This website uses cookies to ensure you get the best experience on our website. Learn more
Compliance Falls Short: New Research Shows Up to 83% of Known Compromised Passwords Would Satisfy Regulatory Requirements
Table of Contents
Organizations of all kinds look to regulatory recommendations and standards for guidance on how to best construct a secure password policy for their networks. However, new research shows regulatory password complexity and construction recommendations are not enough. Today, the Specops Software research team is sharing the results of their analysis on the number of compromised passwords found in leaked password data sets that would otherwise technically satisfy regulatory standards. This analysis coincides with the latest addition of over 24 million compromised passwords to the Specops Breached Password Protection service.
“What this data really tells us is that there is a very good reason why some regulatory recommendations now include a compromised password check,” said Darren James, Product Specialist at Specops Software. “Complexity and other rules might help but the most compliant password in the world doesn’t do anything to protect your network if it’s on a hacker’s compromised password list.”
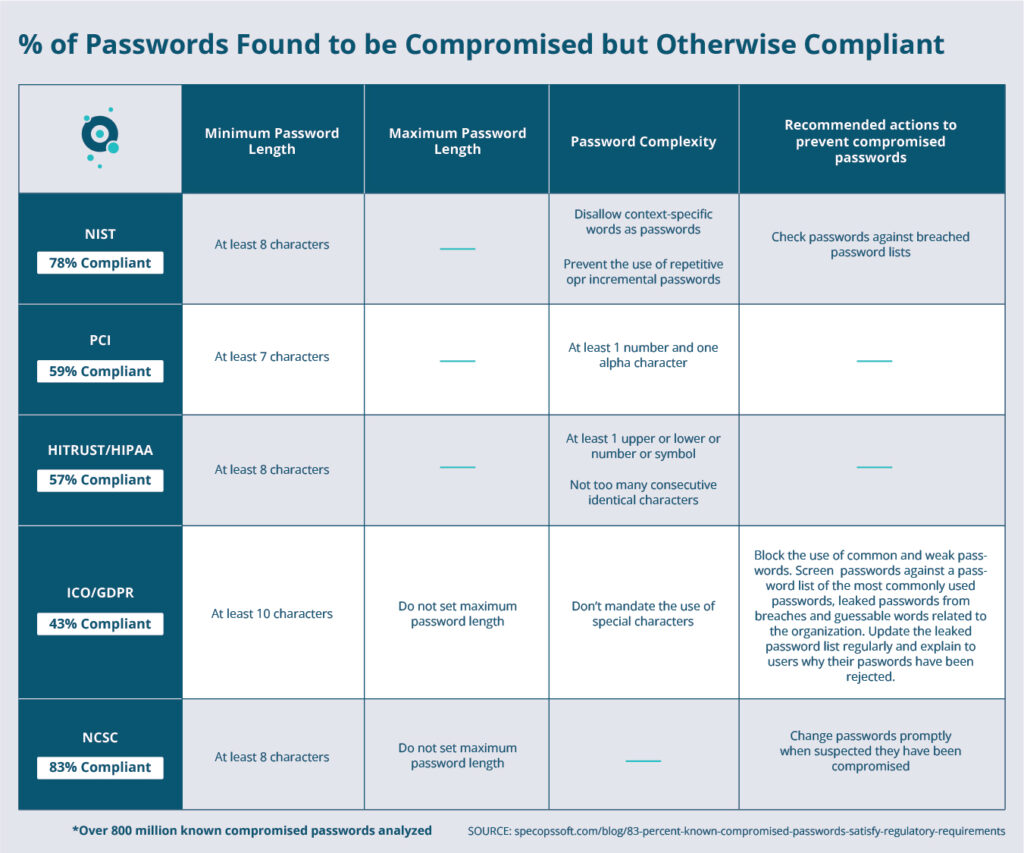
According to our team’s research, which analyzed over 800 million known compromised passwords, up to 83% of passwords that appear in compromised password databases would otherwise satisfy regulatory password standards. The team compared the construction rules of 5 different standards against a dataset of 800 million compromised passwords.
The following regulatory standard rules were investigated:
- NIST
- HITRUST for HIPAA
- PCI
- ICO for GDPR
- Cyber Essentials for NCSC
Quite a few of these standards include a recommendation or requirement to also use a known compromised password list to prevent the use of breached passwords — and for good reason. The following chart shows what percent of the known compromised password dataset would otherwise fulfill regulatory recommendations.
Almost NCSC (Cyber Essentials) Compliant Compromised Passwords
NCSC, the National Cyber Security Centre, is a part of the United Kingdom government that provides advice and support for the public and private sector on how to avoid computer security threats. The NCSC’s approved accreditation scheme, Cyber Essentials, outlines a standardized baseline for cyber security policies, controls, and technologies. Cyber Essentials is mandatory for government contracts that involve handling personal information, or provisioning certain products and services.
The Cyber Essentials password requirements include:
- set a minimum password length of at least 8 characters
- do not set a maximum password length
- change passwords promptly when suspected they have been compromised
When our team analyzed the compromised password dataset for passwords that are 8 characters or more, they found 82.98% of the passwords fulfilled that requirement.
