This website uses cookies to ensure you get the best experience on our website. Learn more

Hybrid Entra ID (formerly Azure AD) environments and third-party password tools
Table of Contents
Can we leverage third-party password tools like Specops Password Policy in hybrid Entra ID (formerly Azure AD) environments? The answer is yes, and this blog will explain how.
Entra ID Hybrid
Let’s start with some background.
The best way to think about Microsoft Entra ID is that it is primarily intended to be an identity solution. A way to leverage a managed identity for say SaaS solutions via Single Sign on, O365, or providing federation.
This is not the same as standing up Domain Controllers on virtual machines in Azure. Entra ID is a service.
One of the challenges for companies that have an existing on-premises Active Directory Domain Services environment is how to deal with users potentially having two identities that have different passwords and are separate entities? That can become burdensome to users, and create overhead for support.
This is where using Microsoft Entra Connect (formerly Azure AD Connect) comes in. It’s Microsoft’s solution to this issue, and allows a synching of identities from your on-premises domain controllers, and Entra ID. In essence, it allows you to extend your on-premises identities.
AD Connect
AD Connect is the Microsoft solution to dealing with the issue of multiple identities. It allows you to use the same account your users are familiar with, and passwords to be used by Entra ID, for authentication.
AD Connect features:
- Included with your Entra ID subscription at no additional cost.
- When Password Writeback is enabled, password changes via Self Service Password Reset can adhere to on-premises password policies, including Specops Password Policy.
- Can be configured to synchronize changes to your Active Directory identities to Entra ID on a configurable interval.
- Password Changes sync near instantly to Entra ID.
- Can be used to used to sync custom attributes to 3rd party solutions via Entra ID Enterprise Applications and Mapping.
Microsoft Entra Connect and Password Writeback
One of the features of Microsoft Entra Connect and Entra ID is to enable password writeback. This setting dictates whether password changes done in Microsoft Entra SSPR (formerly Azure AD SSPR) are then synchronized back to your on-premises Active Directory environment. Let’s review Microsoft’s sample architecture for Password Writeback.
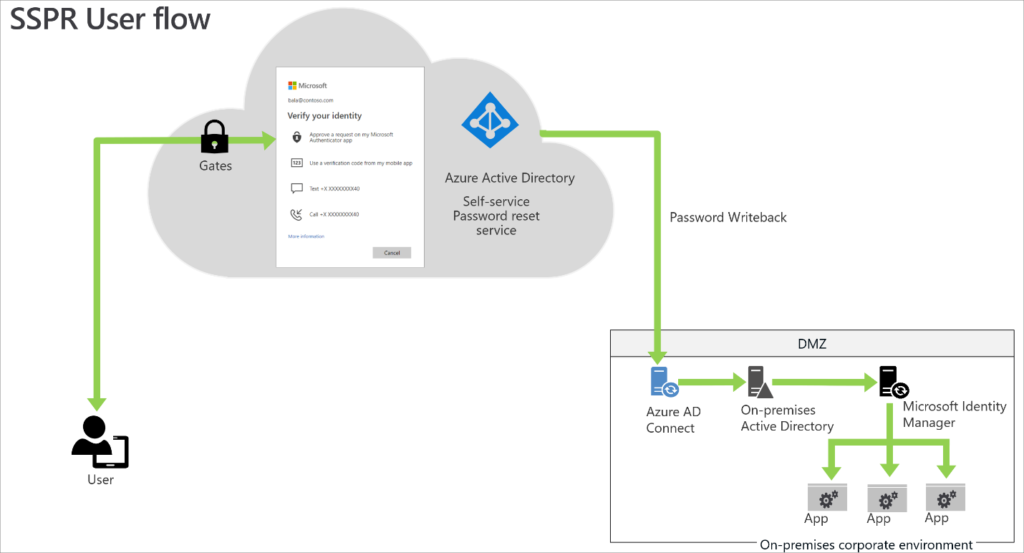
This architecture shows the flow when a user changes their password via SSPR in the cloud. Entra ID will leverage Microsoft Entra Connect (assuming Password Writeback is enabled) to sync the password change back to your on-premises Active Directory environment.
