This website uses cookies to ensure you get the best experience on our website. Learn more
Password length best practices
Table of Contents
When it comes to making strong passwords, the single most important factor is the length of the password. As long as a password isn’t easily guessable by other means (e.g. use of common words, username, repeating characters) length is your best friend for mitigating brute force attacks.
Let’s consider passwords that only use lowercase letters. For an 8 character password, there are 268 possible passwords, which might seem like a large number. And it is — 208,827,064,576 possible passwords – that’s 208 Billion. However, modern computers are exceedingly fast; a computer could churn through every possible password given these requirements in a few hours, a high-end multi-threaded machine might get that time-frame down to a few minutes or even a few seconds. To make the math easier, let’s say we have a really powerful computer that can churn through this list in exactly 1 minute.
Now consider if we added the traditional password complexity rules and we now require one each of an uppercase letter, a lowercase letter, a digit, a number, and special character but leave our length requirement at 8. This means each character position could include any of 26 (uppercase) + 26 (lowercase) + 10 (digits) + 32 (special characters available as keys on a US English keyboard, excluding alt codes, etc.) = 94 characters. For an 8 character password, that adds up to 948 possible passwords, or 6,095,689,385,410,816 — ~29,000 times as many possibilities as the all-lowercase password. So a computer that can brute-force our 208 billion all-lowercase passwords in a minute would take just under 3 weeks to get through all the 8-character complex possibilities. Impressive, but still far from bulletproof.
We also must consider the reality: users are human. So while there are 948 possible passwords, the set of actual passwords that humans might choose is likely much smaller than that. How many of your users do you think have passwords that looks like this:
Abcdef1!
If the first character is always an uppercase letter, characters 2-6 are lowercase letters, then characters 7 and 8 are always 1 and ! (does that look familiar?) – that leaves just 266 possible words:
[A-Z][a-z][a-z][a-z][a-z][a-z]1!
(26)(26)(26)(26)(26)(1)(1) = 308,915,776
That’s 308 Million possible passwords – significantly worse than our all-lowercase password. That virtual supercomputer that could check 208 Billion passwords in 60 seconds would take under a tenth of a second to brute-force guess a password in this set.
Considering that forced complexity isn’t perfect in theory and is potentially even worse in practice, let’s see what just increasing the length does to our possible passwords:
| Length | Complexity | Possible lowercase passwords | Time to guess (minutes) |
| 6 | All lowercase | 308,915,776 | 0.0015 |
| 7 | All lowercase | 8,031,810,176 | 0.038 |
| 8 | All lowercase | 208,827,064,576 | 1 |
| 9 | All lowercase | 5,429,503,678,976 | 26 |
| 10 | All lowercase | 141,167,095,653,376 | 676 |
| 11 | All lowercase | 3,670,344,486,987,780 | 17,576 |
| 8 | Complex (4 of 4) | 6,095,689,385,410,820 | 29,190 |
| 12 | All lowercase | 95,428,956,661,682,200 | 456,976 |
| 13 | All lowercase | 2,481,152,873,203,740,000 | 11,881,376 |
| 14 | All lowercase | 64,509,974,703,297,200,000 | 308,915,776 |
| 15 | All lowercase | 1,677,259,342,285,730,000,000 | 8,031,810,176 |
| 16 | All lowercase | 43,608,742,899,428,900,000,000 | 208,827,064,576 |
We see as we increase from 11 to 12 characters we fly right by the maximum possible 8-character ’complex’ password that used all possible uppercase+lowercase+digit+special characters.
As we continue increasing length — a 16 character password has a massive number of possibilities. Look at it this way: 8 characters gives us 208 billion possibilities, which we theorized would take one minute to crack. 16 characters gives us 208 billion times 208 billion possibilities, or put another way: 208 billion minutes to crack. A bit more math on that:
208,827,064,576 minutes / 60 = 3,480,451,076 hours
145,018,795 hours / 24 = 145,018,795 days
145,018,795 / 365 = 397,312 years
What is the standard for maximum password length?
