This website uses cookies to ensure you get the best experience on our website. Learn more
How to find Active Directory passwords set to never expire
Table of Contents
Passwords set to never expire can be a security vulnerability for your network. Here is how to to find Active Directory (AD) passwords set to never expire.
Some regulatory bodies require passwords to expire every 90 days, while others recommend setting passwords to never expire – as long as other protocols are in place. However, if you don’t have those in place or if you didn’t intentionally set passwords to never become invalid, you may want check your Active Directory for any instances of the setting.
Why search for ‘never expire’ Active Directory passwords?
Identifying passwords set to ‘never expire’ in your Active Directory is crucial for maintaining robust security and compliance. These accounts pose a significant risk as they can become a persistent vulnerability if compromised, since the password would never be forced to change. Regularly auditing and managing these accounts helps ensure that all user credentials are periodically updated, reducing the likelihood of unauthorized access and enhancing overall network security.
Passwords set to ‘never expire’ can pose several security risks:
- They increase the window of opportunity for attackers to exploit a compromised account, as there is no forced password change to potentially lock them out
- They can lead to prolonged unauthorized access, which may go undetected for extended periods
- Such accounts can be a weak link in your security infrastructure, making it easier for malicious actors to gain a foothold in your network.
- They can also complicate compliance with security standards and regulations that mandate regular password changes, potentially leading to audit failures and legal repercussions
Challenges with finding ‘never expire’ passwords
Finding passwords set to ‘never expire’ in Active Directory can indeed be challenging, especially in large and complex environments. The sheer number of user accounts and the distributed nature of Active Directory can make manual identification time-consuming and error-prone. Moreover, these settings might be buried within various organizational units (OUs) and group policies, requiring a deep understanding of your directory structure. Automated tools and scripts can help streamline the process, but they need to be carefully configured to ensure they accurately and comprehensively identify all relevant accounts. Regular audits and a well-maintained security policy can mitigate these challenges, but they still require significant effort and expertise.
Find AD passwords set to never expire attribute with PowerShell
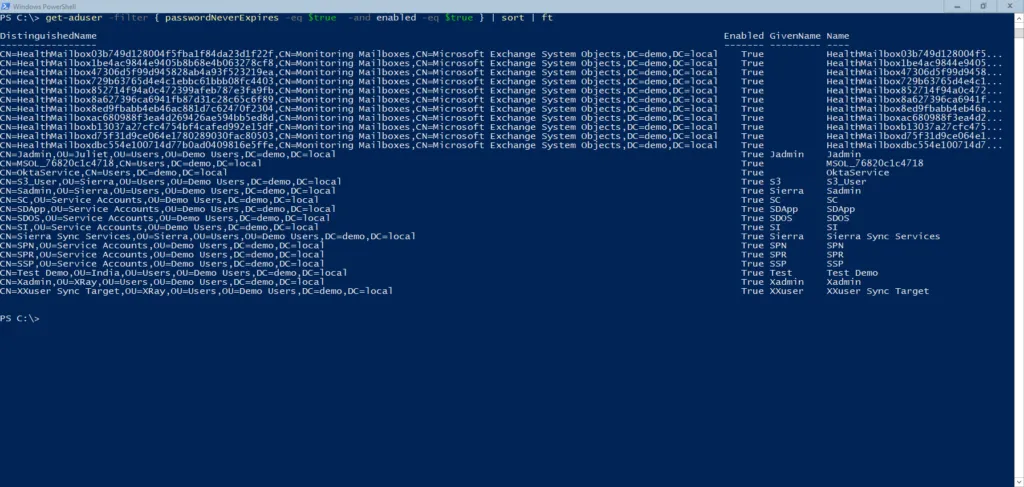
One easier way to do this is with PowerShell. If you’re a PowerShell user and have the Active Directory PowerShell module installed, you can use the below line to find users with the PasswordNeverExpires attribute set to true:
get-aduser -filter { passwordNeverExpires -eq $true -and enabled -eq $true } | sort | ft
Which will return a screen of results like this:
Find AD passwords set to never expire with a simple, free tool
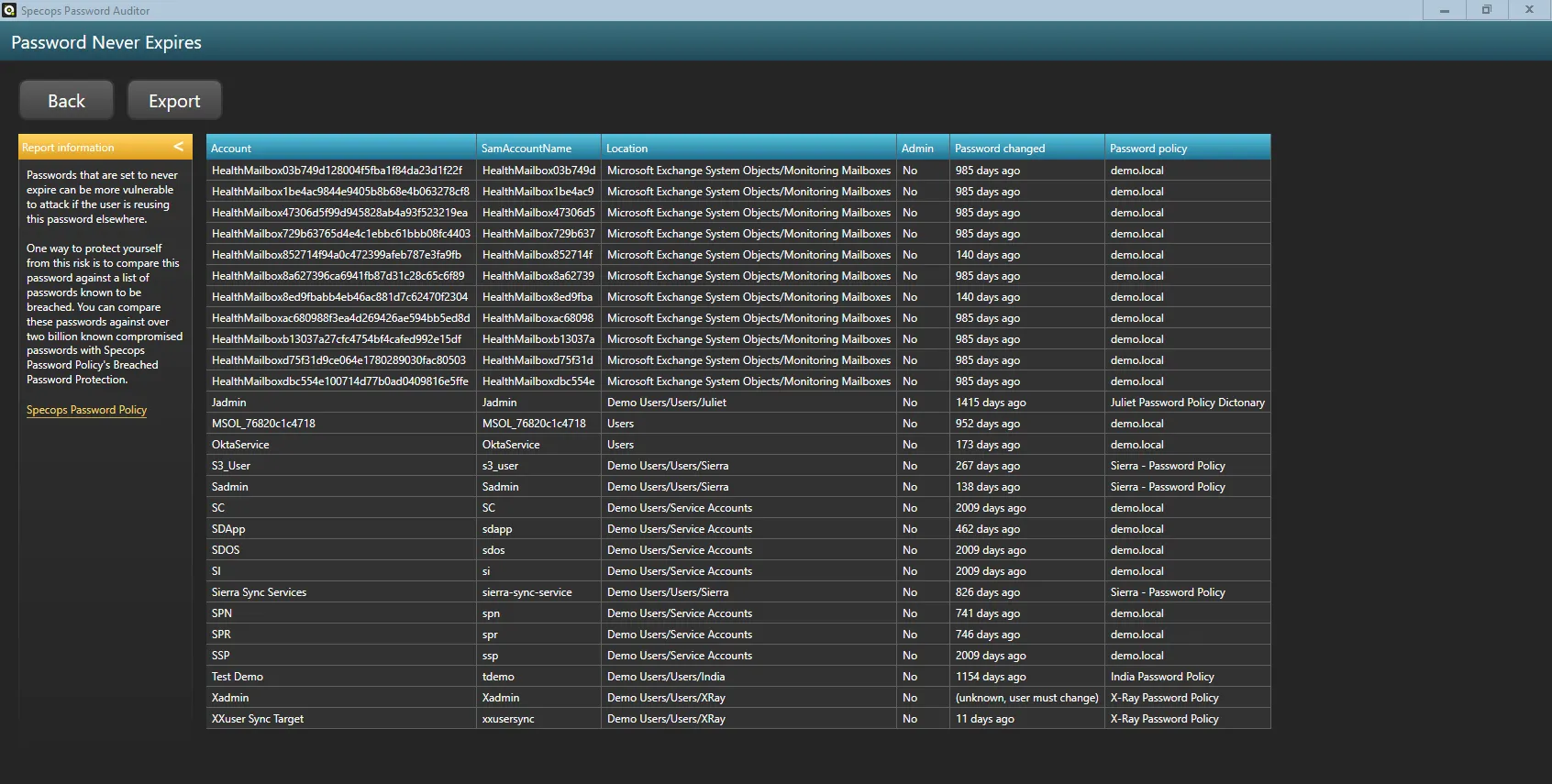
If you’re not a PowerShell user, or simply aren’t in the mood for it, you can also find which of your Active Directory users have passwords that are set to never expire with Specops Password Auditor. Results can be easily exported into a simple-to-understand report.
