What is length based aging and how is it used and implemented?
What is it?
Length based aging is a system that rewards users for having longer and more secure passwords.
How does it work?
It works by adding additional days in which the password will expire based on how many characters are in the password. In this example below, the max password age is set to 90 days, so any password regardless of length would expire under a normal password policy after 90 days. With length based aging, 90 days is the base level for any password between 8-12 characters in length. In this instance, if the password is 13 or more characters, 30 additional days would be given before the password expires making it 120 days instead of 90. You can read more about the settings to configure your policy here.
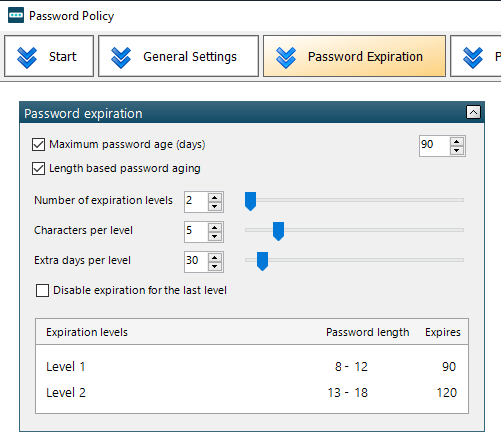
How do I implement this in my environment?
A couple of things to consider:
- Ensure that the default domain policy is set to 1 day higher than the highest tier of your length based aging policy. In the example above, the highest tier expires after 120 days so we will set our default domain policy max password age to 121.
- If you have the setting “Disable expiration for the last level” enabled, set your default domain policy max password age to 0.
Note: if the default domain policy is not adjusted accordingly, it can cause passwords to expire prematurely. If you do not want to modify the default domain policy, you can filter it out by using a bypass policy.
1.Ensure that whatever groups or users you want to be able read custom expirations associated with length-based password aging policies to are a member of this group. This group will need to be created within the product and managed in Active Directory Users and Computers:
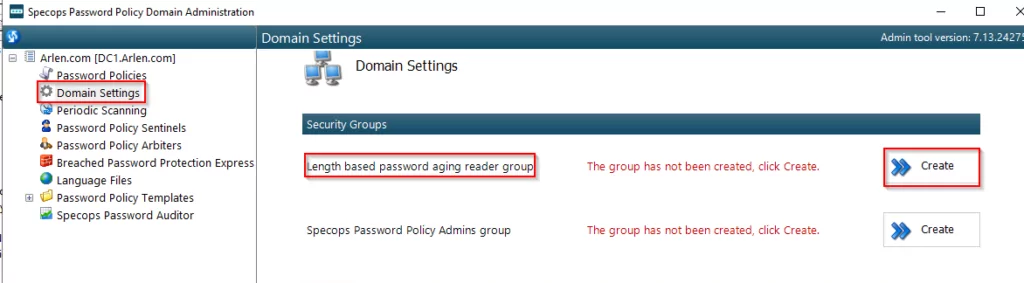
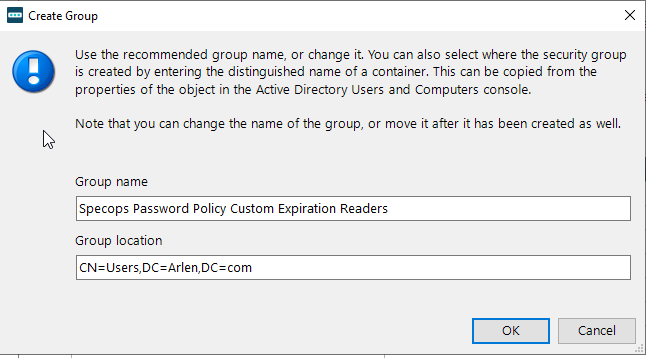
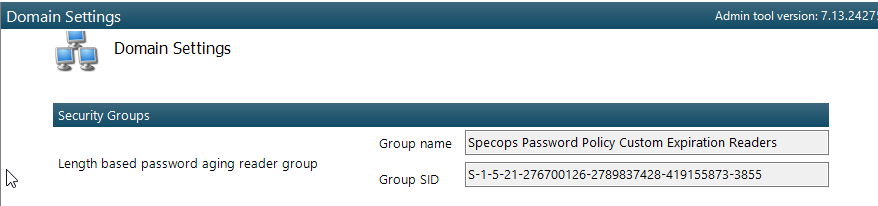
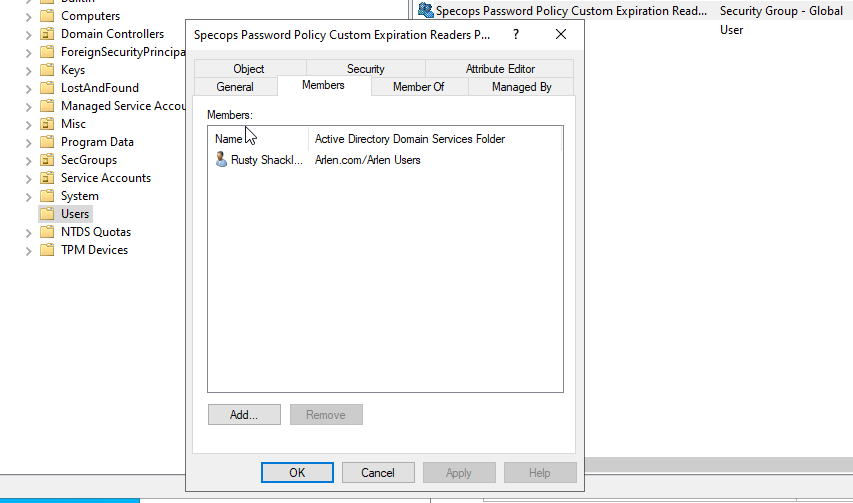
2. Users will then have to reset their password in order for the length based aging policy to take effect. If a user does not reset their password after a length-based password aging policy is implemented, they will be subjected to the Level 1 password Expiration (in the example 90 days).
