This website uses cookies to ensure you get the best experience on our website. Learn more
[New research] How tough is bcrypt to crack? And can it keep passwords safe?
Table of Contents
Earlier this year, the Specops research team published data on how long it takes attackers to brute force MD5 hashed user passwords with the help of newer hardware. Now we’ll be putting the bcrypt hashing algorithm to the test, to see how long its hashed passwords take to crack with the same computational power. This research coincides with the latest addition of over 49 million compromised passwords to the Specops Breached Password Protection service.
We’ll run through what makes bcrypt a popular way to secure passwords and some of the advantages it has over other common methods such as SHA256 and MD5. But does a stronger algorithm keep your passwords safe from hackers? We’ll also explore the Achille’s heel of bcrypt (and all hashing algorithms).
Different types of hashing algorithm
Storing passwords in plaintext should never be an option, as anyone with unauthorized access to the database could simply read them. Most systems today therefore make use of hashing algorithms to protect passwords in storage against the risk posed by an attacker getting their hands on the system’s password database. Because of the one-way nature of hashing algorithms, the only way to reveal the actual password from a hash is to guess via brute force techniques.
Guessing would be an impossible task for a human alone, so attackers user hardware and password cracking software like Hashcat, L0phtcrack, or John The Ripper. During brute force attacks, they’ll try millions or billions or combinations (as many as their computer power can handle) comparing a huge number of strings to a hash. Dictionary lists and other tools make this task a bit easier for an attacker in a hybrid attack, but the time needed to crack a hashed password can get astronomical quickly.
Different hashing algorithms take different amounts of time for password cracking software and hardware to crack. Older ones like SHA-1 and MD5 are not considered as secure because of how quickly modern cracking software can break through them; however, MD5 is still among the most frequently cited hash algorithm in found leaks. If you want to see how MD5 stacks up against brute force cracking techniques – check out the out last piece of research here.
What’s bcrypt and how does it work?
bcrypt was created in 1999, using the Blowfish cipher algorithm as its base. It transforms a user’s password into a fixed-length string of characters in a one-way hash function, meaning it cannot be changed back to the original password. Whenever the user logs in, bcrypt re-hashes the password and compares that value to the one stored in the system’s memory to see if the passwords match. If a plain-text password is short, this process can stretch it to become longer and more complex.
To increase security, bcrypt also adds a random piece of data to each password hash, ensuring its uniqueness and making it very hard to guess with dictionary or brute force attacks. This is known as salting and the result is a 22-character string placed in front of the password hash, making it even harder to guess via brute force. Salting raises security and makes passwords more resistant to brute force and dictionary attacks.
bcrypt also uses a ‘cost factor’ which makes it different to other hashing algorithms. It shows how many password iterations were made before the hash was generated and is added in front of the salt. With it, you can determine the number of password iterations and hashing rounds to be performed, increasing the amount of time, effort, and computational resources needed to calculate the final hash value. This slows cracking down immensely.
The password string, salt, and the cost factor are combined by the algorithm to make a 24-byte hash using base 64 encoding. Let’s see what it takes to crack it.
Time taken to crack bcrypt hashed passwords
A bcrypt hash takes time to make – it also takes time to break. A threat actor might give up, lack the computational power, or it might give security teams the time need to notice suspicious activity. Even with higher computer speeds, bcrypt is very time-consuming to hack via brute force thanks to its variable number of password iterations.
Compare this to popular hashing algorithms such as MD5 and SHA256, which are designed to hash quickly. They’re better for applications that are used frequently and where speed is important, whereas bcrypt is the better option for the safe storage of passwords. If the iteration count is such that one bcrypt invocation is as expensive as millions of computations of MD5, then brute-forcing the password will be millions of times more expensive with bcrypt than with MD5.
As you can see in the below table, the cost factor of bcrypt makes it extremely secure against brute force attacks thanks to its slow-working hashing algorithm. Short, non-complex passwords can still be cracked relatively quickly, highlighting the huge risks of allowing users to create weak (yet very common) passwords such as ‘password’, ‘123456’, and ‘admin’. But once a combination of characters are used in passwords over eight characters in length, the time to crack quickly becomes a near-impossible task for hackers.
