This website uses cookies to ensure you get the best experience on our website. Learn more
What’s Entra ID? Azure AD’s latest name change explained
Table of Contents
If you’ve seen reference to ‘Microsoft Entra ID’ recently, it’s because Microsoft have rebranded Azure Active Directory (Azure AD) to become part of the Microsoft Entra product family. It will be a gradual process that started on July 11th and will finalize towards the end of 2023, so IT teams should start seeing the name change appear across their Microsoft experiences.
Display names for SKUs and Service Plans are planned to change on October 1st and Microsoft expect most name text string changes in their services to be finished by the end of 2023. Remember, this change is only applying to Azure AD. Microsoft Azure is still Azure. So it will still be possible for organizations to host their Active Directory on an Azure server, which would be different from using Entra ID. With us so far? Good!
Why’s the name changing?
Azure AD has been around for a while now (about a decade), so will be a familiar name to most IT teams. Some thought it wasn’t the best name at the time, due to how similar it sounds to Active Directory (AD), although at this point most people are used to it and understand its meaning.
Despite the familiarity, Microsoft claim the change will give IT teams a simpler experience, as in the past there have been many products to keep track of – often with quite different names that are subject to change. They want to unify all their identity and secure access products under the Microsoft Entra umbrella. This means Entra ID will join other Entra products such as Identity Governance, External Identities, and Workload Identities.
The names of Azure AD features are going to be changing too. For example, Azure AD Conditional Access will now be called Microsoft Entra Conditional Access. In addition, Azure AD MFA will change to Microsoft Entra MFA, and Azure AD single sign-on will become Microsoft Entra single sign-on.
What do IT teams need to do?
In short, nothing. Based on what Microsoft have said, this appears to be a marketing-driven name change, rather than a technical one. IT teams using Azure AD don’t need to do anything and Azure AD will continue to work as it always has. There won’t be any changes or interruptions to existing deployments, configurations, or integrations. Customers also won’t see any changes to pricing or licensing plans either.
The only change IT teams will notice is the display name changing to Entra ID. You’ll see notifications in the administrator portal, on Microsoft websites, and other places you interact with Azure AD.
Will it affect Specops products?
No, any Specops products you have integrated with Azure AD will continue to work as normal. But if you’re still only using Azure AD’s native capabilities without any third party support, it’s worth noting Entra ID is just a new name, and as of yet Microsoft will not be adding any new security features. You could still be leaving yourself vulnerable to password risks.
Many of our customers who were solely relying only on Azure AD Password Protection have told us they were shocked to find how many compromised passwords were in use after running a Specops Password Auditor scan. With Specops, your Active Directory will be scanned against a more comprehensive list of over 4 billion unique compromised passwords. This far exceeds the password list used in Azure AD.
You don’t need to abandon Azure AD to implement stronger password policies or to block users from using leaked passwords. Specops Password Policy helps increase password security in your on-prem Microsoft Active Directory or hybrid Azure AD environment. The solution can target any GPO level, group, user, or computer with password complexity, dictionaries and passphrase settings.
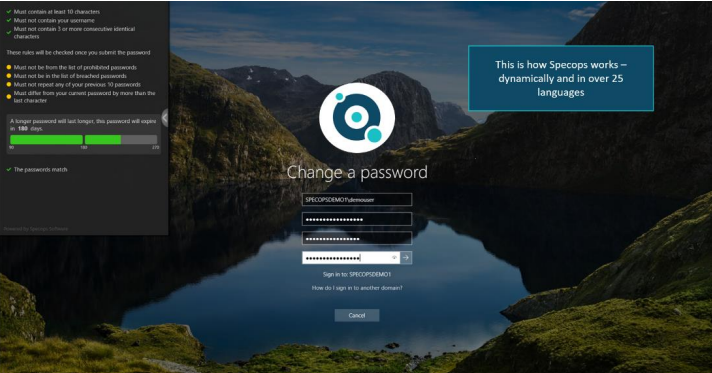
You can also improve the end user experience with custom password rejection messaging. Azure AD only tells users “Unable to update the password. The value provided does not meet the length, complexity, or history requirements of the domain.” Specops Password Policy gives users dynamic feedback at password change as they type, helping to educate them on your organization’s security policies and reduce calls to the helpdesk.
IT teams can set up Specops Password Policy and Breached Password Protection to enforce these policies in an on-prem environment and use a federation solution or Azure AD password write-back to enforce those policies for users across environments. Learn how adding Specops Password Policy to your Azure AD environment can greatly boost your organization’s password security.
(Last updated on February 24, 2025)