Wrapping Third Party Credential Providers
The Specops client operates as a Windows credential provider in order to enhance the user experience when using Specops products from AD-joined Windows workstations. For Specops Password Policy this means improving the user feedback during a CTRL+ALT+DEL password change. For Specops uReset and Password Reset customers, our client provides a link for the user to reset their password from the logon screen before logging into Windows. These features are offered through a process called ‘wrapping’ where we modify or enhance the experience in the default Windows logon screen.
The Specops client also supports wrapping of other third-party credential providers that may also installed on workstations, as long as that other credential provider supports being wrapped. Common examples of other credential providers include full-disk encryption solutions with pre-boot authentication, multi-factor authentication solutions for Windows logon, and VPN solutions that support connections from the Windows logon screen.
This article offers an overview of how to identify third-party credential providers installed on Windows and configure the Specops client to work along side them.
Table of contents
Identifying the Last Logged On Credential Provider
Begin by checking the last logged on credential provider via the Windows registry. This will tell us which credential provider was active when you last logged into Windows.
Key Name: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI
Value Name: LastLoggedOnProvider
Value Data: {GUID of credential provider used to log into Windows}
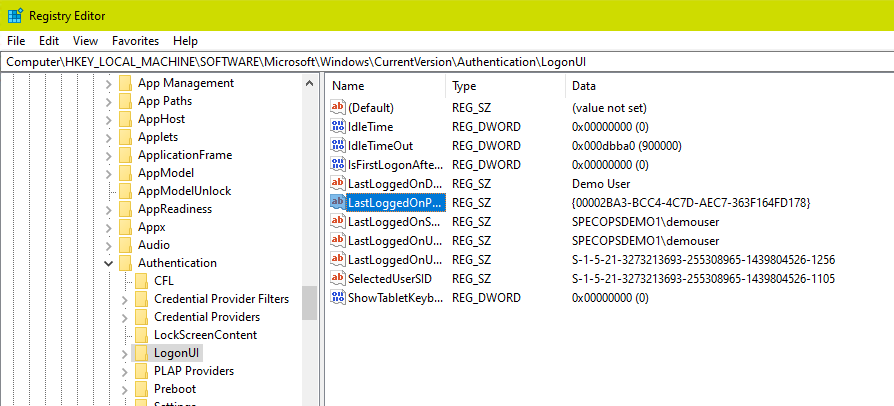
Check the list of all credential providers installed. Each installed credential provider will have a key under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers with the key name as the provider GUID and the default value as the name of the credential provider.
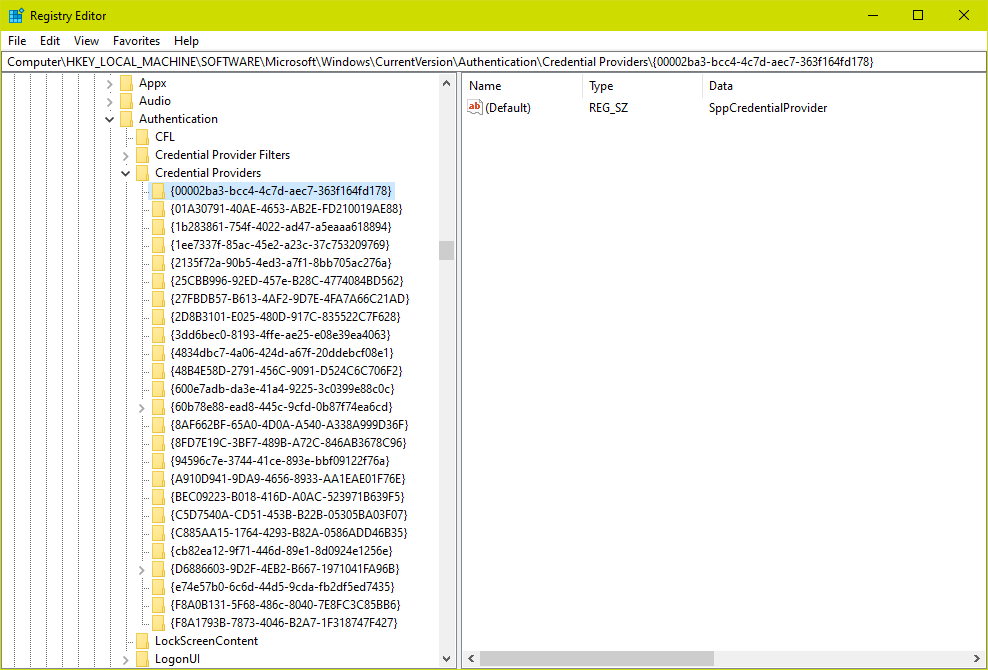
Both sample screenshots here were taken from a Windows 10 machine with the Specops Client and no other third-party credential providers installed. In this example the lastLoggedOnProvider value is actually the GUID corresponding to the Specops Client.
