Specops Is Not Accurately Displaying my Domain Password Policy or Fine-Grained Password Policy
In Specops Password policy administrative tools or in Specops uReset/Password Reset you may find that the displayed password policy rules from Active Directory do not appear accurate.
All Specops password products respect both the default and fine-grained password policies as configured in Active Directory and are displayed by reading the relevant configuration attributes directly from Active Directory. If the rules shown by a Specops product do not appear accurate, it is likely due to a misconfiguration in Active Directory causing a misleading view of what the password policy actually is.
Table of contents
Checking the Default Domain Password Policy
Use the following Active Directory PowerShell cmdlet to view the AD password policy:
get-addefaultdomainpasswordpolicyFor example:
PS C:\> Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled : True
DistinguishedName : DC=specopsdemo1,DC=com
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 3
MaxPasswordAge : 365.00:00:00
MinPasswordAge : 00:00:00
MinPasswordLength : 7
objectClass : {domainDNS}
objectGuid : 8630708b-d579-4ef9-9daf-54e96fdd8a32
PasswordHistoryCount : 4
ReversibleEncryptionEnabled : FalseThis cmdlet directly reads attributes on the root domain object in AD; these same attributes are used by AD when enforcing password rules. (Note: MinPasswordAge and MaxPasswordAge are in days.HH:MM:SS format. If either is set to all 0’s then that rule is not enforced).
The settings in the Default Domain Policy GPO or other GPOs can be used to modify these attributes, but those are not checked by AD during password changes; only the actual attribute values here matter. Specops password management products read these same attributes when displaying the built-in password policy rules to users or administrators. If one or more rules here does not line up with your Default Domain Policy GPO configuration, it is likely that one of the following has occurred:
- The PDC emulator is not processing policy correctly or a recent policy change has been made but gpupdate has not yet run on the PDC emulator — run gpupdate on your PDC emulator manually to rule this out
- ‘The Default Domain Policy is not linked at the root of the domain
- Inheritance is blocked on the Domain Controllers OU