Your passwords have to get quite long before you run into any limitations in the Windows world: the maximum length of a password supported by Active Directory is 256 characters. The maximum length of a password that a human user could actually type to log into Windows in 127 characters (the limitation is in the Windows GUI).
127 is probably quite impractical for a user to type, but might be good for admin accounts where passwords are checked out and copied and pasted from a password vault. Service account passwords that are almost never typed and possibly rarely changed (if ever) could stand to be longer still.
Applications that use AD/LDAP for authentication may have their own limits, unfortunately they are sometimes much shorter than we would like. If you do have an upper limit imposed by a 3rd party application, Specops Password Policy can help there by enforcing a maximum password age in AD to prevent users from choosing passwords that would be unusable in other applications.
What is the default minimum password length in Active Directory?
Default domain policy / password policy
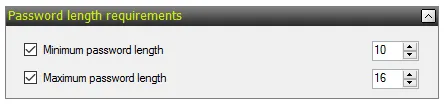
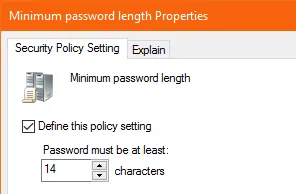
Typically configured either in your Default Domain GPO, or any other GPO linked directly at the root of the domain. You can set a maximum minimum length of 14 characters by this method (run a gpupdate on your PDC emulator for any changes to take effect).
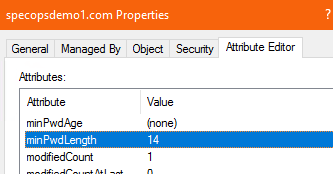
You can also edit the minPwdLength attribute in ADSI edit directly:
Fine-grained password policies
For setting longer minimum length requirements for different sets of users, you can use Fine Grained Password Policies (FGPP). Beginning in Windows 2012, FGPP also supports minimum lengths longer than 14 characters.
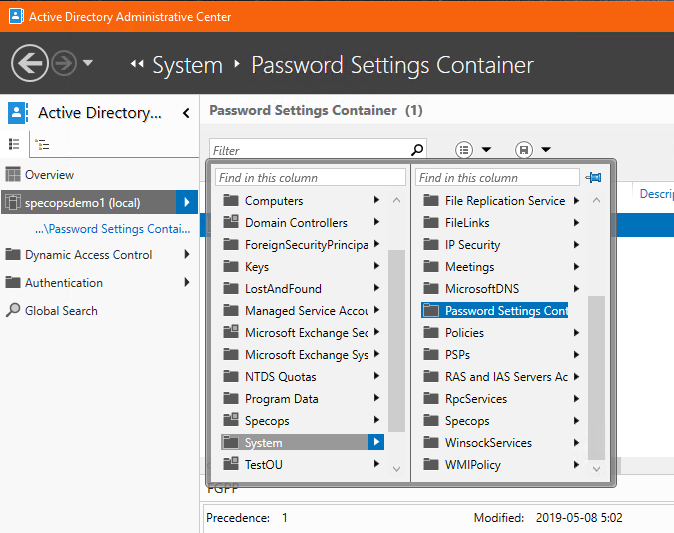
Creating a FGPP used to involve going into ADSIEdit and manually creating a Password Settings Container object there. However with Windows Server 2016 Microsoft added the Active Directory Admin Center, which streamlines the process considerably.
If ADAC is not installed, add it using Roles & Features wizard, or from an admin PowerShell:
>install-windowsfeature RSAT-AD-AdminCenter
In ADAC, navigate to System -> Password Settings Container under your domain.
In the Tasks area to the right, New -> Password Settings.