The Specops client contains two credential providers:
| Provider Name | GUID |
|---|---|
| SppCredentialProvider | {00002ba3-bcc4-4c7d-aec7-363f164fd178} |
| SppTiledCredentialProvider | {4834dbc7-4a06-424d-a67f-20ddebcf08e1} |
You also may see one of the GUIDs built into Windows used as LastLoggedOnProvider. Here is a list of the providers that ship with Windows 10:
| Provider Name | GUID |
|---|---|
| Automatic Redeployment Credential Provider | {01A30791-40AE-4653-AB2E-FD210019AE88} |
| Smartcard Reader Selection Provider | {1b283861-754f-4022-ad47-a5eaaa618894} |
| Smartcard WinRT Provider | {1ee7337f-85ac-45e2-a23c-37c753209769} |
| PicturePasswordLogonProvider | {2135f72a-90b5-4ed3-a7f1-8bb705ac276a} |
| GenericProvider | {25CBB996-92ED-457e-B28C-4774084BD562} |
| TrustedSignal Credential Provider | {27FBDB57-B613-4AF2-9D7E-4FA7A66C21AD} |
| FIDO Credential Provider | {2D8B3101-E025-480D-917C-835522C7F628} |
| NPProvider | {3dd6bec0-8193-4ffe-ae25-e08e39ea4063} |
| Secondary Authentication Factor Credential Provider | {48B4E58D-2791-456C-9091-D524C6C706F2} |
| CngCredUICredentialProvider | {600e7adb-da3e-41a4-9225-3c0399e88c0c} |
| PasswordProvider | {60b78e88-ead8-445c-9cfd-0b87f74ea6cd} |
| FaceCredentialProvider | {8AF662BF-65A0-4D0A-A540-A338A999D36F} |
| Smartcard Credential Provider | {8FD7E19C-3BF7-489B-A72C-846AB3678C96} |
| Smartcard Pin Provider | {94596c7e-3744-41ce-893e-bbf09122f76a} |
| Remote NGC Credential Provider | {A910D941-9DA9-4656-8933-AA1EAE01F76E} |
| WinBio Credential Provider | {BEC09223-B018-416D-A0AC-523971B639F5} |
| Cloud Experience Credential Provider | {C5D7540A-CD51-453B-B22B-05305BA03F07} |
| IrisCredentialProvider | {C885AA15-1764-4293-B82A-0586ADD46B35} |
| PINLogonProvider | {cb82ea12-9f71-446d-89e1-8d0924e1256e} |
| NGC Credential Provider | {D6886603-9D2F-4EB2-B667-1971041FA96B} |
| CertCredProvider | {e74e57b0-6c6d-44d5-9cda-fb2df5ed7435} |
| WLIDCredentialProvider | {F8A0B131-5F68-486c-8040-7E8FC3C85BB6} |
| FIDO Credential Provider | {F8A1793B-7873-4046-B2A7-1F318747F427} |
Identifying the Installation Source of a Third-Party Credential Provider
If lastLoggedOnProvider is a GUID that does not belong to the Specops client or a default Windows credential provider, check its name under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{GuidOfCredentialProvider} as was done in the previous section. Often the names of these providers can be a bit cryptic; if you do not recognize it by name in the registry here, we can dig a bit deeper by looking for the DLL that contains the code for that credential provider.
