This website uses cookies to ensure you get the best experience on our website. Learn more
Password expiration policy best practice
Table of Contents
An effective password policy is a balancing act – security is vital, but ineffective if usability suffers. Users already have too many passwords so NIST tells us to make life a little easier for them. For example, don’t force them to change their password unless there is evidence that it has been compromised.
Forcing users to set a new password not only annoys them, but also drives poor practice. Incrementing a number at the end of the password, character substitutions, and other predictable habits is their coping mechanism. The result is a new password, similar to the old one, with more vulnerabilities as it is more likely to be written down, or forgotten.
Variable password expirations
As an administrator, you are accustomed to the maximum password age policy. The setting determines how long a password can be used before the user is required to change it. Configuring the setting to 90 or 180 days is standard practice in most organizations as it is believed to prevent indefinite access if the password is compromised.
Password age rules – examples and best practice
What if I told you there is a more effective defense against unauthorized account use? Instead of arbitrarily expiring passwords every 90 or so days, you can configure expirations based on the complexity level of a password. With this approach, you can reward security conscious users and stronger password selections with a longer password expiration period.
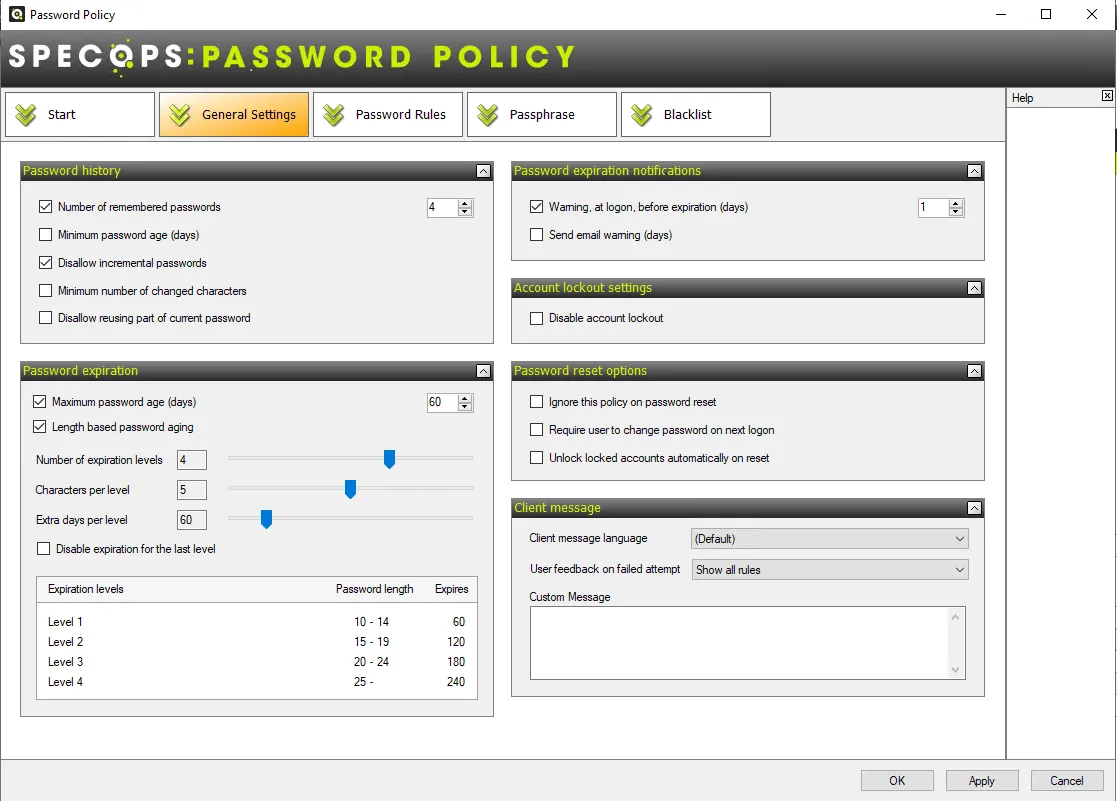
Specops Password Policy supports variable length-based password expirations. The setting allows administrators to extend the maximum password age when a user exceeds the minimum password length.
Using Specops Password Policy, administrators can choose up to 5 password expiration level. For each level they can set a range of characters.
For example, a policy with maximum policy age set to 60 days, and minimum password length set to 10 characters, can be configured with these additional settings:
- Number of expiration levels: 4
- Number of characters per group: 5
- Extra days per group: 60
| Expiration level 1 | Expiration level 2 | Expiration level 3 | Expiration level 4 | |
|---|---|---|---|---|
| Characters per level | Passwords with 10-14 characters | Passwords with 15-19 characters | Passwords with 20-24 characters | Passwords with 25 or more characters |
| Expires | 60 days | 120 days | 180 days | 240 days |
With the above settings, users with longer passwords get additional days on top of their maximum policy age. When they eventually set a new password, you will want to ensure the password is unique. You can mitigate password reuse by enforcing password history – the minimum number of unique passwords that must be associated with a user account before an old password can be reused. With Specops Password Policy, you can also enforce a specify minimum number of characters that must be changed. This will prevent users from using the same password and incrementing a number at the end.
Remember, if you are blocking leaked passwords in Active Directory, password expiration must be frequent enough so they can be checked against the latest password lists. You may want to force users to change their passwords when the banned password list is updated, usually following a major breach incident.
If you want to ditch password expirations altogether, you’ll have to accompany the change with the deployment of a multifactor authentication system. Multi-factor authentication mitigates the risk of a password that never expires.
Contact us for more information about blocking leaked passwords in active directory and variable password expirations for clever password age rules and a safe maximum password age.
These articles might also be interesting:
(Last updated on March 18, 2025)