This website uses cookies to ensure you get the best experience on our website. Learn more
Checking for Pwned Passwords in Active Directory
Table of Contents
If you are trying to fulfill a regulation requirement like that of NIST, you might find yourself tasked with attempting to set up your Active Directory environment to check for leaked passwords against an external password deny list. For many, Have I Been Pwned (HIBP) is the list they want to check against.
HIBP is one of the largest free collections of pwned passwords and accounts that can let you know if your email address or password has been leaked.
Some of the biggest leaks in the HIBP list include:
- 772,904,991: Collection #1 accounts
- 763,117,241: Verifications.io accounts
- 711,477,622: Onliner Spambot accounts
- 622,161,052: Data Enrichment Exposure from PDL Customer accounts
- 593,427,119: Exploit.In accounts
Troy Hunt, the man behind the collection, lists the current count of pwned passwords in HIBP around 800 million. (Our own Specops Breached Password Protection compromised password list is currently about four times that at over 4 billion leaked passwords).
Easy enough to check if an individual email address has been breached:
or an individual password:
However, things get more complicated if you’re looking to check the credentials for your Active Directory users against this list.
For starters, doing this manually would take forever. Never mind that if you’re following good security practices, you shouldn’t have any personal knowledge of your users’ passwords to then individually search them.
So, if your heart is set on checking your AD against the HIBP list, you have two options: the API and downloading the lists.
Checking Active Directory passwords against the HIBP API
The HIBP API after some configuration could help you check your Active Directory against its list.
With a recent update to the HIBP list, Troy introduced the use of k-Anonymity, which means you no longer have to send the entire hash via the API. You can now search the database by range – using the beginning of an SHA1 hash, then using the API response to check whether the rest of the hash exists in the database.
JacksonVD wrote a detailed post on how to set this up with Active Directory.
A guide that got the approval of Troy Hunt himself.
But that doesn’t help with continuous protection; you’d have to re-run this with each new addition to HIBP as well as regularly to check any changed AD passwords against the existing list.
On top of that, security-wise, you might prefer to have an on-premise list you can check your AD credentials against rather than open your Domain Controllers up to (an even slight) compromise and subsequent infection risk.
Checking Active Directory passwords against an on-prem HIBP download list
For those who prefer to not use the API, whether for security reasons or concerns over availability, HIBP does offer a download option of its list.
“The entire set of passwords is downloadable for free below with each password being represented as either a SHA-1 or an NTLM hash to protect the original value (some passwords contain personally identifiable information) followed by a count of how many times that password had been seen in the source data breaches.”
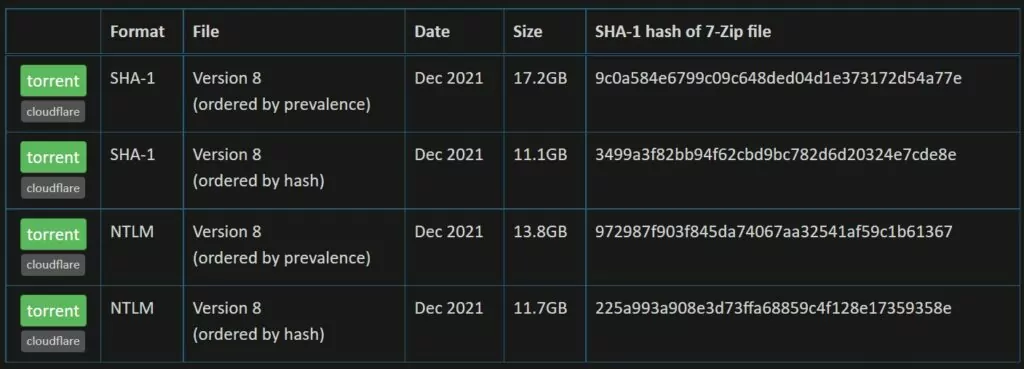
JacksonVD wrote another guide that covers the steps for comparing your AD against a local store of the HIBP list here.
While JacksonVD’s instructions can get you there, you still might not want to go that route due to lack of sign-off on such an approach or lack of desire to set that up technically. Even still, you might need something simpler from an auditing perspective.
Find out how many Active Directory passwords are pwned
Specops Password Auditor is a free tool that checks passwords against our list of breached and vulnerable passwords. This list, known as the Breached Password Protection Express List, includes compromised passwords from sources such as the HIBP password list, other leaked lists, live attack data, and more.
The Auditor also provides a full view of user and password policy information, including: stale or inactive admin accounts, password expiration, and password policy compliance against industry standards, such as NIST. From a single view, you can identify vulnerabilities that can assist you with your security plan.
Specops Password Auditor is a read-only program, and can be run from any domain joined workstation. Check out this blog on the technical impact of using Specops Password Auditor. Remember, you can download it for free from: https://specopssoft.com/product/specops-password-auditor/#tryfree
Ban pwned and other vulnerable passwords in Active Directory
With Specops Password Policy’s Breached Password Protection, you get a comprehensive list of leaked passwords (over 4 billion and counting), as well as passwords used in real attacks today. You get a more secure way to check your Active Directory user passwords against a NIST compliant compromised password list.
Specops Password Policy with Breached Password Protection comes in two versions: Express and Complete. Both check passwords against our leaked list during password change, and blocks users from selecting vulnerable passwords.
With Express, your AD users’ passwords are checked during password change against a streamlined version of our complete list that’s available for on-prem use and notifies immediately if the password they’ve selected is compromised.
With Complete, your AD users’ passwords are checked during password change against our complete list (over 4 billion and counting) that’s available in the cloud and notified via email if the password they’ve selected is compromised. The user will be asked to change their password at next logon.
With both Express and Complete, your users get access to speedy password breach checks during password change as well as the comprehensive security check that comes with Complete. Anytime more breached passwords are added to the Breached Password Protection list, users with vulnerable passwords will be notified and forced to change their password.
Looking for a password deny list that’ll help you comply with regulations from organizations like NIST, but is also more comprehensive and easier to set up than HIBP? Contact us to see if Specops Password Policy and Breached Password Protection are the right fit for your Active Directory security needs.
(Last updated on March 18, 2025)