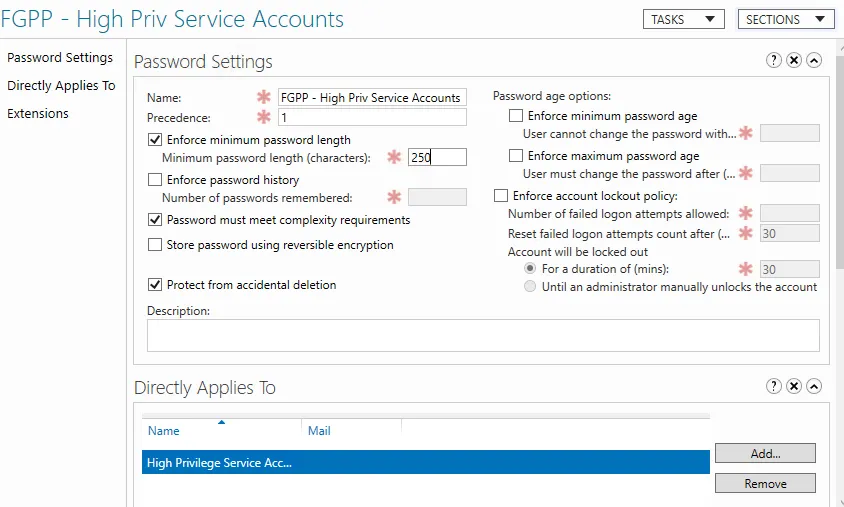
Configure your desired rule set, as well as add users or groups to the ”Directly Applies To” section.
The maximum password length here can be go all the way up to 255 characters (though again, watch out for limitations on password fields. For example: Logon credentials for Windows services cannot exceed 251 characters).
Now to set a password that long, a ”programmatic” interface such as PowerShell is ideal. Here’s an example (with the real password replaced by *s).
$newPasswordText = ”************************************************************** ********************************************************************************** **********************************************************************************” $newPassword = convertto-securestring -string $newPasswordText -asplaintext -force set-adaccountpassword -identity svc-password-test -newpassword $newPassword -reset
Long but easily guessed passwords – what to do
Now we have talked considerably about password length and why it’s important, but remember that’s not the entire story when it comes to modern password recommendations. A long password is a strong password, however it’s still not any good if it contains your username or other easily guessable words such as the name of the organization. If my password were ”SpecopsSoftware1!” it’s quite long, and that’s good. However if someone wanted to guess my Specops account password, this would be a fairly easy guess. Similarly, if I was allowed to chase a minimum length requirement with a repeating character — e.g.”Specops11111111” — that wouldn’t be much harder to guess than ”Specops1”
With Specops Password Policy, you can help ensure that your longer password length requirement isn’t entirely for naught. You can block common dictionary words – case insensitive, and with detection for common character substitution), detect and block repeating characters. So ”SpecopsSoftware1!” would be blocked, as would ”Specops11111111” or even ”Sp3c0psS0ftw@re1!”
With Specops Breached Password Protection you can also block over 4 billion known leaked passwords. Although, there are hundreds of billions of possible password combos looking at words alone, a long password is no good if it’s known to hackers.
Length-Based Password Aging
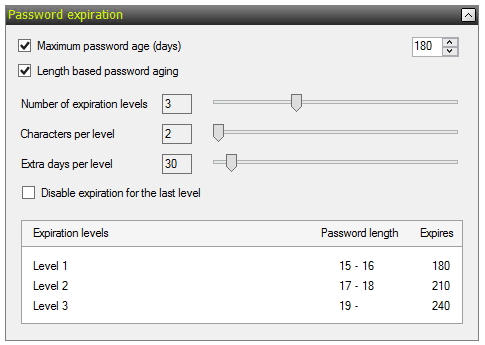
With Specops Password Policy 7.1 we introduced a new feature: length-based password aging. With this feature enabled, you can reward you users for selecting a longer password by extending the time until they’ll need to change their password again or even letting them keep that long password forever.
Check out this recent review of Specops Password Policy for more information about the product.
(Last updated on March 18, 2025)