Since AD Connect by default syncs passwords from your on-premises Active Directory environment to Entra ID, you’ve now created a two-way sync for passwords.
Microsoft Entra Connect – Installation considerations
If you want more information about getting Microsoft Entra Connect up and running you can see documentation here.
Some of the items that you may want to consider if you are thinking about implementing Microsoft Entra Connect:
- Review permission requirements for the AD Connect service account, and the required access the person setting up Microsoft Entra Connect will need. You can see details here.
- Look at the requirements and supported configurations – in particular supported topologies here. From experience, it might save you some headaches down the line.
- Treat this server like you would treat a Domain Controller. When in production, it will have important identity information and become pretty critical infrastructure. Consider how you will secure access to this server.
- Considering setting up at least two Microsoft Entra Connect Servers. One in production, and one in Staging mode. They should have identical configurations in case of a critical failure. This way in the case of an issue, or if one server requires maintenance, you can switch the staging into production, and vice versa. You can see more information here.
I have Microsoft Entra Connect installed, how do I enable Password Writeback?
There are two pieces that are required to be configured for this:
- Microsoft Entra Connect Password Writeback feature needs to be enabled.
- Enable Password Writeback for SSPR via Entra ID.
Let’s quickly go over Microsoft’s documentation on how to do this.
Once you’ve done those two items, you have enabled Password Writeback.
How does Specops Password Policy fit in?
Now that Microsoft Entra SSPR (formerly Azure AD SSPR) is configured to use Password Writeback, user password changes done via SSPR do the equivalent of an Admin Reset and SSPR will check your on-premises Active Directory for any password policies including Specops Password Policy, and the password has to meet all of them.
If the user chooses a password that meets your Default Domain Policy, as well as your Specops Password Policy, the password will be changed in Azure, and then sync down to your on-prem Active Directory domain. Please keep in mind that there might be a delay in the password syncing down to your on-prem Active Directory.
| Users | ||||
| On-Prem-only | Hybrid (synced AS->AAD) | AAD-only | ||
| Machines | On-Prem-only | Microsoft Specops Software | Microsoft Specops Software | N/A |
| Hybrid AD Joined | Microsoft Specops Software | Microsoft Specops Software | N/A | |
| AAD-only | N/A | Microsoft Specops Software | Y | |
What does the client-side password feedback support look like for Azure-only machines?
Due to Microsoft’s removal of the traditional password change experience on Azure-only workstations, this is not available with Specops Password Policy, or other vendors in this space. The password change process is replaced with an Entra ID browser-based experience that is similar to the on-prem joined workstation experience, but without any support for layering on custom policy feedback.
Specops uReset can ease the transition to Azure-only workstations, as it brings our dynamic multi-factor engine (including integration with Entra ID) and the Specops Password Policy dynamic feedback experience to the cloud.
What happens when a user chooses a password that is rejected?
The password will not be changed in Azure, nor the on-prem Active Directory Domain.
On the user side, they will receive a message similar to this:

While it does tell them it is rejected, the user still doesn’t quite know what in particular they need to fix for their password change to be accepted. This can cause the user time and they may contact your Service Desk needing assistance.
Whether the password is accepted or rejected, Specops Password Policy is still enforced.
Changing a password in Specops uReset vs Entra ID
As we saw previously, we can change the password in Microsoft Entra SSPR, but the user experience leaves a lot to be desired.
For comparison, I want to walk through the password change experience in Specops uReset to compare.