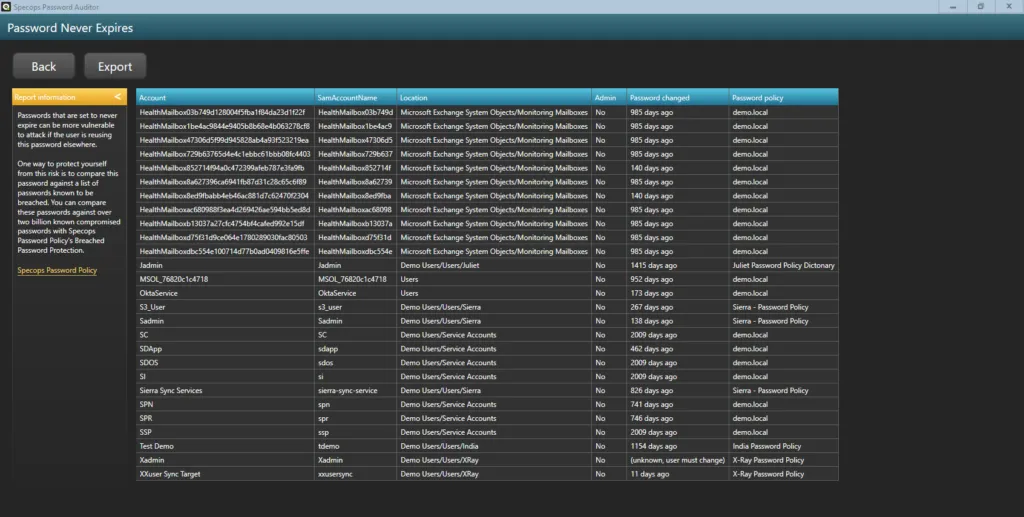
Specops Password Auditor is a free read-only program that scans your Active Directory environment for password-related vulnerabilities. In addition to letting you know whose passwords are set to never expire, you can find out how many of your AD passwords are on a list of known breached passwords, how many are blank or identical, and more. Download for free here.
What to do about passwords that never expire?
Once you’ve found out which Active Directory users have passwords set to never expire, the next action is to decide what to do with them. Make up your mind if want never expire passwords or why it might be better to have an expiration.
Have you set these intentionally? Great. Then your next step would be to ensure that these passwords are not passwords that are known to be breached. Easy enough to do if you’ve run a scan with Password Auditor. If you’ve got known breached passwords active in your environment, you’ll want to look at blocking those – whether you go DIY or with Specops Password Policy which can block over 4 billion known breached passwords. The Breached Password Protection database offers continuously updated protection that can run on a daily scheduled scan of your Active Directory.
Have you not set these intentionally? If that’s the case, you’ll want to update the password settings for these users.
How to update the password settings to never expire for an individual user
Navigate to the user in question within your Active Directory Users and Computers Snap-in.
Once you find the user, right click and select properties.
Uncheck the “Password never expires” box and click OK.
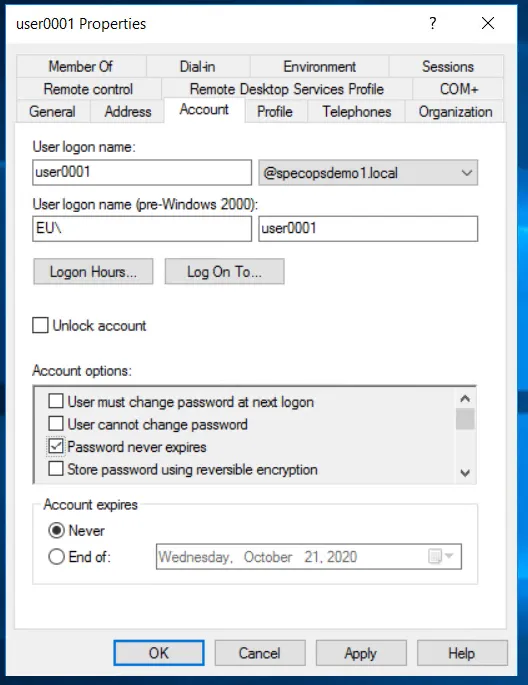
Or update it for that user using the following PowerShell command, substituting the username “user0001” for the username you want to change:
set-aduser user0001 -PasswordNeverExpires $false
It’s also possible to reset the clock on Active Directory password expiration.
