passwords in the enterprise. Microsoft Active Directory Domain Services (AD DS) is the predominant technology used to create and establish password policies for end-users. However, many studies indicate that certain password policies and rules enforced by enterprise organizations are no longer effective at preventing compromise from an attacker.
By in large, there has been no change in the password policy settings in Microsoft Active Directory Domain Services for decades, and most businesses are still using the built-in settings defined by Group Policy password policy settings.
Studies have indicated that many traditional password policy settings in the enterprise may undermine the security of passwords instead of bolstering them. For example, password policy settings such as mandatory password expiration and forced password changes have been questioned as to their effectiveness.
In the security baseline draft for Windows 10 v1903 and Windows Server v1903, Microsoft stated they were “dropping the password-expiration policies that require periodic password changes.” They went on to say: “Recent scientific research calls into question the value of many long-standing password-security practices such as password expiration policies, and points instead to better alternatives such as enforcing banned-password lists (a great example being Azure AD password protection) and multi-factor authentication.“
The Government of Canada (GC) and many other cybersecurity authorities have reevaluated traditional password policy settings and have adopted new guidelines for securing passwords in the enterprise. In the NIST Special Publication 800-63B, it advises against mandatory password changes, stating:
- “Do not require that memorized secrets be changed arbitrarily (e.g., periodically) unless there is a user request or evidence of authenticator compromise.” Instead it recommends the following: “When processing requests to establish and change memorized secrets, verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised. For example, the list MAY include, but is not limited to:
- Passwords obtained from previous breach corpuses
- Dictionary words
- Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’)
- Context-specific words, such as the name of the service, the username, and derivatives thereof
Government of Canada (GC) Password Guidance
In the latest revision of its documented password guidance, the Government of Canada (GC) has adopted a more modern approach to password guidance that aligns with adjustments made by Microsoft and NIST with password expiration. Note the following as stated in the GC guidance on forced password changes:
“Forcing users to change their password at regular intervals puts a significant burden on users and has little effect on security. Typical password validity periods do little to prevent password cracking and, once a password is cracked, an attacker still has ample time to exploit the system. Also, users tend to select weak passwords that differ only slightly, and predictably.”
In addition to not recommending forced password changes, the Government of Canada (GC) recommends the following general guidance for passwords:
- Length over complexity – Disable or reduce complexity requirements. Longer simpler passwords are better than shorter more complex passwords.
- Require longer passwords – At least 12 characters in length without a maximum length limit. Also, IT admins should permit passphrases. In Windows environments, having a 15-character limit or longer prevents weak LAN manager password storage in Active Directory.
- Blacklist common passwords and combinations, such as “Password1!”
- Counter online guessing or brute forcing of passwords using throttling, account lockout policies, monitoring, and multi-factor authentication.
- Protect against offline attacks where an attacker can take the encrypted credentials and use powerful processing systems to try many billions of guesses per second. To protect against these offline attacks, using effecting hashing, salting, and keyed hashing. Password length also helps to protect against offline attacks.
Active Directory Password Policies do not support modern requirements
Microsoft Active Directory Password Policies, as found in Group Policy, haven’t changed in decades. While they allow configuring the basic requirements for passwords in the enterprise, they do not protect organizations against several key password risks in the environment, including:
- Incrementing passwords
- Breached passwords
- Contextual passwords
- Dictionary-based passwords
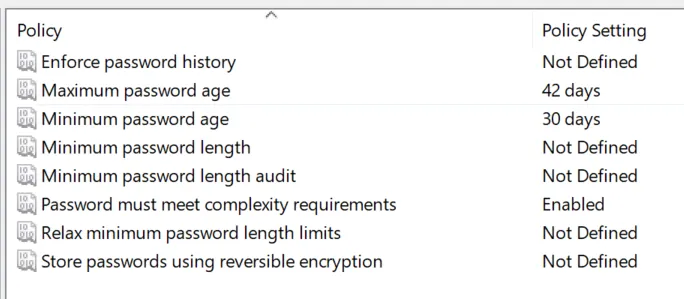
The following Active Directory Group Policy Password Policy settings are taken from a Windows Server 2022 domain controller. As you can see, the settings have not changed from the early days of Group Policy Password Policy.
