This website uses cookies to ensure you get the best experience on our website. Learn more
British law firms are under attack from ransomware. How should we upgrade our cyber defences?
Table of Contents
Law firms across the UK have been given a stark warning in a recent report by the National Cyber Security Centre (NCSC): get serious about upgrading your cyber defences or risk your legally privileged information being stolen by ransomware gangs.
Legal business leaders agree. According to PwC’s 2022 Annual Law Firms Survey, 78% of the UK’s top 100 law firms are already ‘extremely or somewhat’ concerned about cyber risk. In addition, 90% of firms said cybersecurity is a major threat to future growth – with the global increase in ransomware attacks cited as a main reason for having a solid crisis management plan in place.
Why are ransomware gangs targeting law firms?
Ransomware attacks are primarily financially motivated. Cybercrime gangs know law is a lucrative business and the price of paying a ransom can be dwarfed by the cost of not being able to work. The reputational risk of highly sensitive data being breached is also used to coerce law firms into paying ransoms. Of course, there’s nothing stopping cybercriminals holding onto sensitive data for further extortion or to sell on the Crime-as-a-Service marketplace, even if a ransom is paid.
The NCSC also warns of state-sponsored hackers, whose motivations may be more political than purely financial. It says China, Russia, Iran, and North Korea all pose threats, with some UK legal institutions already targeted by disruptive ransomware and intellectual property theft. There has also been a rise in ‘hacktivist’ groups which could turn to ransomware due to ideological motivations against a law firm or its clients.
Find out more about the complete Cyber Essential guidelines by NCSC.
Unfortunately, legal workers also make prime targets for email phishing, the most common delivery vector for ransomware. Constant digital communication, distributed remote workforces, and time-pressured employees combine to make it easy for people to miss the warning signs of phishing and accidentally click on a malicious file or link containing ransomware.
How to defend against ransomware
In 2020, a ransomware attack shut down a number of IT systems belonging to the criminal law firm Tuckers Solicitors LLP. The attackers also exfiltrated data relating to 60 court cases (some ongoing) and published details on the dark web. Unfortunately, some cybersecurity failings made Tuckers Solicitors a target. The ICO fined them £98,000 for “negligent security practices” and failing to protect personal data after they deemed the firm had left a vulnerability unpatched for five months. The Commissioner also pointed to the absence of multi-factor authentication (MFA) on certain key systems.
Proactive defences
- Patching: Keep your software (especially operating systems) patched as soon as updates are available. Cybercriminals look for known vulnerabilities – it makes their jobs much easier.
- Shadow IT: Be careful what software and applications employees are allowed to download and use. It may be innocent enough but could be unsupported and have vulnerabilities.
- Malware scans: Scan for malware with antivirus software often to detect and isolate infected machines quickly. Ransomware is most dangerous when allowed to spread.
- Anti-phishing: Phishing is the main mechanism for direct ransomware delivery or stealing passwords for key systems. Law firms should be educating employees on the signs of phishing and supporting them with anti-phishing technology.
Worst case scenario planning
- Backups: Regularly backup your important data and make sure there’s a process for restoring files. This can help limit damage and speed up recovery in the worst case scenario of a ransomware attack.
- Data storage: Ensure you create offline backups that are kept separate from your network and systems. Ransomware attackers will actively targets backups to increase the likelihood of payment.
- Recovery plan: Draw up a plan for recovery and business continuity in the event of a ransomware attack or other incident and rehearse the procedure to ensure it’s well understood.
- Ransom plan: The NCSC’s position, aligned with law enforcement, is to never pay a ransom. There’s no guarantee your data will be returned or you won’t be extorted further. Plus you’re more likely to be targeted in the future once criminal groups know you’ll pay out.
Tighten access security
- Principle of least privilege: IT teams should regularly review access permissions and ensure the ‘principle of least privilege’ is enforced, so if an account was compromised, an attacker won’t have far-reaching access to data.
- Multi-factor authentication (MFA): All employees should be encouraged to use MFA (and it should be mandatory for key systems). This means an attacker needs more than just login credentials.
