This website uses cookies to ensure you get the best experience on our website. Learn more
Secure your Active Directory passwords
Verizon’s Data Breach Investigation Report found stolen credentials are involved in 44.7% of breaches. Specops Password Policy lets you greatly reduce your organization’s attack surface through a simple interface that easily integrates with Active Directory. Admins can block end users from creating weak passwords and continuously scan for passwords that have become compromised through data breaches or password reuse.
-
Continuously block over 4 billion breached passwords
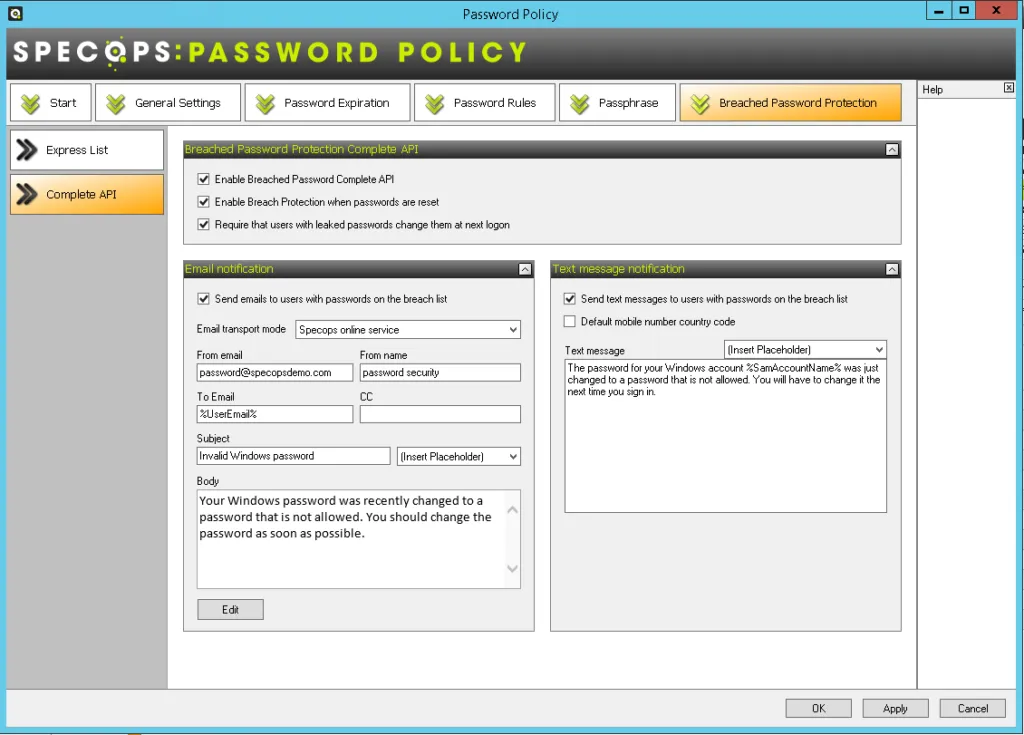
- Breached Password Protection feature blocks and removes over 4 billion unique compromised passwords
- Continuous scan feature finds breached passwords daily, instead of only at password change or reset
- Includes passwords from real-time attack monitoring system that monitors live brute force attacks, plus malware-stolen data from our human-led Threat Intelligence team
-
Better user experience for fewer service desk tickets
