This website uses cookies to ensure you get the best experience on our website. Learn more
[New research] Which passwords are attackers using against RDP ports right now?
Table of Contents
The Specops research team has been analyzing 15 million passwords being used to attack RDP ports, in live attacks happening against networks right now. Our team have found the ten most common passwords attackers are using and analyzed their wordlists for the most common complexity rules and password lengths. We shared the results of a similar analysis back in 2022, so this research is now refreshed and up to date for 2025.
The launch of the report also coincides with the latest addition of over 85 million compromised passwords to the Specops Breached Password Protection service. These passwords come from our honeypot network and threat intelligence sources.
Why do hackers target the RDP port with brute force attacks?
One of the most common uses of the Remote Desktop Protocol (RDP) over TCP port 3389 is providing remote access capabilities to remote and hybrid workers. The RDP port can also give remote servers the ability to provide maintenance, set up, and troubleshooting, regardless of their location. It offers an easy way to remotely connect to corporate environments, which unfortunately also makes it a target for hackers.
Attackers are on the lookout for exposed RDP servers as these can be easy targets for brute force attacks. Additionally, attackers may conduct password spraying attacks on RDP servers and try known breached credentials on exposed servers. Many organizations find that monitoring RDP servers reveals hundreds if not thousands of failed log attempts on their servers from hackers, bots, ransomware attacks, and others.
Which passwords are being used in RDP attacks?
Our research team looked at a subset of NTLMv2 hashes collected from our honeypot system. These records span from March 2025 back to late 2024. In order to filter down to specifically RDP attacks, it was necessary to isolate the hashes recorded by the honeypot system. This means it was necessary to crack these records specifically for this exercise. Given the hardware and time available, it was possible to crack approximately 40% of these NTLMv2 records. So, bear in mind this data is illustrative of recent login attempts against the RDP port of said honeypots, rather than the full dataset contained in the Specops Breached Password Protection database.