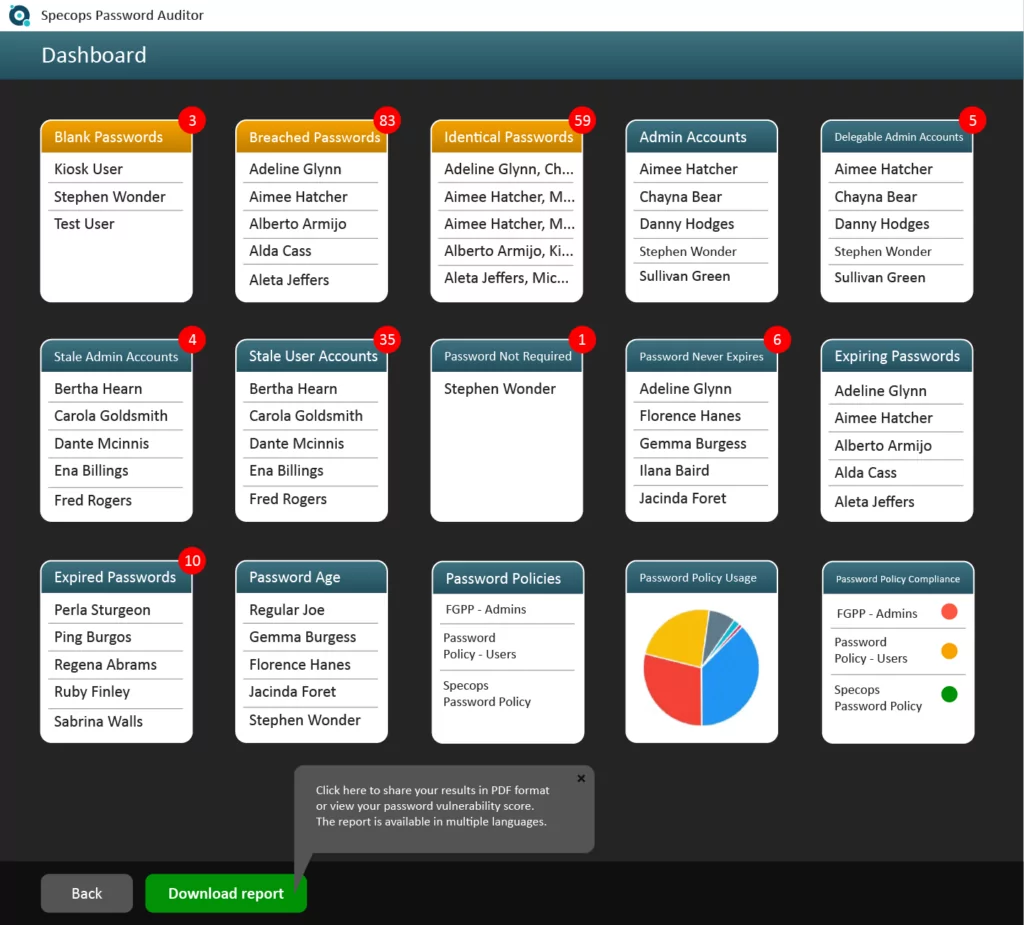
Find more password vulnerabilities with Specops Password Auditor
Passwords set to never expire aren’t the only possible password vulnerability in your environment. With Specops Password Auditor, you can find stale admin accounts, comparisons of your password policies against industry recommendations, breached passwords, and more. Download and find out what your password-related vulnerabilities are today.
Last updated on November 11, 2025


