This website uses cookies to ensure you get the best experience on our website. Learn more

How to change the Active Directory password hash method
Table of Contents
Passwords are generally associated with all aspects of securing technology systems. In most environments, passwords are secured using a password hash. Password hashes can impact how vulnerable an organization’s passwords are to an attacker, or in a data leak that may expose hashed passwords. Let’s dive into an overview of password hashing and see why the Active Directory password hash method is crucial in your environment.
What is a password hash?
Let’s take a step back and discuss the most basic form of recording a password – plain text. We all know the dangers of storing passwords in plain text format. When a password is in plain text format, the password is openly disclosed without any character transformation. You might think about the time when you lifted a keyboard and found that your coworker had recorded their password on a post-it note stuck to the bottom. It is a basic example of a plain text password.
Plain text passwords can be stored digitally, as well. Passwords can be openly viewable inside a notepad document, database, spreadsheet, or another digital file. When a password is in plain text, there is no security to keep someone from seeing and using the password.
When passwords are secured using a password hash, the password undergoes a one-way transformation from the original characters, making up the password into another string value: the hashed password. This transformation is made possible by mathematical algorithms used to calculate the hashed value of the end user’s password input. Again, this is a one-way transformation since it is impossible to “un-hash” or turn the password from the hashed value to the original password.
When an end-user performs a login with a password, their password’s resulting hash is checked with the actual hash value recorded by the system. The same mathematical formula compares the two hashes. If the two are the same, the password entered was the correct one. If they do not match, the user has entered an incorrect password.
When attackers execute a data breach and successfully exfiltrate databases or files containing hashed passwords, the passwords are not in their original format. The attacker still has to figure out the original password used to create the hashed password. As mentioned, the hashing process transforms the data into random data other than the actual password. However, it is essential to stop and think about what password hashing is again. It is a one-way process that transforms your password into a hash value.
While the attacker can’t perform an “un-hash” of the hash, there is nothing to stop an attacker from trying password combinations to get the same password hash. Systems using password hashing get the same result each time with the same input (your password). With this knowledge, an attacker can use educated guesses and other tools to discover the password used to generate the password hash for an account.
Are all password hashes created equal?
There are many different kinds of password hashing algorithms in use today. Some are certainly stronger than others. To help appreciate the difference between hashing algorithms, let’s look at the following three:
- MD5 – This stands for Message Digest and can have 128 bits length of message digest content. It is a high-speed algorithm that provides relatively low security as a password hashing algorithm. An attacker only needs to perform 2^64 operations to find the identical hashes produced with MD5.
- An example of the MD5 hashed password (iloveyou): 8f3e13ff103d826b03821e53ce7ab05a
- SHA-1 – It stands for Secure Hash Algorithm and can have a 160-bit message digest size. SHA-1 is a much slower algorithm than MD5 but provides better security than MD5.
- An example of the SHA-1 hashed password (iloveyou): EE8D8728F435FD550F83852AABAB5234CE1DA528
- bcrypt – The bcrypt password hashing algorithm using salting to calculate the hashed value of a password. Salting adds additional random characters to the first set of characters provided by the user, and then a hash is created. Bcrypt helps to protect passwords from so-called rainbow table attacks.
- An example of the bcrypt hashed password (iloveyou): $2y$12$nRhqyj7F4XMKotj4GQ5nheExNUnT/Xnne7ithBy3EzM83zbYNM13m
Considering the examples of the password hashing algorithms mentioned above, compared to MD5 and SHA-1, bcrypt is exponentially more secure as a password hashing algorithm. It is extremely slow to create a hash using bcrypt due to the extra salting creating the hash when compared to MD5 and SHA-1. However, an attacker attempting to generate hashes using bcrypt to duplicate hashes to leaked copies of bcrypt hashed passwords will have a much more difficult time.
As noted by security expert Troy Hunt, attackers can generate tens of billions of password hashes a second for either MD5 or SHA-1 password hashes. While bcrypt is undoubtedly much more secure than either MD5 or SHA-1, given how password hashes work, an exact password hash still is not impossible to determine using any of the current password hashing algorithms used today, including bcrypt.
No matter how secure a password hashing algorithm may be, the strength of the password itself becomes crucially important. As we have learned with the overview of password hashing, the hashed equivalent of the password is the same each time. It means that using a known or commonly used weak password is dangerous no matter the hashing algorithm used.
Attackers who get their hands-on large databases of previously compromised accounts and passwords have a treasure trove of known passwords they can use in password stuffing attacks against various online systems. Additionally, they can use known passwords to crack accounts in password spraying attacks.
The Active Directory password hash method
There is another issue that must be considered important with Active Directory hashing in particular. In Windows, when a user selects a password that is less than 15 characters, Windows generates two different kinds of hashes. These hashes are:
- LAN Manager Hash (LM hash) – LM hash is restricted to 14 characters or less, characters are converted to uppercase, and any characters under 14 are null-padded to equal 14 characters. The fixed-length is split into two 7-byte halves.
- Windows NT hash (NT hash) – The stronger modern way that passwords are stored in Windows.
Both of these hashes are stored in the local Security Accounts Manager (SAM) database or in Active Directory. The LM hash is notoriously weak and is explicitly used for backward compatibility with legacy Windows operating systems such as Windows 95 and Windows 98. However, Macintosh clients also rely on the LM hash and may experience problems authenticating to an Active Directory domain without it.