- Password security: MFA adds an additional layer of security on top of passwords although isn’t foolproof – it can be overcome through attack techniques like prompt bombing. Poor passwords still represent the easiest way for an attacker to gain access to your systems.
Compromised passwords: An overlooked vulnerability
Weak and compromised passwords offer the most simple route for attackers into law firm systems – especially if MFA is not widely used. With the growing use of cloud systems to store confidential data, attackers can exploit weak passwords for initial access, then go on to compromise all manner of legal data through ransomware.
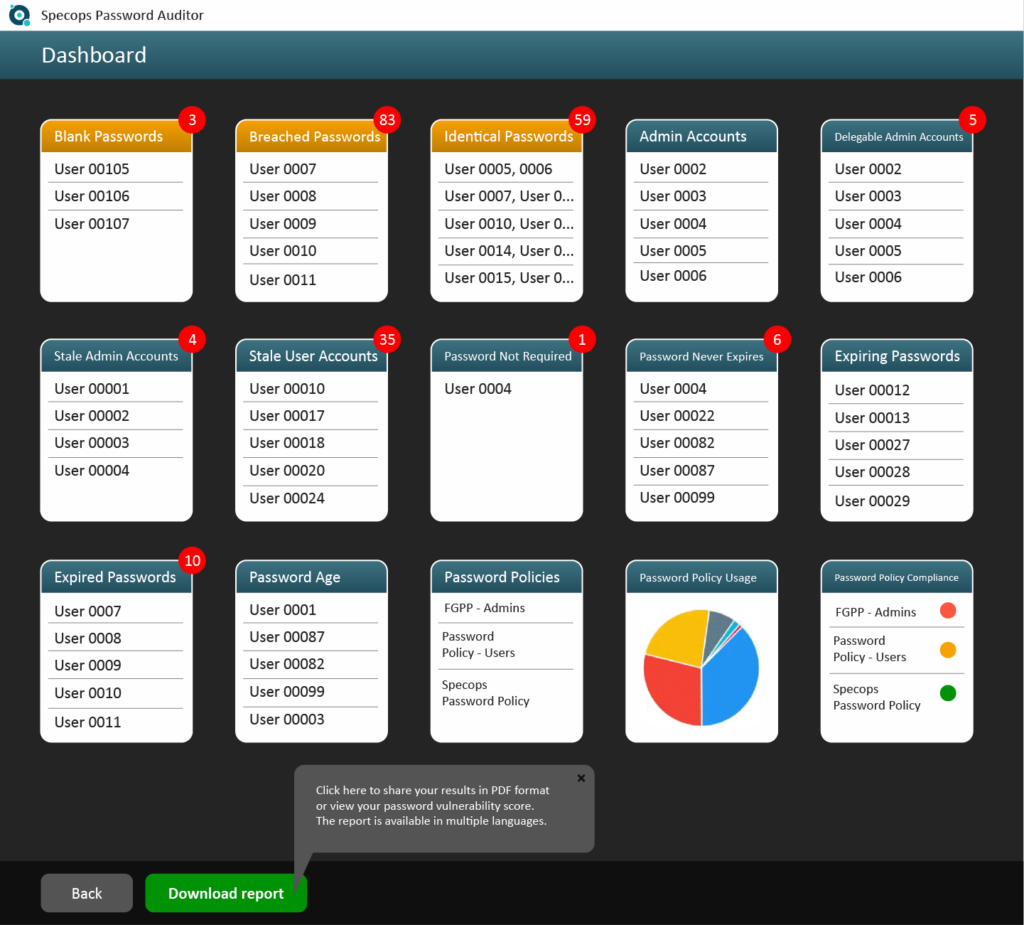
The NCSC recommends combining three random words into a passphrase that’s hard to guess through social engineering, long enough that it’s hard to crack, while also being easy for employees to remember. Tools such as Specops Password Policy help users build strong password policies in line with NCSC guidance, while also checking against a continuously updated list of over 4 billion compromised passwords.
Run a free password audit today
Interested to learn how many passwords in your organization are re-used, weak, or already compromised? Or how many stale user accounts are sitting around with far-reaching access privileges? Close off the easiest routes for attackers to enter your organization: Download for free and scan your Active Directory today.
(Last updated on December 3, 2024)