TIME TO CRACK: bcrypt Hashed Passwords
| Number of characters | Numbers Only | Lowercase Only | Upper and LowerCase | Number, Upper, Lower | Number, Upper Lower, Symbols |
|---|---|---|---|---|---|
| 6 | Instantly | 7 minutes | 7.5 hours | 22 hours | 11.5 days |
| 7 | Instantly | 3 hours | 16.2 days | 8 weeks | 3 years |
| 8 | 3 minutes | 4 days | 2.4 days | 9.5 years | 286 years |
| 9 | 23 minutes | 2.8 months | 120 years | 583 years | 27154 years |
| 10 | 3.8 hours | 6 years | 6228 years | 36160 years | 2579596 years |
| 11 | 38 days | 161 years | 323856 years | 2241941 years | 245061585 years |
| 12 | 15 days | 4169 years | 16840527 years | 139000337 years | 23280850.6 thousand years |
| 13 | 5.2 months | 15483 years: | 875707453 years | 8618021 thousand years | 2211681 million years |
| 14 | 4.3 years | 2779344 years | 45536787 thousand years | 534317295 thousand years | 210109676 million years |
| 15 | 44 years | 72262968 years | 2367912 million years | 33127672 million years | 19960419.3 billion years |
| 16 | 431 years | 1878837183 years | 123131474 million years | 2053916 billion years | 1896240 trillion years |
| 17 | 4309 years | 48849767 thousand years | 6402837 billion years | 127342773 billion years | 180142784 trillion years |
| 18 | 43084 years | 1270094 million years | 332947505 billion years | 7895252 trillion years | 17113565 quintillion years |
| 19 | 430840 years | 33022443 million years | 17313271 trillion years | 489505617 trillion years | 1625789 quadrillion years |
| 20 | 4308396 years | 858583501 million years | 900291 quintillion years | 30349349 quintillion years | 154449919 quadrillion years |
The above table shows time to crack via brute-forcing given hashes with modern hardware with the following assumptions. This was the exact same set-up we used for the MD5 cracking research – it’s achievable for most bad actors looking to crack an organization’s passwords, although for optimal results you’d ideally want more power than we’re using here:
- Hardware: the Nvidia RTX 4090. Currently the best value-for-money generally available hardware to perform password cracking attacks with. This is a flagship gaming GPU which can be purchased by consumers, and is largely affordable with an MSRP of around $1599 USD. In order to generate this data, we’re using a hypothetical Nvidia RTX 4090.
- Software: Hashcat. Generally, a stock RTX 4090 will achieve approximately 164 GH/s in Hashcat (that can be thought of as 164 000 000 000 password guesses/second).
The above hardware assumptions may sound expensive; however, with ransomware payments in the millions, the cost can seem minimal. Even still, some attackers may find faster and cheaper results with cloud services.
Can bcrypt hashing prevent password compromise?
In short, no. While it offers a way to protect stored passwords from being guessed, HaveIBeenPwned has many examples where bcrypt hashes been exposed via data breaches. For example, in February 2018, the diet and exercise service MyFitnessPal suffered a data breach. The incident exposed 144 million unique email addresses alongside usernames, IP addresses and passwords stored as SHA-1 and bcrypt hashes (the former for earlier accounts, the latter for newer accounts).
“An attacker will typically try to avoid brute-forcing a hashing algorithm like bcrypt, for the reasons we’ve seen in this research. They much prefer low-hanging fruit, such as Active Directory passwords that have already been compromised through data breaches. One of the biggest threats to organizations is password reuse,” said Darren James, Senior Product Manager at Specops. “Your users’ work passwords could be stored in the most secure way but the minute they reuse that password on some less secure website and that website gets breached; that attacker could be coming for your network.”
As the below table illustrates, a strong password hashing algorithm is meaningless once a password has been compromised. Blocking the use of known compromised passwords is an essential part of defending against password guessing attacks.
“When we speak to IT teams, they usually understand the risks of password reuse,” continued James, “but it’s not always easy to get decision makers to see what’s essentially a hidden danger. Hopefully these password cracking tables can help IT teams get buy-in for dealing with compromised passwords. They’re a risk that really shouldn’t be overlooked in any password security program.”