Current Windows Server domain controllers do not have an easy way to introduce password filters. There is a means to do this but it requires development skill and low-level edits to your domain controller. In addition, there is no protection against breached passwords, commonly used passwords, contextual passwords, and other dangerous passwords that may meet the password policies defined, but that attackers scan for when attempting to compromise your environment.
Comparing password recommendations of the Government of Canada, NIST, and NCSC
Below is a comparison of a few basic characteristics of password recommendations from the Government of Canada, NIST, and NCSC
| Agency | Minimum Password Length | Password Expiry Recommended? | Complexity requirements | Monitor passwords |
| Government of Canada | 12 | No | Length over complexity | Yes |
| NIST | 8 | No | Length over complexity | Yes |
| NCSC | Use passphrases w/ Password Manager | No | Length over complexity | Yes |
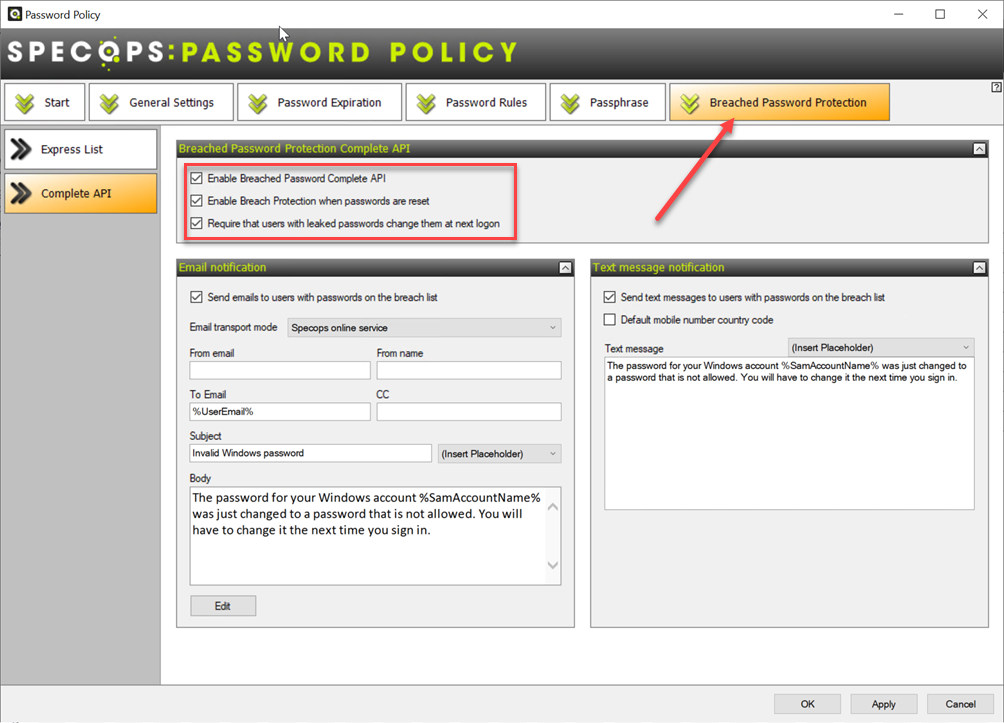
Specops Password Policy with Breached Password Protection
Specops Breached Password Protection found in Specops Password Policy is a robust solution that significantly bolsters Active Directory Password Policies. In addition, it is quick to implement and can implement breached password protection in your environment. For example, you prevent users from picking passwords that have been compromised when they reset them. You can also force users to change their password at the next login if these become breached.
Specops Password Policy allows organizations to quickly adopt the current password recommendations from cybersecurity authorities such as the Government of Canada, NIST, and the NCSC. In addition, using Specops Password Policy, organizations can continue to use the technology they are familiar with in Active Directory Password Policies and augment these to include many additional features.
Wrapping Up
Traditional password policies are not enough to prevent modern password attacks launched by cybercriminals from compromising your environment. As a result, many cybersecurity authorities have adopted Adjusted recommendations, such as removing the requirement for password expiration. The Government of Canada is one of these, along with Microsoft, NIST, and the NCSC. Specops Password Policy with Breached Password Protection provides businesses with the modern tools to implement modern password recommendations, including monitoring for breached passwords.
Learn more about Specops Password Policy with Breached Password Protection here: Specops Password Policy.
(Last updated on December 3, 2024)