When a user goes to change their password, they get a screen that shows them all of the requirements the user must meet:
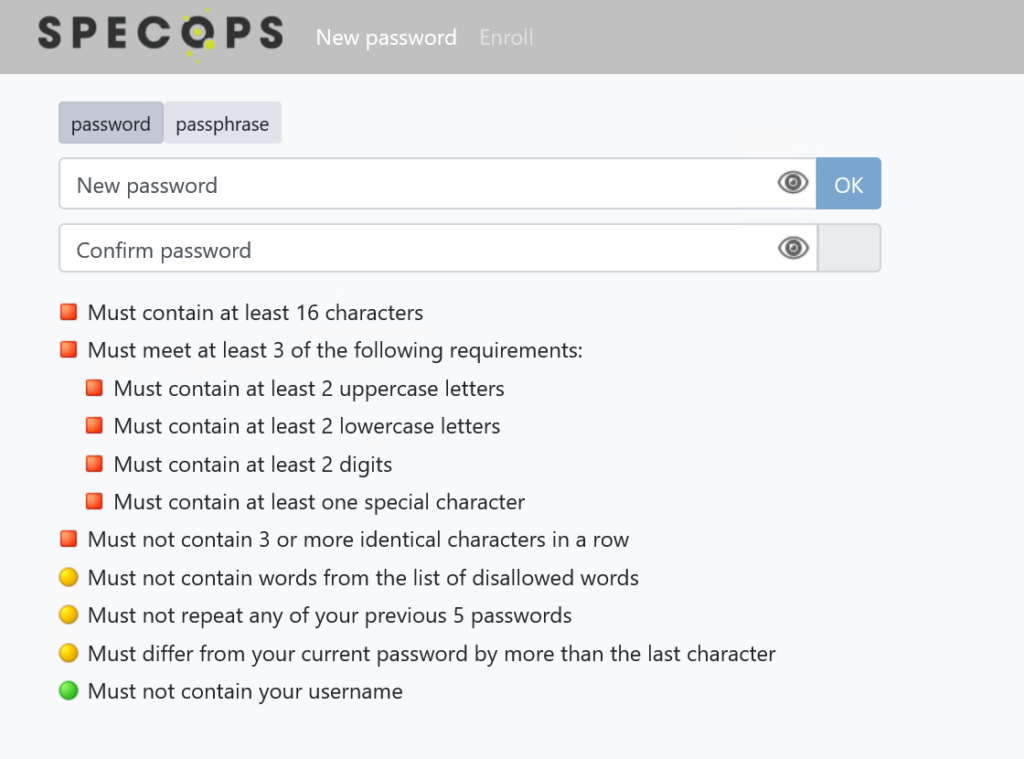
As you can see the user is presented with requirements that they must meet to change their password. This is based on the policy set in Specops Password Policy. The policy requirements can be customized as you need.
As the user starts typing a password, the requirements will turn green as they are fulfilled:
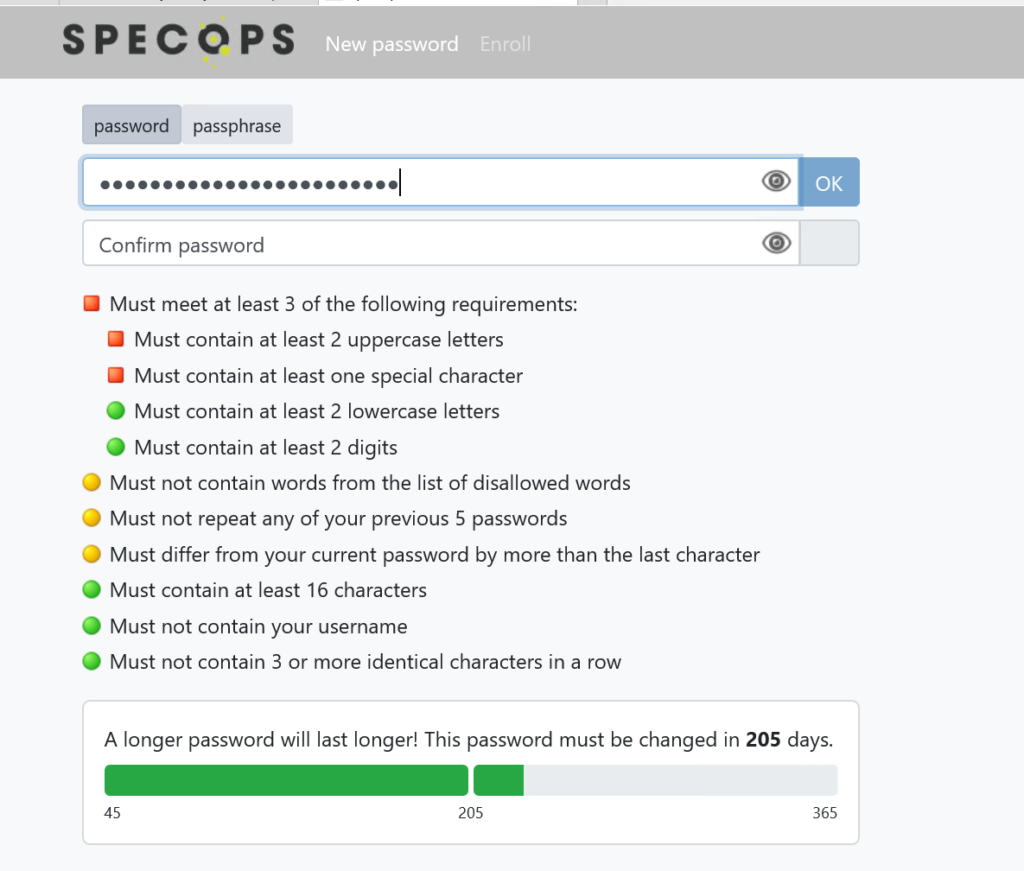
Note: At the bottom we are leveraging the variable length aging custom setting in Specops Password Policy that allows a password maximum age to be set based on the length of the user’s selected password.
Once the user has completed all of the requirements in red, you will see them turn green and the OK button becomes available.
Once the user hits OK and the password change is accepted, they will be given a Success screen:
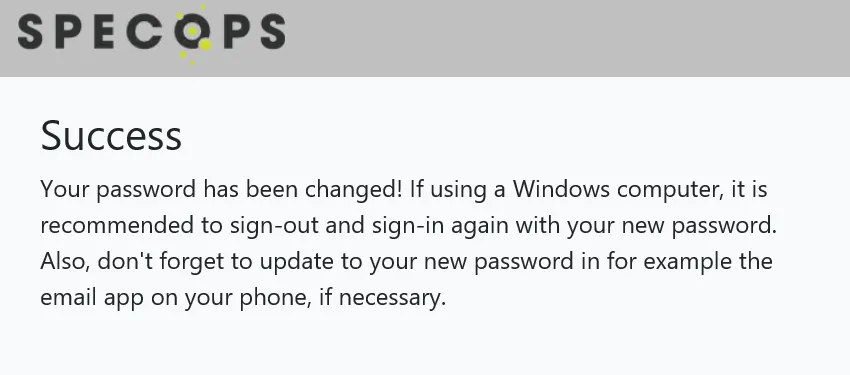
This password will be changed on your on-prem Active Directory, as well as updating the user’s local cached credentials, without the workstation needing direct connectivity to a Domain Controller.
The user has a much more streamlined experience. Users will be able to change their passwords without service desk intervention, password policy compliance will be easier to maintain, and passwords will still be synced back to your on-prem Active Directory domain.
Additional uReset features:
- Multi-Factor Authentication for password changes and resets including 15+ Identity Providers including Okta, PingID, Duo, Symantec VIP, and others including traditional methods like Mobile Code, Google Authenticator, and Email.
- Accessible from any web browser, the Windows logon screen, the mobile app.
- When a user changes their password, their cached credentials is also updated, even if not connected to a Domain Controller.
- Enrollment enforcement and auto-enrollment options.
- Enrollment notifications via system tray, email, or unclosable full screen browser.
- Helpdesk interface for verifying users, unlocking user accounts and setting temporary passwords.
Please Contact us to get more information, or to have a chat about how Specops can help you meet your password security needs.
(Last updated on July 2, 2025)