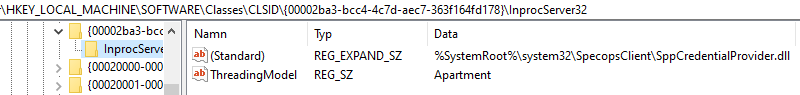
Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{LastLoggedOnProviderGuid}\InprocServer32. For example, here we will look at the credential provider for the Specops Client:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00002ba3-bcc4-4c7d-aec7-363f164fd178}\InprocServer32InprocServer32’s (standard) value will be a DLL file name or path. This is the DLL that is loaded at the Windows logon screen for that credential provider. If no absolute path is specified, the DLL is somewhere in the default path, most likely c:\windows\system32.
Go to the DLL in a file explorer and right-click Properties to check the Details and Digital Signatures tabs. You should find vendor information about the DLL and the name of the program that it was installed with:
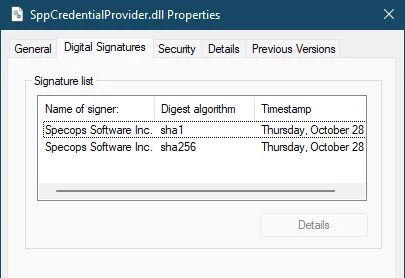
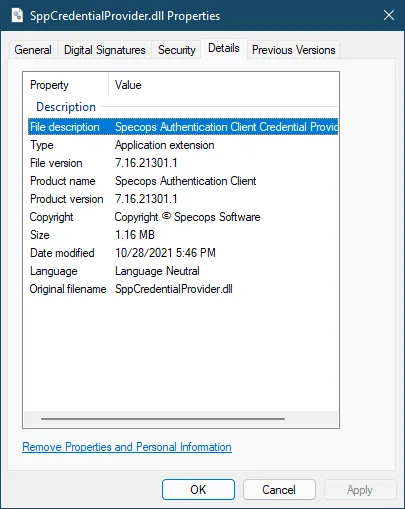
If the credential provider is something you expected to find installed, we can configure the Specops Client to wrap that provider. Note for McAfee Full Disk Encryption customers: if no other third-party credential providers are installed in addition to McAfee, no Specops configuration is necessary.
Wrapping Custom Credential Providers with the Specops Client
Using the Group Policy ADMX Template
Install the Specops Client ADMX Template to either the local policy definitions folder or your Active Directory central store if you have not done so already.
Create (or us an existing) GPO applied to the computers where both the Specops Client and third-party credential provider are installed.
Configure the following setting:
Computer Configuration/Policies/Specops Client/Enhance Windows logon and password change/GUID of credential provider to wrap
Enabled
Guid: GUID of the third-party credential provider including the surrounding curly brackets, e.g. {12345678-90AB-CDEF-1234-567890ABCDEF}

Using the Registry
While we recommend using the client ADMX template, often for testing or remote users we must create the registry keys that the ADMX would create through some other means.
For specifying which credential provider to wrap, create the following string value in the registry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Specopssoft\uReset\Client\CredentialProvider]
"WrappedCredentialProviderGuid"="{12345678-90AB-CDEF-1234-567890ABCDEF}"Change the GUID value to the appropriate GUID for the credential provider you want to wrap. Be sure to include the curly brackets {} in the value.
Further Troubleshooting
If after wrapping the third party provider you experience either a degradation in the Windows logon experience with that provider, or still do not see the Specops Password Policy detailed error message and/or Reset Password link, it may be necessary to perform additional configuration in that third party credential provider. Often the third party provider will require additional configuration to allow the Specops client to wrap it, or they may say instead require that their client wraps the Specops provider. The exact details vary from vendor to vendor; you will need to reach out to that vendor’s support channel for more information.
