This website uses cookies to ensure you get the best experience on our website. Learn more
How to stop O365 phishing attacks
With a 56% market share in 2018, Office 365 (O365) and its users are an obvious target for cybercriminals looking for an easy way to access data that they can quickly translate into money. Phishing is such a successful attack vector that it continues to dominate as a means to gain entry to an organization’s network, or cloud environment. In organizations with users on personal devices, connecting via unsecured networks, cybercriminals find it easy to use social engineering tactics to trick them into giving up their O365 credentials. This is far less work than attempting to trick users into installing malware for the same purpose.
According to the 2019 State of the Phish report from security vendor Proofpoint, phishing attacks involving compromised accounts rose 71% in 2018. The combination of cloud-based services like O365, and user susceptibility to phishing attacks, provides a great recipe for cybercriminals – one they’re not going to give up on anytime soon.
Phishing email examples
For some context, let’s look at a few examples of actual scams that have happened in the last year involving O365:
- The one that almost cost €3 Million – A company’s CEO was targeted and tricked into giving up his O365 credentials. The cybercriminals were intent to change banking details to have millions wired to their bank. The scam was discovered before the wire was sent.
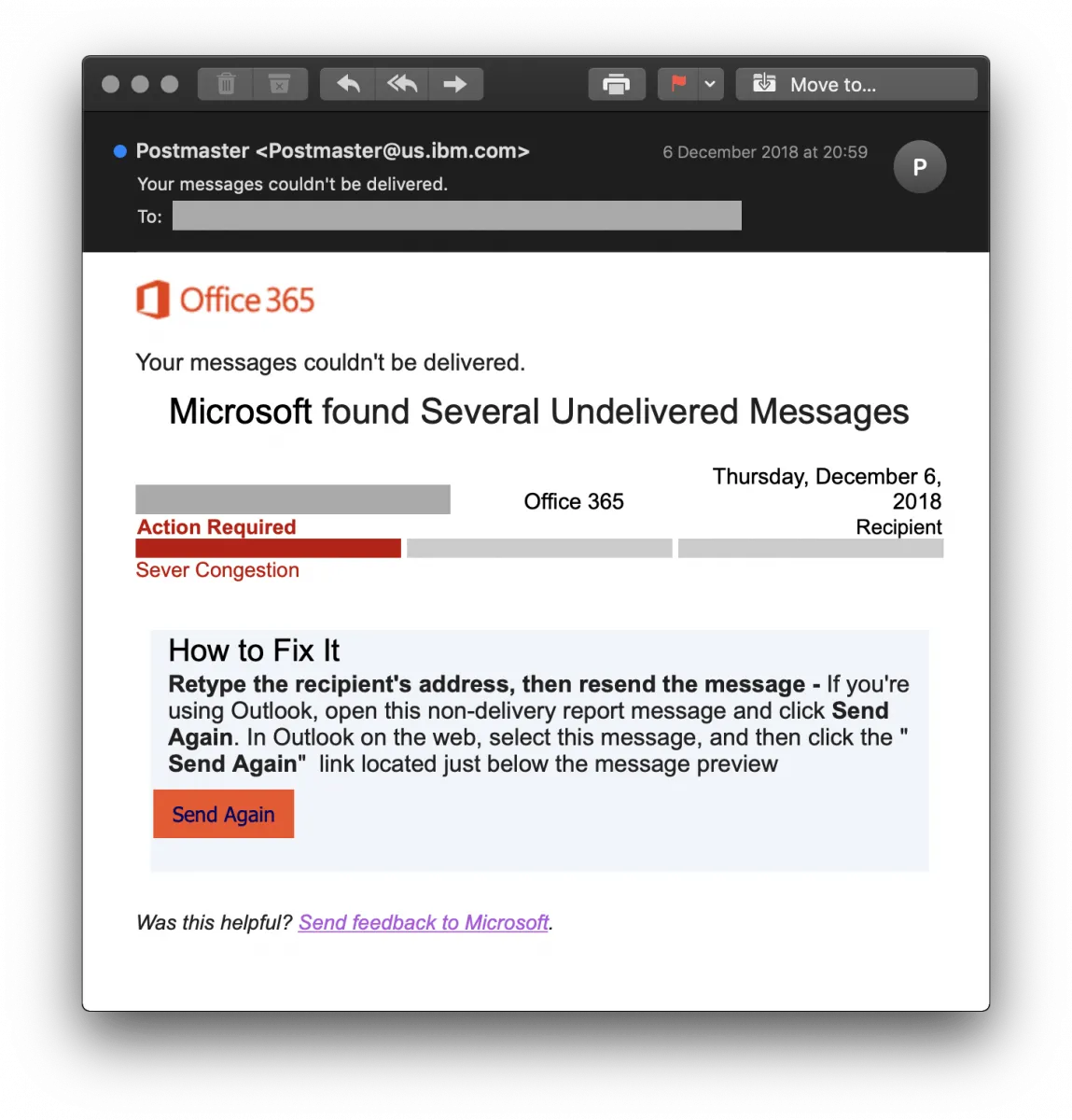
- The Non-Delivery Notification phish – A well-written, authentic-looking email notifies the recipient that “several undelivered messages” exist, with instructions to fix the problem complete with a “Send Again” button (shown below) which takes users to a spoofed O365 logon page to capture their credentials.