How can i tell if a user is affected by a length based aging policy?
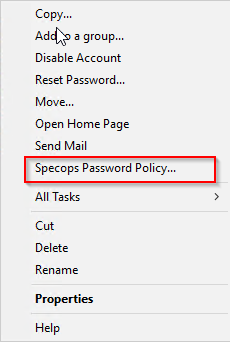
Look in Active Directory Users and Computers by right clicking on a user in Active Directory Users and Computers:
Please note this option will only be available if the following are installed on the same system, you are viewing this from:
- Active Directory Users and Computers
- Specops Password Policy Domain Administration
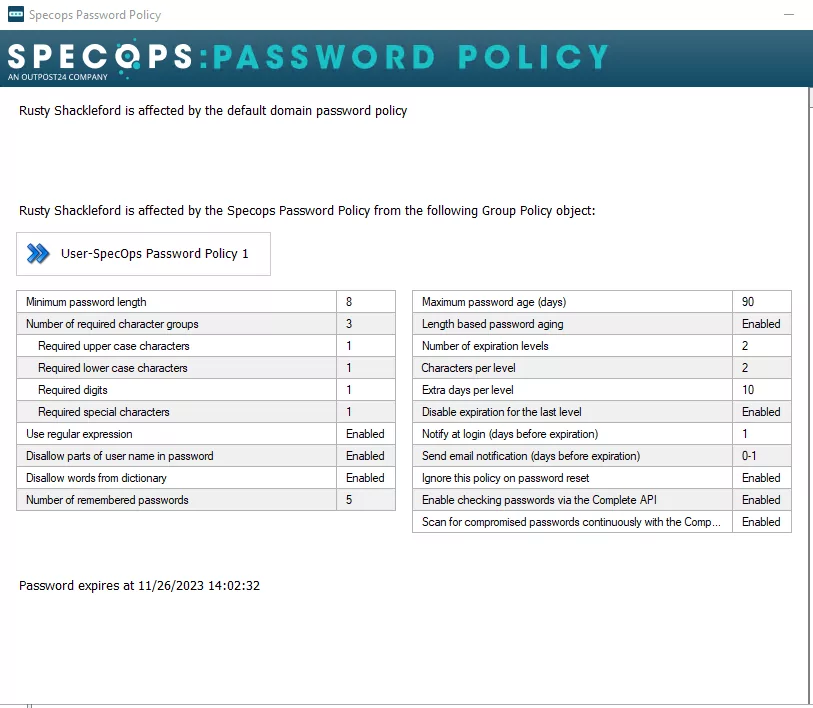
You can also use PowerShell or Specops Password Auditor which is explained in detail here.
How to validate the length of expiration
Ensure these options are selected:
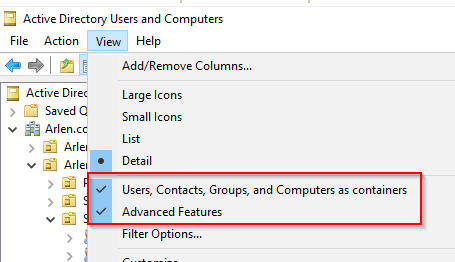
then locate the user with active directory and expand the user object and look at the properties of the specops-spp-pwdHistory object. Looking at the attribute tab we take note of what value is in the flags attribute. This value is indicative of the amount of days associated with the tier in which the password expires.
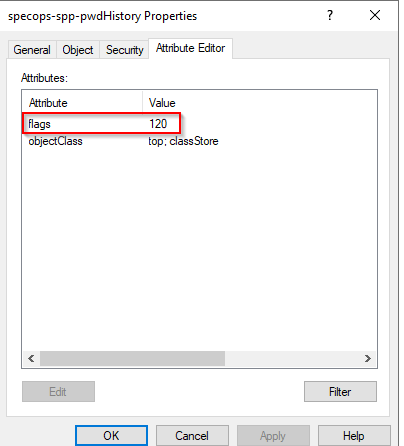
If it is set to a value of 2147483647, this indicates that the length-based password aging policy was set to disable expiration for the last level and the user’s password was long enough that it will not expire.
Note: the value 2147483647 was not chosen at random here: https://en.wikipedia.org/wiki/2,147,483,647
