Understanding Active Directory Password Expiration with Specops Password Policy
In this article we will review how to predict when users’ passwords will expire when affected by a Specops Password Policy, as well as troubleshoot if passwords are not expiring when expected.
In general, it is good to be aware that any Active Directory native tools for password expiration will not be aware of Specops Password Policy and therefore may produce results that are inconsistent with the settings configured there. For example, the ‘net user’ command and the msDS-UserPasswordExpiryTimeComputed attribute on user accounts will only show the expected password expiration according to your AD domain password policy and/or fine-grained password policies; this is because while Windows does allow for password filters to handle password expiration it not allow any modification of these built-in tools/attributes.
While Active Directory will continue to expire passwords based on its own policies even when Specops Password Policy is installed, Specops Password Policy also does its own calculation for password expiry based on the following:
- pwdLastSet attribute on the user account
- Maximum Password Age as defined in the Specops Password Policy applied to the user account
- Optionally: variable length-based password age if it is configured in your policies and users have taken advantage of that feature
Both AD and Specops will respect the ‘Password Never Expires’ flag. When troubleshooting password expiry please confirm this flag is not set on the users in question before proceeding.

Permissions Required
An administrator should have the following access rights in order to effectively troubleshoot password expiration:
- Read access to any Fine Grained Password Policies in the domain — typically this is restricted to Domain Admins however a Domain Admin can grant access to other groups.
- If you are unsure if you have any Fine Grained Password Policies, check in Active Directory Administrative Center or Active Directory Users and Computers MMC under System/Password Settings Container. If this container is empty you do not have any fine-grained password policies. If there are entries here confirm you able to view the properties of each.

- If using Variable Password Age in Specops Password Policy, the user running Specops Password Auditor must be a member of the Length Based Password Aging Reader group. The group name will be displayed in the Password Policy Domain Administration tool. You can manage its membership via Active Directory Users and Computers. In environments not using the length-based password aging feature this group may not be defined; this is expected.

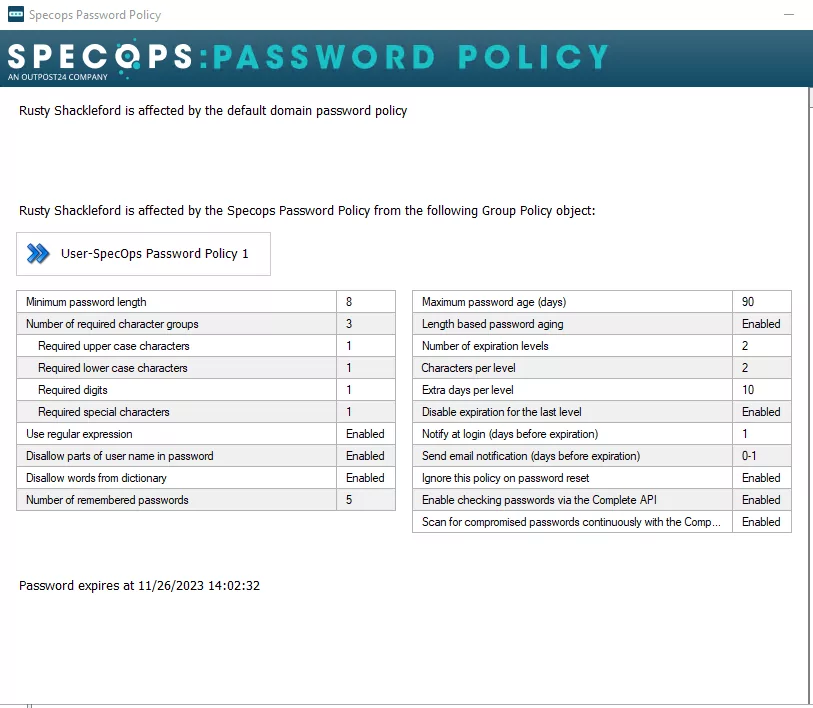
It is also important to note that if a fine-grained password policy is being used to apply a Specops policy to users, you will see the warning below, which can be disregarded as since this is referencing that this policy is unaware of the default domain policy settings because it is using a fine-grained policy instead.