TIME TO CRACK: Known Compromised Passwords
| Number of characters | Numbers Only | Lowercase Only | Upper and Lower Case | Number,Upper, Lower | Number,Upper, Lower,Symbols |
|---|---|---|---|---|---|
| 6 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 7 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 8 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 9 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 10 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 11 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 12 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 13 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 14 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 15 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 16 | Instantly | Instantly | Instantly | instantly | Instantly |
| 17 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 18 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 19 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 20 | Instantly | Instantly | Instantly | Instantly | Instantly |
Find compromised passwords in your network today
This month’s update to the Breached Password Protection service includes this month’s addition of over 21 million compromised passwords to the list used by Specops Password Auditor. You can find how many of your passwords are either compromised or identical with a read-only scan of your Active Directory from Specops Password Auditor. You’ll get a free customizable report on password-related vulnerabilities, including weak policies, breached passwords, and stale/inactive accounts. Download your free auditing tool here.
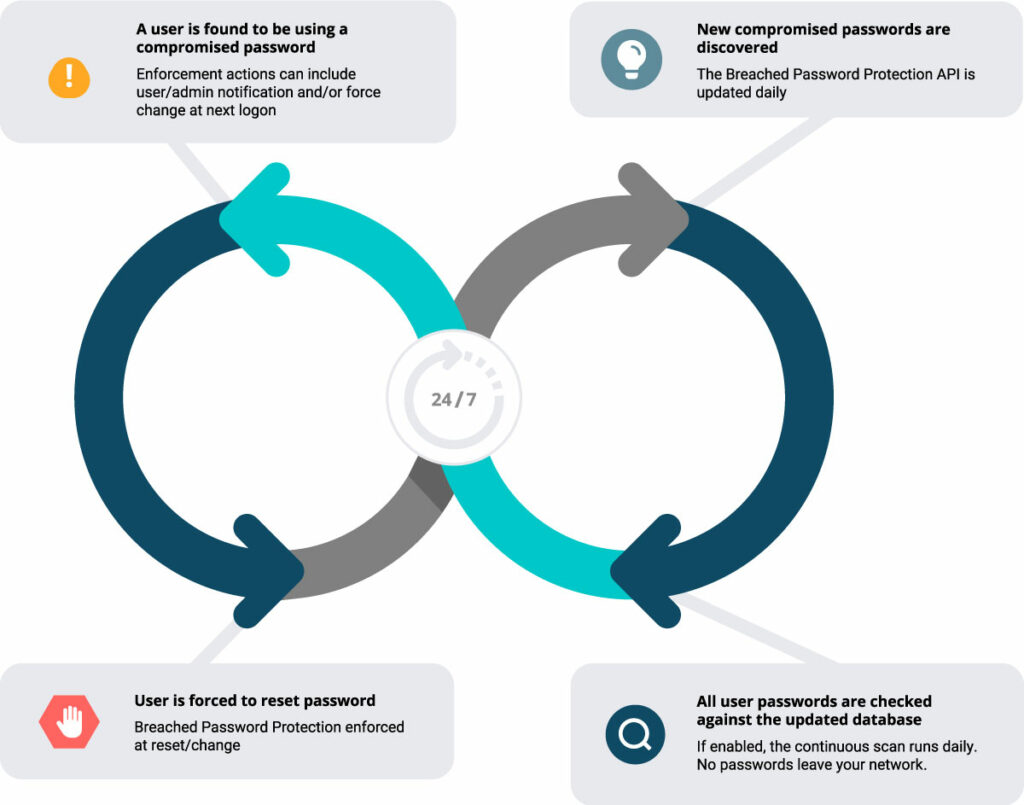
Continuous automated defense against compromised passwords
Specops Password Auditor offers a great starting point for assessing your current password risks, but it’s only a snapshot. With Specops Password Policy and Breached Password Protection, organizations can continuously protect themselves against over 3 billion more known unique compromised passwords. These compromised passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC.
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk.
The daily update of the Breached Password Protection API, paired with continuous scans for the use of those passwords in your network, equals a much more comprehensive defense against the threat of password attack and the risk of password reuse. Interested in seeing how this might work for your organization? Have questions on how you could adapt this for your needs? Contact us or see how it works with a demo or free trial.
(Last updated on April 10, 2025)