This website uses cookies to ensure you get the best experience on our website. Learn more
[New Data] Attackers Are Using These Passwords to Attack the RDP Port Right Now
Table of Contents
The Specops Breached Password Protection List Tops 3 Billion Unique Compromised Passwords from Live Attack Data and Leaked Lists
Today, the Specops Software research team is sharing the results of our analysis on what passwords are being used to attack RDP ports in live attacks happening against networks right now. This analysis coincides with the latest addition of over 34 million compromised passwords to the Specops Breached Password Protection service, which now tops over 4 billion unique compromised passwords.
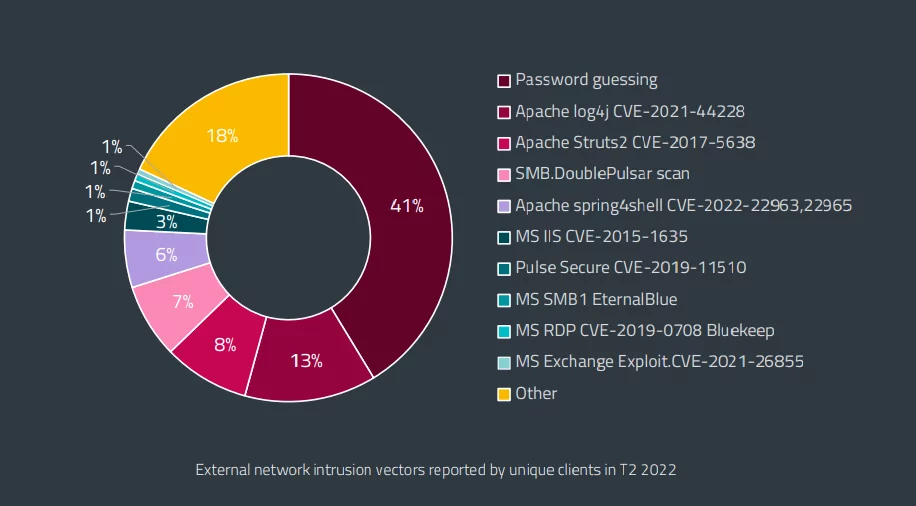
The Remote Desktop Protocol (RDP) over TCP port 3389 is a popular way to provide remote access capabilities to remote workers. The port is also a popular attack method for criminals despite the return to office, which is why Microsoft is introducing default RDP connection attempt lockouts in Windows 11. Brute force password guessing continues to top the list of attack methods experienced, with ESET reporting password guessing at 41% of all intrusion vectors.
For the newest data, please check out our updated RDP attack analysis 2025.
So what passwords are these attackers using in these attempts?
Our research team took a look at a subset of over 4.6 million passwords collected over the span of a few weeks in October 2022 from our honeypot system – one of our sources for compromised passwords blocked by Specops Password Policy and Breached Password Protection.
The below password set is a list of the most common base terms found in recent attacks on our team’s honeypot network, including ones used to attack the RDP port.
Most Common Base Terms Used to Attack the RDP Port
The most common base terms found in passwords used to attack TCP Port 3389 in October 2022 were the following:
- password
- p@ssw0rd
- welcome
- admin
- passw0rd
- p@ssword
- pa$$w0rd
- qwerty
- user
- test
These base terms show some very basic password practices in the wordlists attackers are brute forcing Port 3389 with. Organizations that deploy the use of a custom dictionary that also prevents the use of leetspeak would go a long way to protect against the most common base terms used to attack this port.
Compare that with the most common base terms used to attack networks across multiple ports (including Port 3389) observed by our internal attack monitoring team in the same time period:
- password
- admin
- welcome
- p@ssw0rd
- qaz2wsx
- homelesspa
- p@ssword
- qwertyuiop
- q2w3e4r5t
- q2w3e4r
Most interesting about this larger dataset might be the inclusion of “homelesspa” – a password base term found in the 2016 MySpace leak, giving us insight into the lists used by attackers to attack networks. We also see this term in the NCSC Top 100k list published in 2019. This base term indicates that even if a wordlist or breach is “old” it is still worth protecting against as attackers are often compiling their attack lists from several different breach corpuses.
Our team also took a look at what patterns could be found in recent attacks on networks to help organizations design a more effective password security approach and noted the following:
- More than 88% of passwords used to attack these ports in October were 12 characters or less
- The most common password length found in this attack data was 8 characters at almost 24%
- Less significant patterns in password construction in this data – though passwords containing only lowercase letters were the most common character combination found at 18.82% of the set
Organizations looking to prevent the use of passwords like these could make use of password construction rules like implementing the use of passphrases, requiring a minimum length of 13 characters or more, or introducing length-based password aging. Those rules paired with a custom dictionary or compromised password check would be the best defense against passwords like these.
Securing the RDP Port from Brute Force Password Attacks
Organizations looking to secure the RDP port to protect against ransomware or other malicious activity should implement security best practices such as:
- Keep Windows servers and clients patched and up to date to protect against CVEs
- Check for misconfiguration – ensure the TCP port 3389 is using an SSL connection and not exposed directly to the internet
- Limit the range of IP addresses that can use RDP connections
- Add push-spam resistant MFA to RDP connections
- Block the use of weak and compromised passwords, especially those being used to attack RDP ports right now
Find Compromised Passwords Like These in Your Network
Today’s update to the Breached Password Protection service includes an update of over 26 million added to the list used by Specops Password Auditor.
You can download the latest Specops Password Auditor here. Specops Password Auditor does not store Active Directory data, nor does it make any changes to Active Directory.
Decrease Your Ransomware Attack Risk by Blocking These Passwords
With Specops Password Policy and Breached Password Protection, organizations can prevent the use of passwords like the ones our research team shared today and over 4 billion more known compromised passwords. These compromised passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC.
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk. See how with a demo or free trial.
(Last updated on March 18, 2025)