Because of the prevalence of O365 usage, the possibilities are limitless when it comes to phishing-based credential theft.
So how do you stop it?
Stop O365 phishing scams with MFA
The success of these phishing attacks lies in tricking the recipient into giving up their credentials. All that is needed is a solid business reason (e.g., the non-delivery above, an email about a tracked package, etc.) and a reasonably accurate spoofed logon page. What’s necessary here is a security measure that stands in the gap.
Multi-factor authentication (MFA) is a viable means to stop these scams. By requiring users to provide a second method to prove their identity, cybercriminals can be stopped in their tracks. Even if the victim gives up their O365 password on a spoofed logon site, the cybercriminal is powerless to use that credential in the organization’s actual O365 instance.
Many organizations settle for the SMS to mobile phone as the second factor.
But cybercriminals are aware of how to spoof mobile phones or can simply vish (voice phish) the phone’s owner into attaining the 2nd factor.
Organizations seeking to truly be secure need to leverage MFA in the following ways:
- Everyone should use MFA – it’s no longer enough to have just those deemed “important” in the company, or those with elevated permissions to use MFA. Cybercriminals are doing their homework, identifying industry verticals, companies, and even specific individuals within the company to phish. Any compromised account can be leveraged to move the criminal agenda forward through additional social engineering, or lateral movement within on-premises networks.
- Use stronger authentication factors – SMS feels very much like the password; an age-old method of identifying someone. Given that SMS messaging has been compromised, it makes more sense to utilize other types of factors, including: biometrics, mobile app-based code, and third-party identity providers. Use of multiple factors (providing it doesn’t hinder productivity) is also a desired option.
O365 phishing attacks will continue because they are easy, and lucrative. Until organizations implement real-world MFA that leverages more than just SMS messages, the security of user credentials is in question. By leveraging MFA that uses stronger factors, organizations reduce the likelihood of credential compromise to nearly zero, making O365 and the data it contains secure and untouched.
(Last updated on October 30, 2023)
Related Articles
-
MFA vs. 2FA – why the difference matters for your O365 implementation
When it comes to protecting cloud applications such as O365, two-factor authentication (2FA) has some serious limitations. A dynamic MFA solution frees users from passwords, and secures the authentication process.
Read More -
Why choose 3rd party MFA for O365?
The adoption of SaaS services requires organizations to house user data in the cloud. Without the right strategy in place, this can mean user management and authentication processes – outside the confines of IT. Take the move to O365, and its creation of a tenant in Azure AD. Maintaining it alongside the on-premises Active Directory…
Read More -
O365 attacks continue exploiting your weakest link
With more than 120 million active users, Office (O365) is a frontrunner in the cloud service popularity contest. Consequently, its users are equally popular with hackers. For IT pros, storing data in the cloud means a bigger attack surface, a threat aggravated by targeted, more sophisticated techniques. Guided by the “you are only secure as…
Read More