This website uses cookies to ensure you get the best experience on our website. Learn more

Search for custom AD attributes from the helpdesk
Table of Contents
From Specops Password Reset (SPR) 6.4 and onwards, there will be a new registry setting that will allow you to specify the AD attribute to search from the helpdesk.
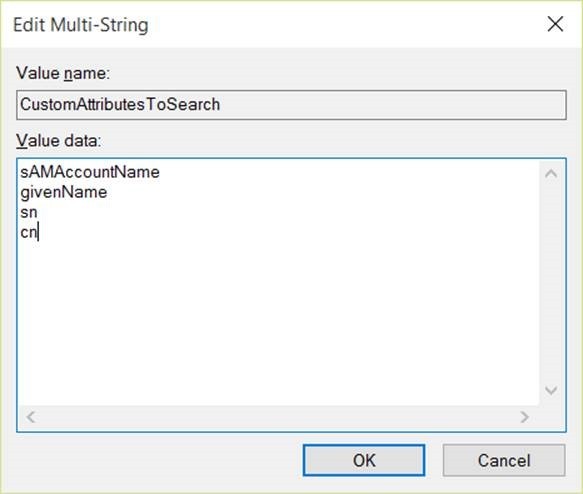
If the registry setting is not set, the default will be Ambiguous Name Resolution (ANR), a consolidation of some common attributes on the user object. Previous version of SPR searched for “sAMAccountName”, “givenName”, “sn” and “cn”. The difference now is that we will now also search “displayName” by default.
For more details about ANR, click here!
The new setting in the registry is a multi-string value called “CustomAttributesToSearch” under “HKEY_LOCAL_MACHINE\SOFTWARE\Specopssoft\Specops Password Reset\Server”.
The behavior for SPR 6.3 and older would have values configured in the following way:
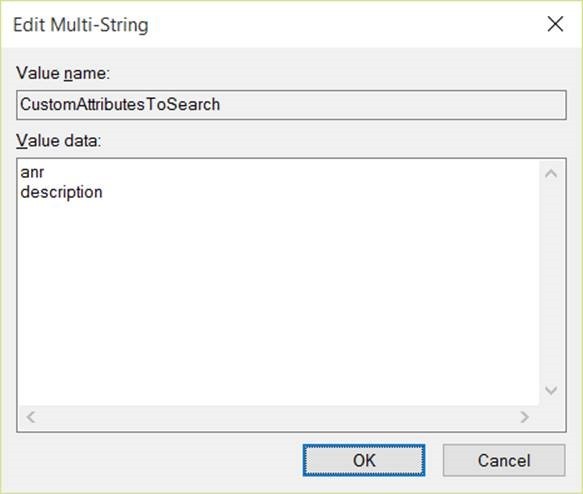
To use ANR and a custom attribute, you will need both “anr” and “description” in the value data.
Note: You need to have both “anr” and “description”. If only “description” is used, it would replace the default value ANR.
This feature could be useful for some of our customers. For example, a helpdesk user in a school may want to list all students in a class. If they, for instance, have the student’s class stored in ‘description’ it would be possible to search for all students in class 7C by typing the AD attribute ‘7c’ in the helpdesk search.
Find out more about our secure help desk identity verification solution Specops Secure Service Desk.
(Last updated on January 21, 2025)