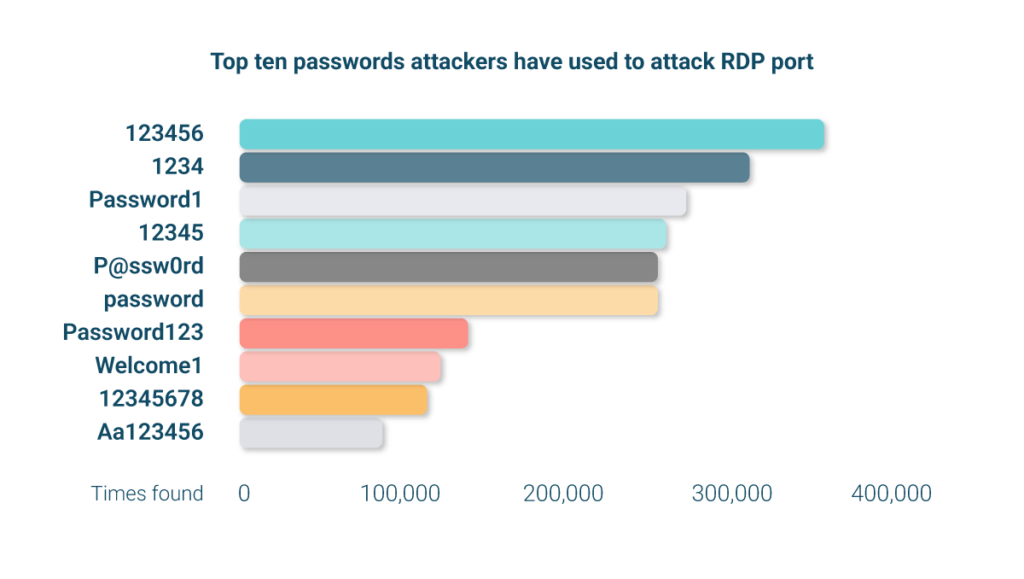
Top ten passwords used to attack the RDP port
Looking at the top ten list below, a few things stand out regarding the passwords attackers are using to target the RDP port:
- ‘123456’ was the top result and this also showed up as the most popular password stolen by malware in our 2025 Breached Password Report. This means lots of end users are still using very basic and vulnerable keyboard walks as passwords – you can see several examples in this top ten
- There are several variations of ‘password’ in the list. Hackers know that end users will often try to meet complexity requirements in the easiest way possible. For example, P@ssw0rd would pass the standard requirements set by many organizations of eight characters, one capital, one number, and one special character. But it’s still a weak password due to its predictability and common base term
- It’s interesting to see ‘Welcome1’ show up in the list. Recent Specops research suggested that many end users are given weak temporary passwords when joining organizations and are not forced to change them
| Password | Times found |
|---|---|
| 123456 | 355,088 |
| 1234 | 309,812 |
| Password1 | 271,381 |
| 12345 | 259,222 |
| P@ssw0rd | 254,065 |
| password | 138,761 |
| Password123 | 121,998 |
| Welcome1 | 113,820 |
| 12345678 | 86,682 |
| Aa123456 | 69,058 |
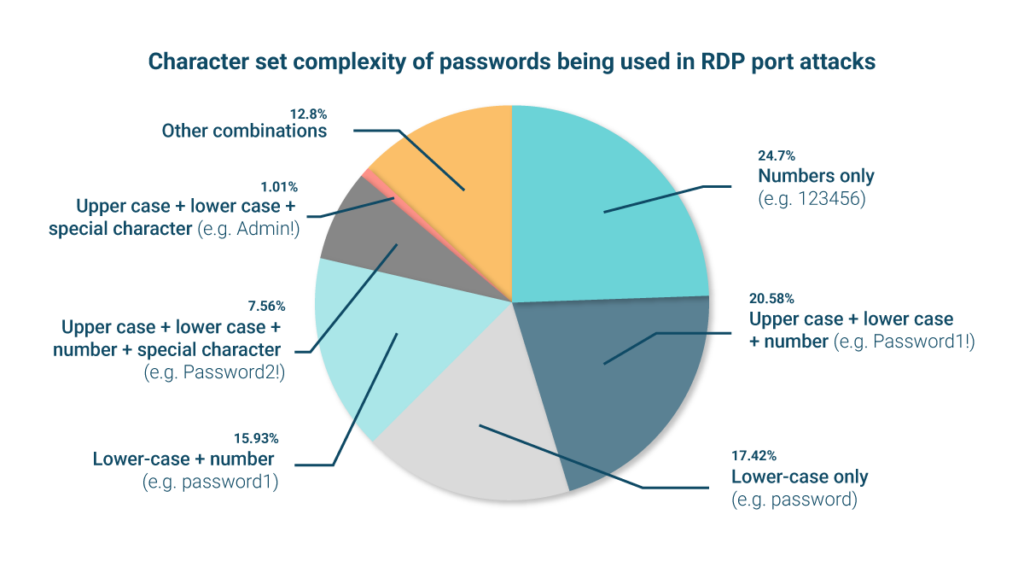
Character set complexity
We’ve looked at the character sets that make up the passwords being used in RDP port attacks. The below table shows some selected combinations of the four types of password character end users can choose on a keyboard:
- Numbers
- Lower case letters
- Upper case letters
- Special characters
As shown in the below table, only 7.56% of passwords being used in the attacks contained at least one character from the above options. Almost half of the passwords (45%) being used in the attacks were made up of only numbers or lower-case letters. The fact attackers still use such simple passwords in password spraying attacks shows how many end users still choose them.
An end user who had chosen a complex password (even a short basic one) would have been protected against >92% of the passwords being used in these RDP port attacks. But for a truly strong password, we need to factor in length too.