- In Group Policy, expand Computer Configuration > Windows Settings > Security Settings > Local Policies, and then click Security Options.
- In the list of available policies, double-click Network security: Do not store LAN Manager hash value on next password change.
- Click Enabled > OK.
Microsoft officially turned off LAN Manager with Windows Server 2008. However, it is still a point that is worth noting in environments still using legacy Windows versions due to compatibility with legacy applications and other reasons. You can read more about LM hash and how to disable it with the official Microsoft article.
The easiest way to prevent storing an LM hash of your password is to enforce the use of passwords that are at least 15 characters long. When 15 characters and longer passwords are chosen, Windows stores an LM hash value that can’t be used to authenticate an end-user.
Finding weak or breached passwords is critically important
No matter which password hashing algorithm your organization uses for business-critical systems, finding weak or breached passwords is critically essential for securing your environment. Microsoft Active Directory, used by most enterprise organizations worldwide for identity services, does not have built-in capabilities to check for commonly used, reused, or breached passwords.
Having the right tools to gain visibility to these types of passwords in your environment helps to remediate issues with the insecure or out-right breached passwords used before an attacker does. Specops Password Auditor is a free tool that provides visibility to dangerous passwords configured in your Active Directory environment.
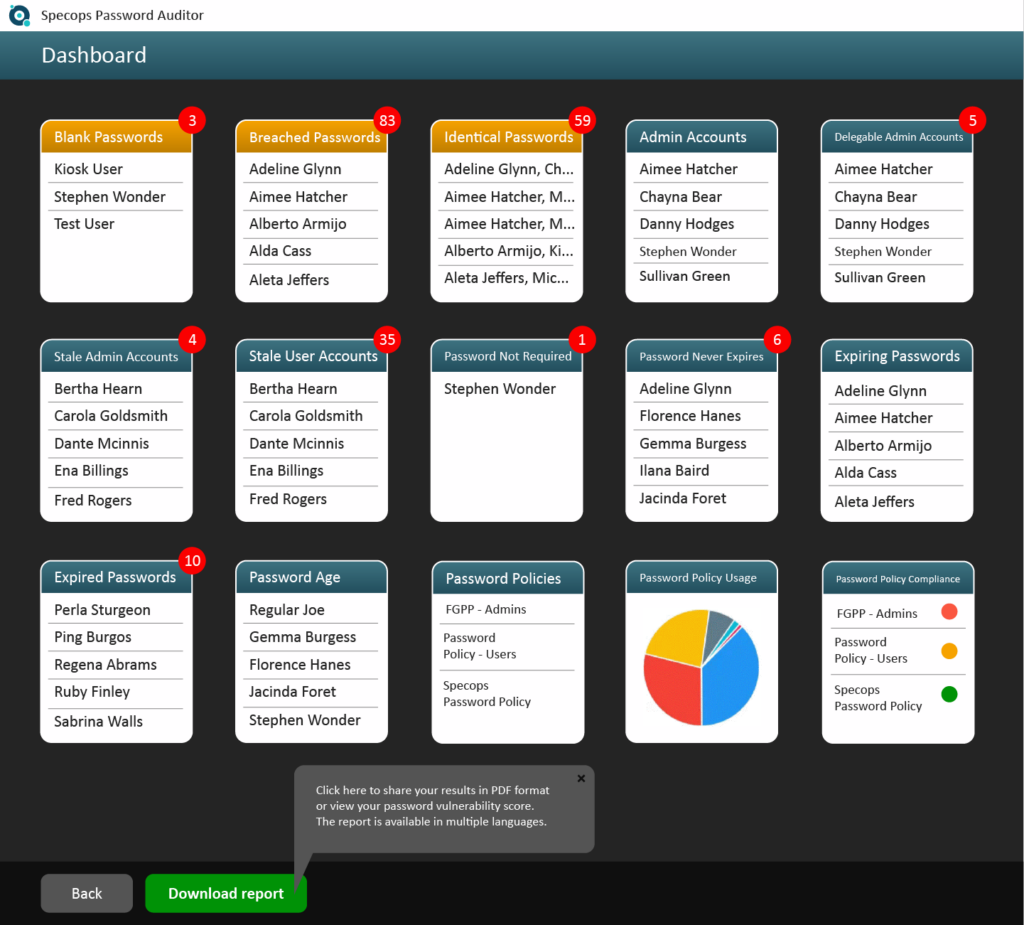
Considering that no password hash algorithm can protect you against weak and easily guessed passwords, finding and remediating these in your environment is crucial.
Concluding thoughts
Password hashing is a commonly used technique to protect passwords. Not all password hash technologies are equal. Compared to the relatively insecure MD5 and SHA-1, the bcrypt hash provides far superior protection to the original password than MD5 and SHA-1. Additionally, it takes much longer to reproduce or guess the hashes generated with bcrypt. Regardless of the type of password hash technology used, weak or commonly used passwords provide easy targets for attackers who use large password lists in password spraying and credential stuffing attacks.
Organizations need to use the right tools to discover weak and risky passwords in their Active Directory environments. Specops Password Auditor provides a powerful tool to help gain visibility to many different types of dangerous passwords used in Active Directory as well as effective auditing of existing password policies against security best practices.
Find out more about Specops Password Auditor and download the tool for free.
(Last updated on June 27, 2025)