Using Specops Password Auditor
The easiest way to see when users’ passwords will expire is to use Specops Password Auditor. The Password Auditor scan results will include a report of all users whose passwords are expected to expire within the next 365 days. The user running Password Auditor must have access to both fine grained password policies and be a member of the length based password aging reader group as discussed earlier in this article.
Using Active Directory Context Menu
This will be available on a machine with Active Directory Users and Computers and the Password Policy Domain Administration tools install. This will give the ability to check individual users by right clicking them in Active Directory Users and Computers, and using the context menu:
Using PowerShell
Troubleshooting an individual user may be a more effectively done through PowerShell. This will also offer a closer view into both Active Directory and Specops Password Policy calculate password expiration. Active Directory and Specops Password Policy process password expiration separately; of the expiration dates/times calculated here for AD and Specops Password Policy expiration, the user’s password will always expire on the earliest of the two.
Note: this section will make use of both the ActiveDirectory and Specops.SpecopsPasswordPolicy PowerShell modules. ActiveDirectory can be installed via Roles and Features or Windows RSAT Tools for Active Directory. The Specops.SpecopsPasswordPolicy module is installed with the Password Policy Admin Tools.
Active Directory Password Expiration
You can query AD directly when the password will expire — the msDS-UserPasswordExpiryTimeComputed attribute on user accounts automatically consider both the AD default password policy and fine-grained policies. It is stored in ‘filetime’ format, so we must do a bit of extra work to convert that into readable UTC time:
get-aduser username -properties msDS-UserPasswordExpiryTimeComputed | select @{Name="msDS-UserPasswordExpiryTimeComputed";Expression={[datetime]::FromFileTimeUTC($_."msDS-UserPasswordExpiryTimeComputed")}}
For example:
PS C:> get-aduser demouser -properties msDS-UserPasswordExpiryTimeComputed | select @{Name="msDS-UserPasswordExpiryTimeComputed";Expression={[datetime]::FromFileTimeUTC($_."msDS-UserPasswordExpiryTimeComputed")}}
msDS-UserPasswordExpiryTimeComputed
-----------------------------------
2022-12-24 23:30:13
If the result here is not what is expected from Active Directory, double check your domain and fine-grained password policies. Note the max password age will be expressed in Days.Hours:Minutes:Seconds format. If the value returned is blank, the user’s password does not expire; assuming you have already verified the ‘password never expires’ option was enabled for this user, this means the Active Directory password policy is configured to never expire passwords.
To check the Default Domain Policy max password age:
Get-ADDefaultDomainPasswordPolicy | select MaxPasswordAge
To list all Fine Grained Password Policies and their MaxPasswordAge setting:
Get-ADFineGrainedPasswordPolicy -filter * | select Name,MaxPasswordAge,AppliesTo | fl
To list only the Fine-Grained password policy applied to your user and its MaxPasswordAge setting. If this command returns no results the user is not affected by a fine-grained password policy:
Get-ADUserResultantPasswordPolicy -identity username | select Name,MaxPasswordAge,AppliesTo | fl
Examples:
PS C:> Get-ADDefaultDomainPasswordPolicy | select MaxPasswordAge
MaxPasswordAge
--------------
999.00:00:00
PS C:> Get-ADFineGrainedPasswordPolicy -filter * | select Name,MaxPasswordAge,AppliesTo | fl
Name : FGPP for Admins
MaxPasswordAge : 30.00:00:00
AppliesTo : {CN=Domain Admins,CN=Users,DC=specopsdemo1,DC=com}
PS C:> Get-ADUserResultantPasswordPolicy -identity demouser | select Name,MaxPasswordAge,AppliesTo | fl
PS C:> Get-ADUserResultantPasswordPolicy -identity demoadmin | select Name,MaxPasswordAge,AppliesTo | fl
Name : FGPP for Admins
MaxPasswordAge : 30.00:00:00
AppliesTo : {CN=Domain Admins,CN=Users,DC=specopsdemo1,DC=com}
If in either case the maxPasswordAge value is set to 00:00:00 this indicates passwords never expire for the users affected by that policy.
Specops Password Policy Password Expiration
For Specops Password Policy we must calculate the expected password expiration time based on the pwdLastSet attribute and the policy configuration.
First we must check which Specops password policy the user is affected by, and which expiration settings are configured within that policy.
get-passwordpolicyaffectinguser username | select -expand passwordpolicy | select MaximumPasswordAge,EnableVariableExpiration | fl
Example:
PS C:> get-passwordpolicyaffectinguser demouser | select -expand passwordpolicy | select MaximumPasswordAge,EnableVariableExpiration | fl
MaximumPasswordAge : 100
EnableVariableExpiration : TrueIf the MaximumPasswordAge value here is blank, then Specops Password Policy affecting the user will not expire passwords. If there are no results at all, the user is not affected by a Specops Password Policy.
If EnableVariableExpiration is True, we must check if the user’s current password was sufficient to be affected by the length-based aging policy. If a user affected by a Specops password policy with length-based aging enabled sets a password of sufficient length to qualify for a longer expiration, we write that user’s new maximum password age to a leaf object under their user account. This attribute is accessible only to domain controllers and members of the length-based password aging reader group.
$userDN = (Get-ADUser username).distinguishedName
get-adobject "CN=Specops-SPP-PwdHistory,$userDN" -properties flags | select @{Name="UserMaxPasswordAge";Expression={$_.flags}}
Example:
PS C:> $userDN = (Get-ADUser demouser).distinguishedName
PS C:> get-adobject "CN=Specops-SPP-PwdHistory,$userDN" -properties flags | select @{Name="UserMaxPasswordAge";Expression={$_.flags}}
UserMaxPasswordAge
------------------
160
If the userMaxPasswordAge (stored in the flags attribute) is blank or if the Specops-SPP-PwdHistory leaf object does not exist, the user’s maximum password age is as defined in the MaximumPasswordAge value in the policy. If it is set to a value of 2147483647, this indicates that the length-based password aging policy was set to disable expiration for the last level and the user’s password was long enough that it will not expire.
Note: the value 2147483647 was not chosen at random here: https://en.wikipedia.org/wiki/2,147,483,647
To determine when Specops Password Policy will expire the user’s password, we need to retrieve the timestamp when the user’s password last set then add the number of days per either the default or variable maximum password age:
get-aduser username -properties pwdlastset | select @{Name="PasswordExpiresSpecops";Expression={[datetime]::FromFileTimeUTC($_.pwdlastset).addDays(maxpasswordage)}}
Example:
PS C:> get-aduser demouser -properties pwdlastset | select @{Name="PasswordExpiresSpecops";Expression={[datetime]::FromFileTimeUTC($_.pwdlastset).addDays(160)}}
PasswordExpiresSpecops
----------------------
2020-09-06 23:30:13One final caveat to be aware of here is Specops will not expire the password at this moment of the date/time here. The Password Policy Sentinel on the domain controller holding the PDC Emulator role runs a task once every 24 hours (by default at midnight local time) to expire passwords. The Sentinel will check every user affected by a password policy and if the date/time calculated by this algorithm has passed, the user’s account will be set to require password change at next logon.
