Enabling Kerberos for Specops Authentication
In order to use Kerberos in Specops Authentication, you will need to uninstall the Specops Authentication Gatekeeper and the Specops Authentication Gatekeeper Administration applications and then install a new instance of each gatekeeper in your environment and use a Group Managed Service Account (gMSA).
This is recommended as Microsoft will start phasing out NTLM. It is important to note that when doing this, each gatekeeper will need to be restarted in order to get the necessary tokens to access the gMSA account.
If you are not sure or would like to confirm if you already have KDS Root Key type the following into Powershell:
Get-KdsRootKeyIf a key is present you will see the information below and if not your results will be blank:

If your results are blank, you can generate a KDS root key by typing the following. Note that it will take up to 10 hours for this to replication throughout the environment before it becomes active.
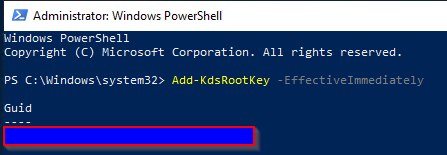
Add-KdsRootKey -EffectiveImmediatelyand getting the below result:
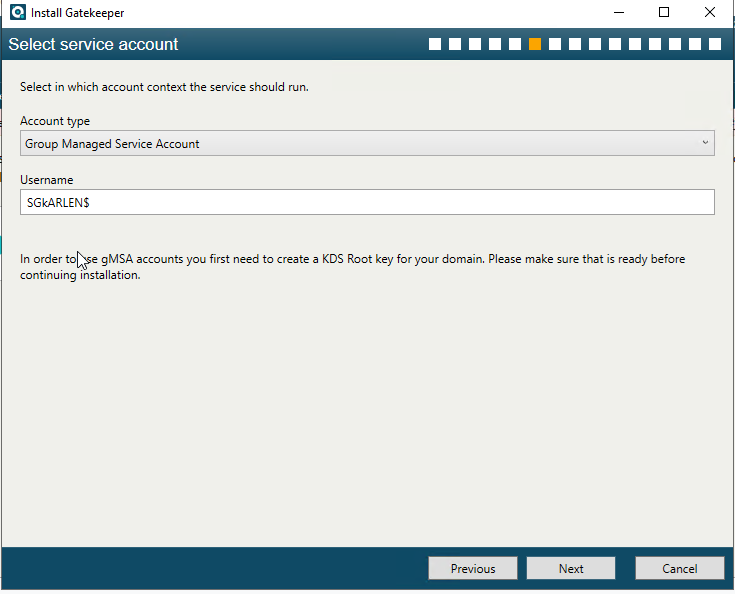
Once that is done, we can proceed with the removal and install of all the gatekeepers one by one to switch them over, taking note that if you only have one gatekeeper, it is important to have a least one back up and this step will allow you to spin up an additional gatekeeper. When you get to this step in the installation process, you will want to change the Account type to Group Managed Service Account.
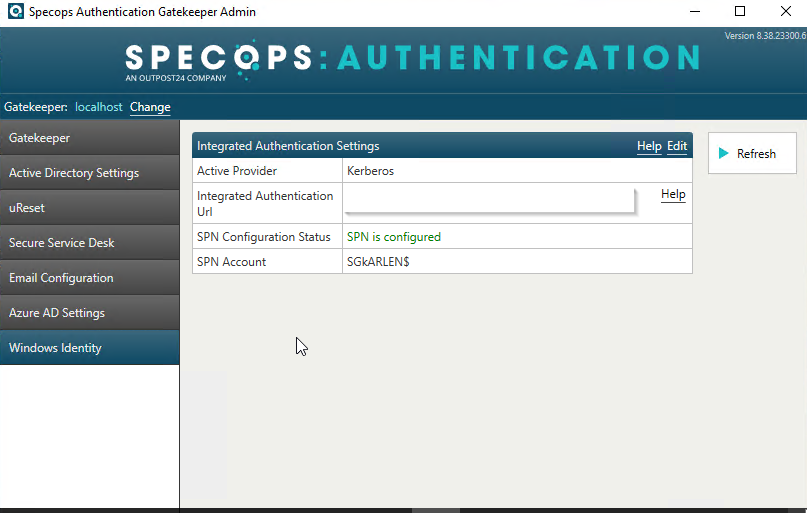
Once the setup is complete, you can go to the Windows Identity tab on your gatekeeper and switch the Integrated Authentication Settings Active Provider to Kerberos
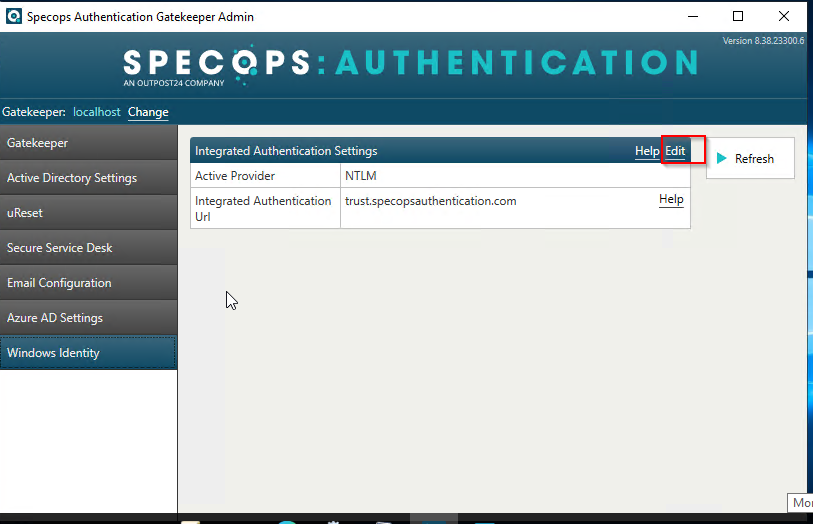
and you will be provided with the below and you will need to add the Integrated Authentication Url to the local intranet zone.