| Character Set | % of passwords used in RDP attacks |
|---|---|
| Numbers only (e.g. 123456) | 24.7% |
| Upper case + lower case + number (e.g. Password1!) | 20.58% |
| Lower-case only (e.g. password) | 17.42% |
| Lower-case + number (e.g. password1) | 15.93% |
| Upper case + lower case + number + special character (e.g. Password2!) | 7.56% |
| Upper case + lower case + special character (e.g. Admin!) | 1.01% |
| Other combinations | 12.8% |
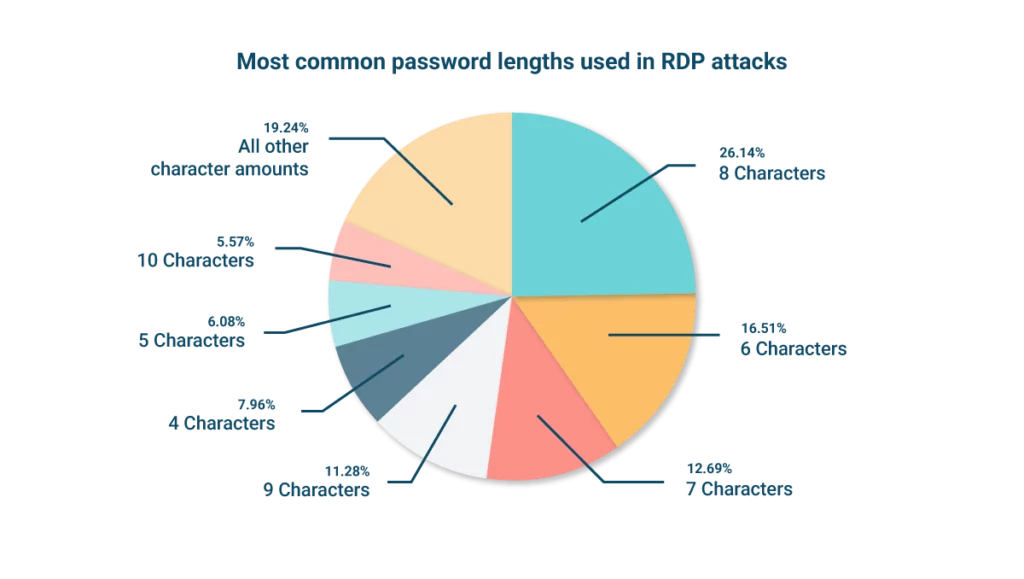
Most common password lengths used in attacks
Complexity is one factor that makes passwords more resistant to brute-force attacks, but the more important factor is password length. Once a hashed password gets over 15 characters in length with a degree of complexity, it becomes near impossible to crack with brute-force techniques. For more detail on how this works, check out some of our recent research into cracking SHA 256 hashed passwords.
Coming back to our passwords attacking the RDP port, we can see that eight is the most common length. Simply, this is because most organizations use eight as the minimum password length, and end users will often take the path of least resistance.
Only 1.35% of the passwords being used to attack the RDP port were over 12 characters. So, if your organization was enforcing passphrases of over 15 characters, your end users would be protected against 98% of the passwords being used in the attack.
| Password length | % of passwords used in RDP attacks |
|---|---|
| 8 characters | 26.14% |
| 6 characters | 16.51% |
| 7 characters | 12.69% |
| 9 characters | 11.28% |
| 4 characters | 7.96% |
| 5 characters | 6.08% |
| 10 characters | 5.57% |
| All other character amounts | 19.24% |
Find compromised passwords in your network today
This month’s update to the Breached Password Protection service includes this month’s addition of just under 5 million compromised passwords to the list used by Specops Password Auditor. You can find how many of your end users’ passwords are either compromised or identical with a read-only scan of your Active Directory from Specops Password Auditor. You’ll get a free customizable report on password-related vulnerabilities, including weak policies, breached passwords, and stale/inactive accounts. Download your free auditing tool here.
What can we learn from analyzing RDP attacks?
Most of the passwords being used in these RDP attacks would be described as weak. They’re either short, lack complexity, or use common base terms such as ‘password’. A good third-party solution can block end users from choosing weak Active Directory passwords (which are often reused as RDP or VPN passwords). Enforcing a strong password policy where users are encouraged to create long passphrases would offer protection against the vast majority of passwords we found in this analysis.
However, we’re not seeing only low hanging fruit by any means. A decent password policy can get you most of the way there, but there are some additional methods to employ that offer more complete protection of your RDP connections:
- Enabling push-spam resistant MFA to RDP connections adds a layer of protection, even if the password was to be breached. For example, Specops Secure Access can harden RDP connections with a second factor to better secure remote access
- Keep Windows servers and clients patched and up to date to protect against CVEs
- Check for misconfiguration – ensure the TCP port 3389 is using an SSL connection and isn’t exposed directly to the internet
- Limit the range of IP addresses that can use RDP connections
- Block the use of weak and compromised passwords in your Active Directory
Secure your organization against RDP brute force attacks
Specops Password Auditor offers a great starting point for assessing your current password risks, but it’s only a snapshot. With Specops Password Policy and Breached Password Protection, organizations can continuously protect themselves against over 3 billion more known unique compromised passwords (4 billion in total). These include compromised passwords that could be considered ‘strong’ and have been stolen by malware.
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. It also includes passwords found on breached password lists on the dark web and elsewhere. Breached Password Protection continuously scans your Active Directory for breached passwords and allows you to alert end users with customizable messaging that helps reduce calls to the service desk.
And if you want to secure the RDP connection with MFA on top of securing the password, you can add Specops Secure Access. Interested in seeing how this might work for your organization? Have questions on how you could adapt this for your needs? Contact us or see how it works with a demo or free trial.
Last updated on March 18, 2025