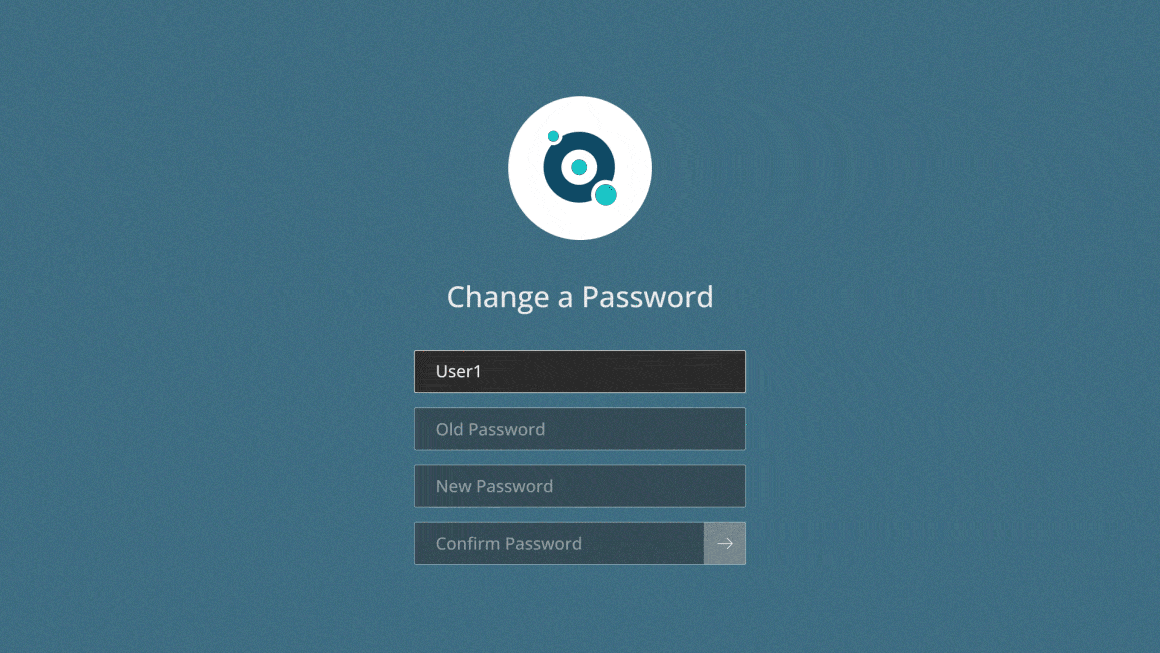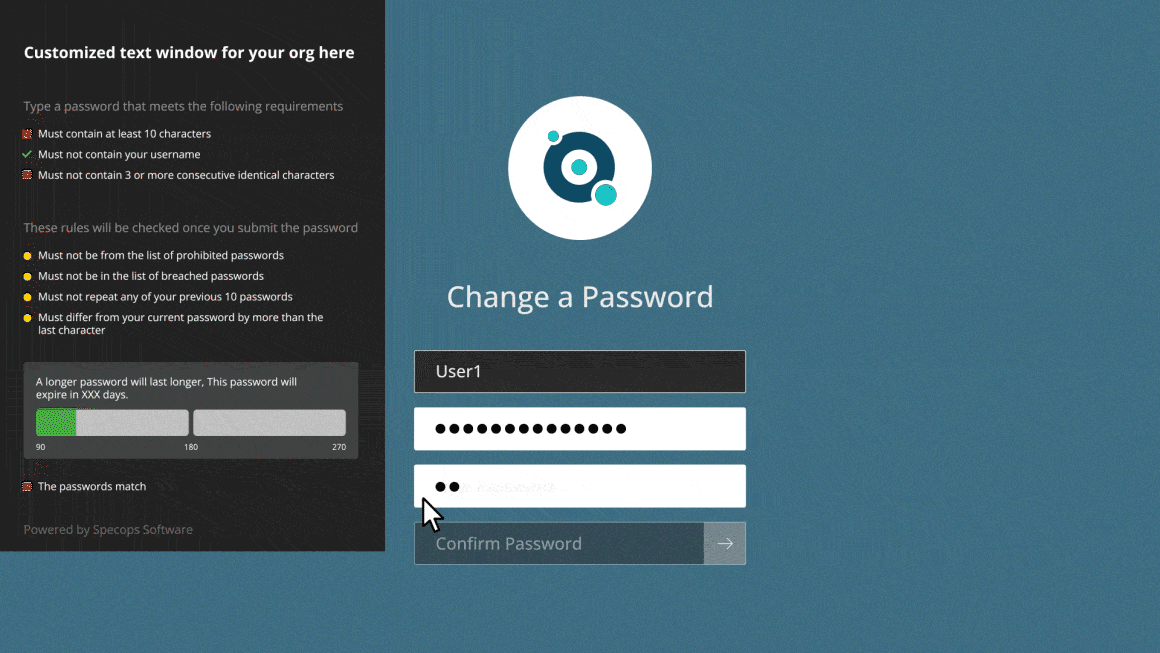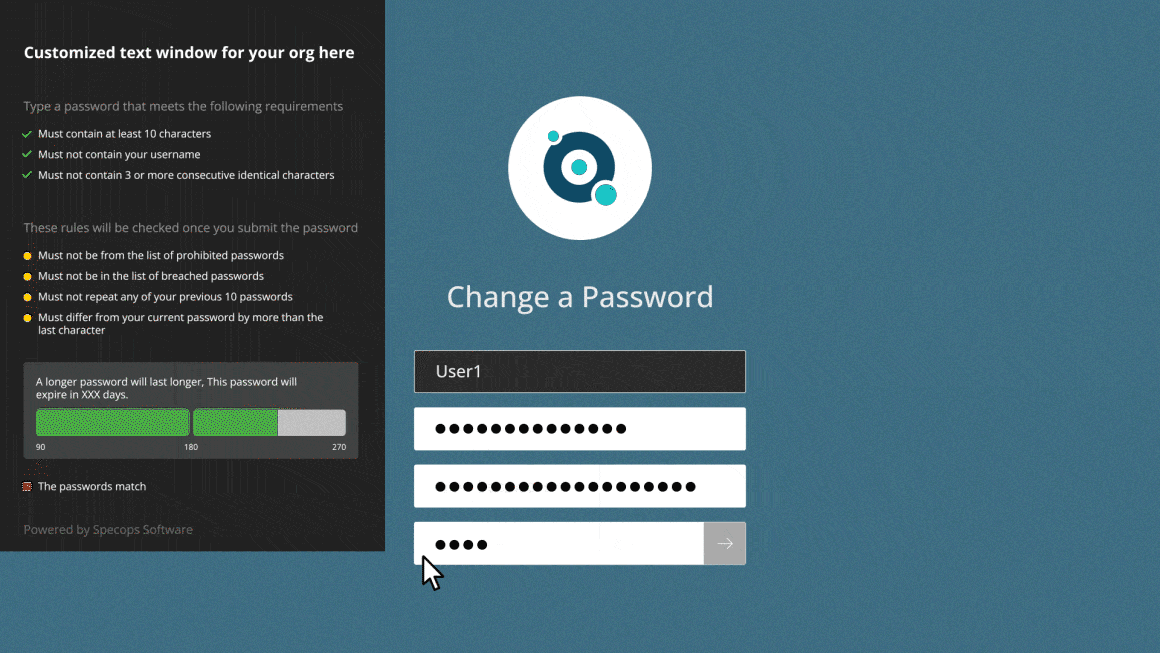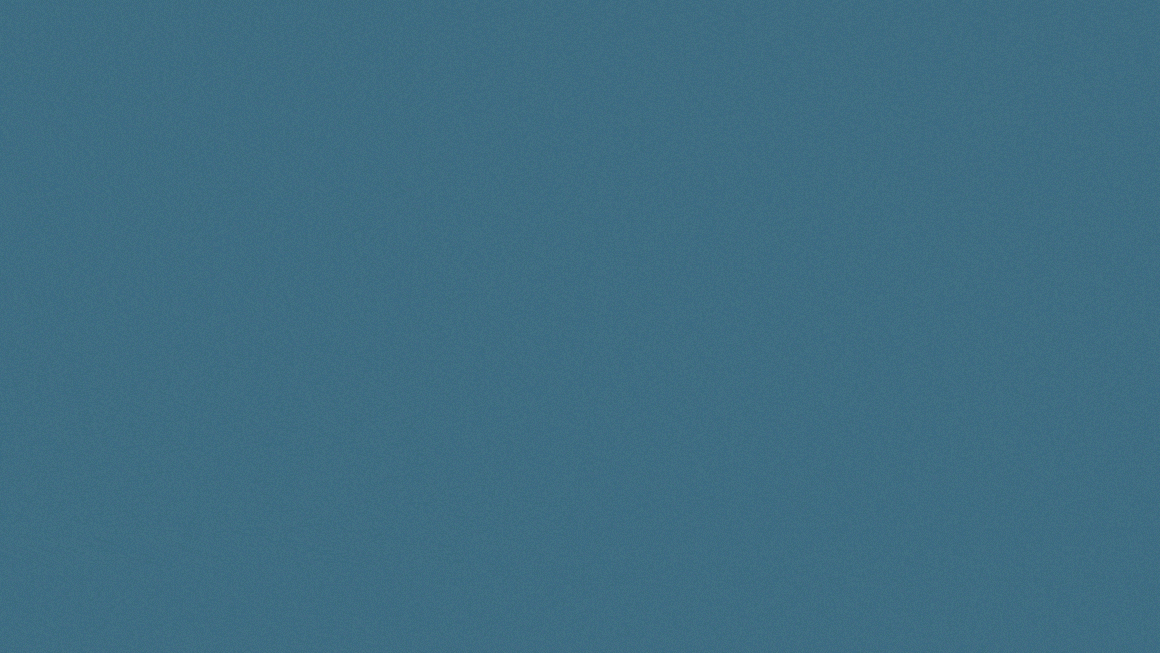
- Dynamic feedback reacts to user input, guiding them to create strong passwords they can actually remember
- Customizable SMS and/or email notifications to alert users if their password has been compromised
- Easy-to-understand, simple user experience avoids password frustration and fatigue, meaning fewer calls and emails to the support desk
-
Quickly create and enforce compliant password policies
- Readymade compliance templates and reporting tool ensure you match standards
- Comply with cybersecurity regulations (e.g. NIST, CJIS, NCSC, ANSSI,) and privacy regulations (e.g. CNIL, HITRUST, PCI)
Features
We check your Active Directory on a daily basis against a continuously updated list of known breached passwords – not just at expiry or reset. See how Specops compares head-to-head with Azure AD.
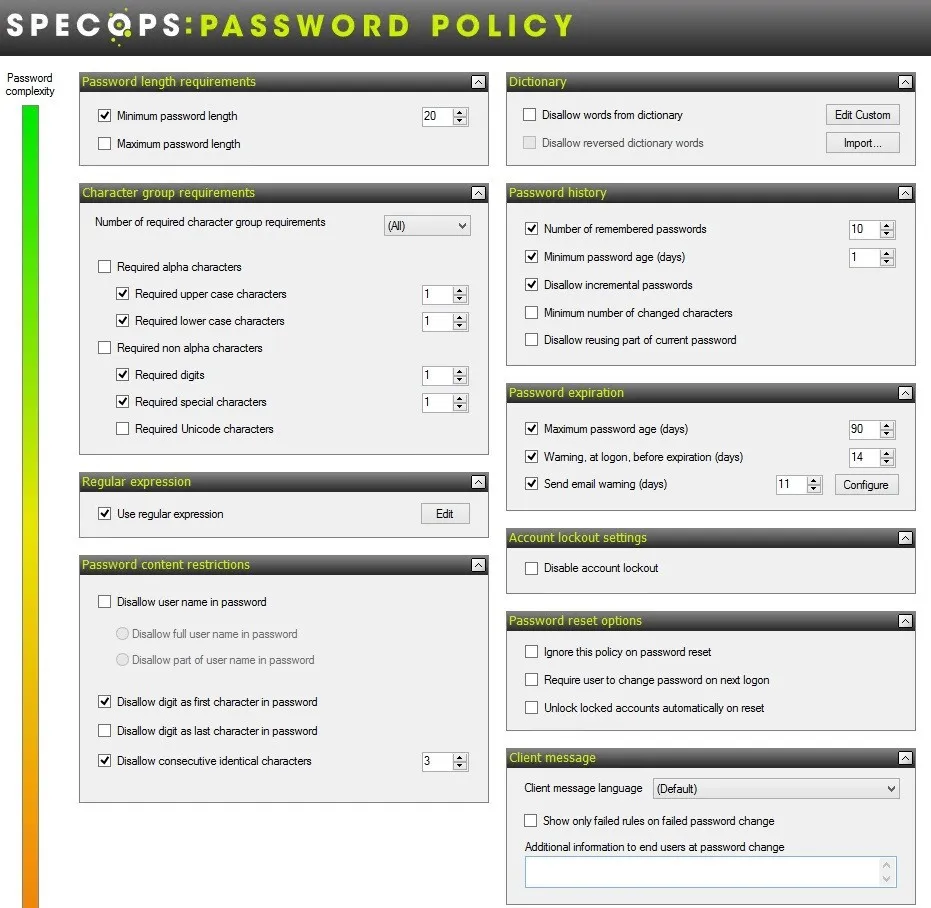