- Another GPO at the root of the domain also has password policy settings configured and has higher link order than the Default Domain Poilicy
- The password policy setting(s) in Group Policy are set to ‘not defined’ leaving any existing password policy settings tattooed on the attributes in AD
Fine-Grained Password Policies and Specops Password Policy
Specops Password Policy admin tools do not display fine-grained password policies or consider them when evaluating if the Specops policy is compatible with the built-in AD policy. This is expected, as comparing the scope of GPO-based Specops policies and group-based fine grained password policies can get complicated quickly. Compatibility between a Specops policy and a fine-grained policy must be checked manually; it is recommended to move any policy variance in your fine-grained policies to Specops policies for greatly improved ease of administration.
Fine Grained Password Policies and Specops uReset / Password Reset
Specops uReset and Password Reset will display the rules configured in a fine-grained password policy when users are changing their passwords. If the fine-grained policy rules are not displayed in these products, it is likely that the relevant service account does not have access to read the fine-grained password policies as they are heavily locked down by default.
Identify the service account — for Password Reset this is the account the Specops Password Reset Server service is running as. For uReset 8 it is the Specops Authentication Gatekeepers group. Then grant it read access to your fine-grained policies:
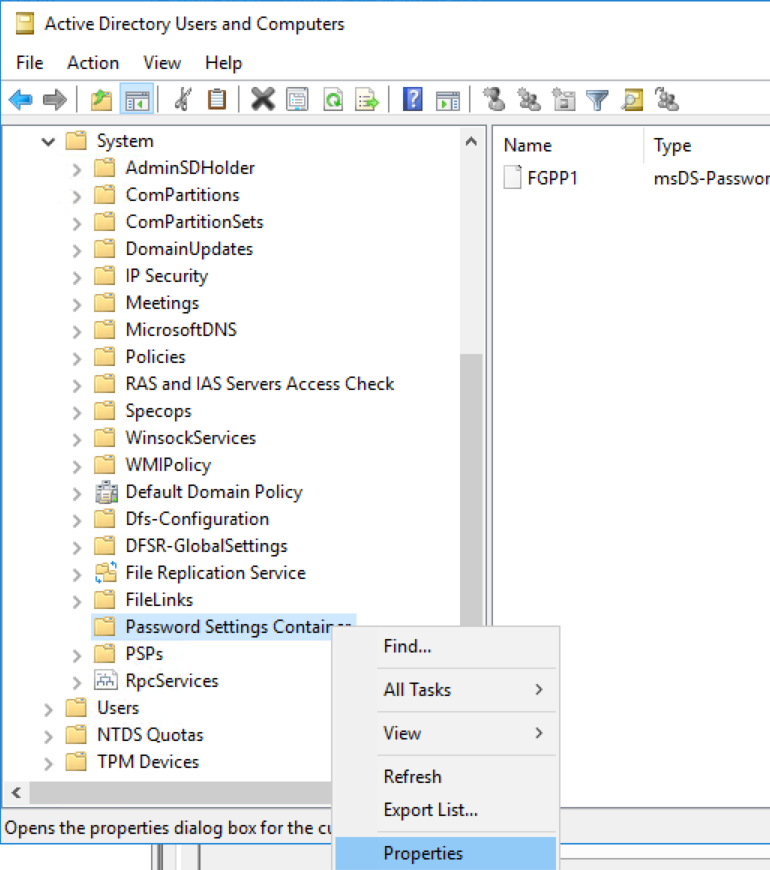
In Active Directory users and Computers with View -> Advanced Features enabled, right-click on the Password Settings Container under the System container in AD and select Properties:
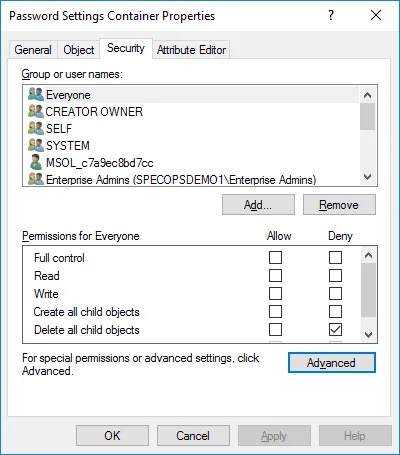
Go to the Security tab and click the Advanced button:
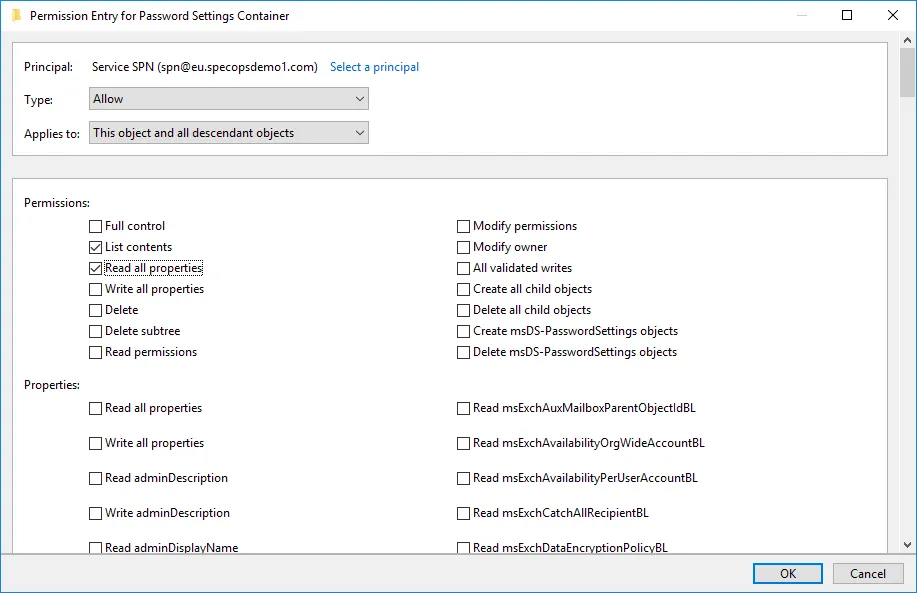
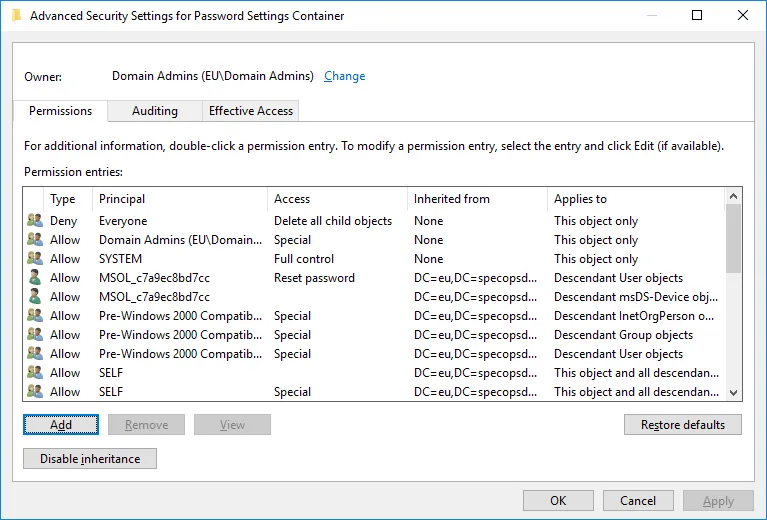
Click the Add button:
Set the principal to your service account or Gatekeepers group. Verify the type dropdown is set to Allow and the Applies to dropdown is set to ‘this object and all descendant objects.’ Scroll all the way to the bottom to find and click the button to clear all permissions, then scroll back to the top and check ‘list contents’ and ‘read all properties.’ Click OK on this dialog and all parent dialogs until back in AD Users and Computers.