Some examples of the nearly 83% otherwise compliant passwords:
- malcom01
- maidmarian
- magvai87magvai87
- maggie1987
- madrilena
Almost ICO/GDPR Compliant Compromised Passwords
The General Data Protection Regulation (GDPR) requires organizations to take care of protecting EU citizen data and privacy. The regulation provides no specific password guidance, but the Information Commissioner’s Office (ICO) which is responsible for enforcing the regulation, does provide some non-binding guidance, including:
- Password length: Minimum length should be 10 characters and there should be no maximum.
- Password complexity: Don’t mandate the use of special characters.
- Password deny list: Block the use of common and weak passwords. Screen passwords against a password list of the most commonly used passwords, leaked passwords from breaches and guessable words related to the organization. Update the leaked password list regularly and explain to users why they their passwords have been rejected.
When our team analyzed the compromised password dataset for passwords that would fulfill these recommendations, they found 43.48% of the compromised passwords would meet the password length standard.
Some samples of the 43% otherwise-compliant compromised passwords:
- ihatekittens
- ihatebrent
- ihateapples
- igor5062489
- igor454645
Almost HITRUST/HIPAA Compliant Compromised Passwords
Formed in 2007 to fill the gap in the often found to be vague requirements of HIPAA, the Health Information Trust (HITRUST) offers a framework to comply with standards such as ISO/IEC 27000-series and HIPAA. Some of the password guidance provided by HITRUST includes:
- Minimum of 8 characters
- At least 1 upper or lower or number or symbol
- Not too many consecutive identical characters
Our team defined “not too many consecutive identical characters” 4 or more, and found 56.87% of the compromised password dataset fulfilled the above guidance.
Some examples of the otherwise-compliant nearly 57% compromised passwords:
- freedom1321
- freddie43
- fortview0122015
- forrest55
- foolish16
Almost PCI Compliant Compromised Passwords
The major credit card companies – Visa, Mastercard, and American Express – established Payment Card Industry Data Security Standards (PCI DSS) guidelines in 2006 in an effort to protect credit card data from theft. PCI v3 has 12 Requirements; Requirement 8 covers identifying and authenticating access to system components and includes the following password recommendations:
- Minimum 7 characters
- At least 1 number and one alpha character
Our team analyzed the compromised password dataset for passwords that met the above criteria and found 59.14% of the dataset matched those requirements.
Some samples of the 59% otherwise compliant passwords:
- 22pink22
- 21dog657
- o1livia
- beatrice.99
- klippen5
Almost NIST Compliant Compromised Passwords
NIST, the National Institute of Standards and Technology, sets the information security standards for federal agencies (or organizations looking to do business with those agencies) in the United States. Through the NIST Special Publication 800-63B Digital Identity Guidelines, NIST provides best practices related to authentication and password lifecycle management. In this publication, NIST outlines several best practices to bolster password security, including:
- Minimum password length of 8 characters
- Prevent the use of repetitive or incremental passwords
- Disallow context-specific words as passwords
- Check passwords against breached password lists
Our team analyzed the 800 million compromised password dataset for passwords that met minimum length of 8 characters and did not use repetitive or incremental characters, and found 78.27% of the known compromised password dataset to fulfill those two recommendations. The repetitive/incremental check included looking for character repetition of at least 3 (aaa, bbb, ccc) and sequences of 123, 234 etc. In a real-world setting, context-specific checks such as preventing usernames and business-related words would drive this down further.
Some examples of the 78% otherwise compliant passwords:
- password1
- qwertyuiop
- 1q2w3e4r5t
- iloveyou
- myspace1
What to do about it
Passwords that would otherwise satisfy regulatory recommendations found in compromised password lists shouldn’t be ignored.
“Whether or not you are required to follow a regulatory standard that includes a compromised password check – this data makes clear that you should be implementing one anyway,” continued James.
Specops Breached Password Protection can help defend against password attacks by blocking the use of over 4 billion known compromised passwords in Active Directory.
You can find out how many of your Active Directory users are using compromised passwords like these by running a free read-only scan with Specops Password Auditor. Read more and download Specops Password Auditor here.
With Specops Password Policy and Breached Password Protection, companies can block over 4 billion compromised passwords in Active Directory. These compromised passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC. Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk.
About Specops Software
Specops Software, an Outpost24 group company, is the leading provider of password management and authentication solutions. Specops protects your business data by blocking weak passwords and securing user authentication. With a complete portfolio of solutions natively integrated with Active Directory, Specops ensures sensitive data is stored on-premises and in your control. Every day thousands of organizations use Specops Software to protect business data.
The Outpost24 group is pioneering cyber risk management with continuous vulnerability management, application security testing, threat intelligence and access management – in a single solution. Over 2,500 customers in more than 40 countries trust Outpost24’s unified solution to identify vulnerabilities, monitor external threats and reduce the attack surface with speed and confidence. Delivered through our cloud platform with powerful automation supported by our Cyber security experts, Outpost24 enables organizations to improve business outcomes by focusing on the cyber risk that matters. Visit Outpost24.com for more information.
Media Contact
Media contact details can be found on this page.
(Last updated on February 19, 2025)