- Continuous scanning against list of 4 billion (and counting) compromised passwords
- Create an unlimited custom dictionary of blocked words unique to your organization – use Regex to further customize requirements
- Block user names, display names, consecutive characters, incremental passwords, and reusing parts of current passwords to protect against targeted attacks
- Informative end-user client messaging at failed password change that reduces calls to the helpdesk
- Our client supports wrapping, making it easy to pair with your chosen MFA solution
- Granular, GPO-driven targeting for any GPO level, computer, user, or group population
- Prevents the use of passwords being used in attacks happening right now
- Length-based password expiration with customizable email notifications that rewards users with more time before the next reset when they set longer passwords
- Real-time, dynamic feedback at password change with the Specops Authentication client
- Over 25 languages supported including English, French, German, Spanish, and Chinese
Gartner customer reviews
See what satisfied customers on Gartner Peer Insights had to say after buying and deploying Specops Password Policy.
Want a live demo? Let’s talk!
See how Specops Password Policy can fit in with your organization with one simple Active Directory integration. Complete our quick info form and choose a convenient time to meet.
Need more info?
FAQs
A strong password policy encourages unique passwords that are hard to guess. A strong Active Directory Password Policy protects the network from unauthorized access.
Most cybersecurity regulations recommend screening new passwords against a list of known compromised passwords. Find more detailed advice on best practice for Active Directory security in our blog.
A weak password policy in Active Directory does not disallow commonly used words nor does it block known breached passwords.
Active Directory does not check for breached passwords out-of-the-box. With some configuration, Administrators can check Active Directory passwords against the Have I been Pwned password list.
The fine-grained password policy in Active Directory is not compliant with common cybersecurity requirements. With a third-party tool like Specops Password Policy, system admins can easily enforce a compliant password policy.
Downloads and resources
- Impact of running Specops Password Policy on Active DirectoryWe are often asked about the technical impact of using our solutions on Active Directory (AD), and other services. In this blog post, we will look at the impact of Specops Password Policy and Breached Password Protection. See part 1 of this blog here, where we look at the impact of Specops Password Auditor on…
- Specops Password Policy comparison and priceIn the market for a third-party password policy solution? If an audit has revealed poor password practices, you may look to Microsoft Fine-Grained Password Policy (FGPP) for additional flexibility over default domain password settings. Unfortunately, FGPP still lacks a lot of the capabilities for meeting auditor requirements, regulatory standards, and the latest password recommendations from…