Will making changes to my password policy force my end users to change their password?
Short answer: It depends
Situation where it depends
If you disable length-based password aging, the user(s) will then be subjected to the normal maximum password age.
Situations where the user will not be forced to change their password:
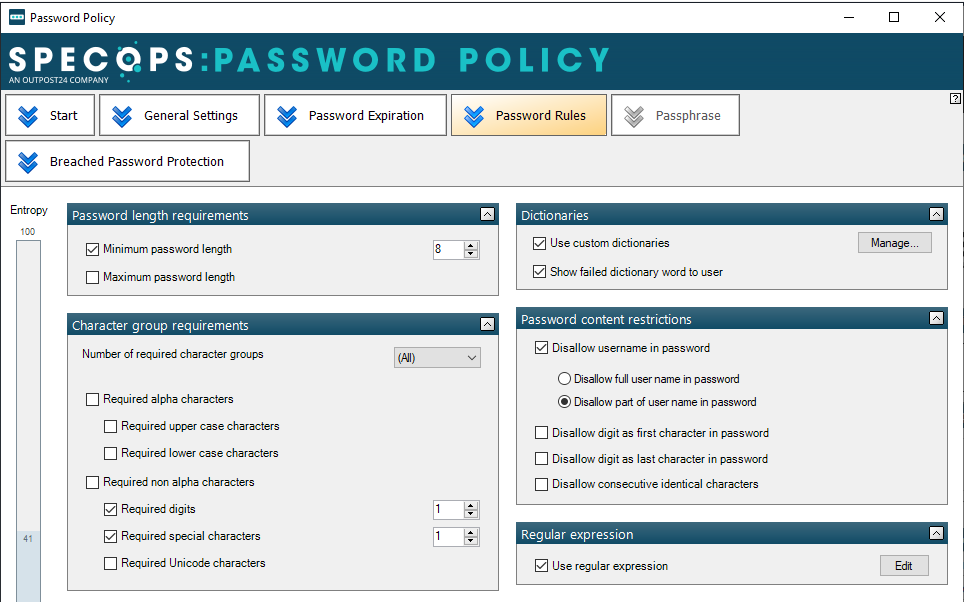
- Adjusting password complexity (this is checked the next time a user changes their password)
- Adding words to a custom dictionary (this is only checked when a user changes their password)
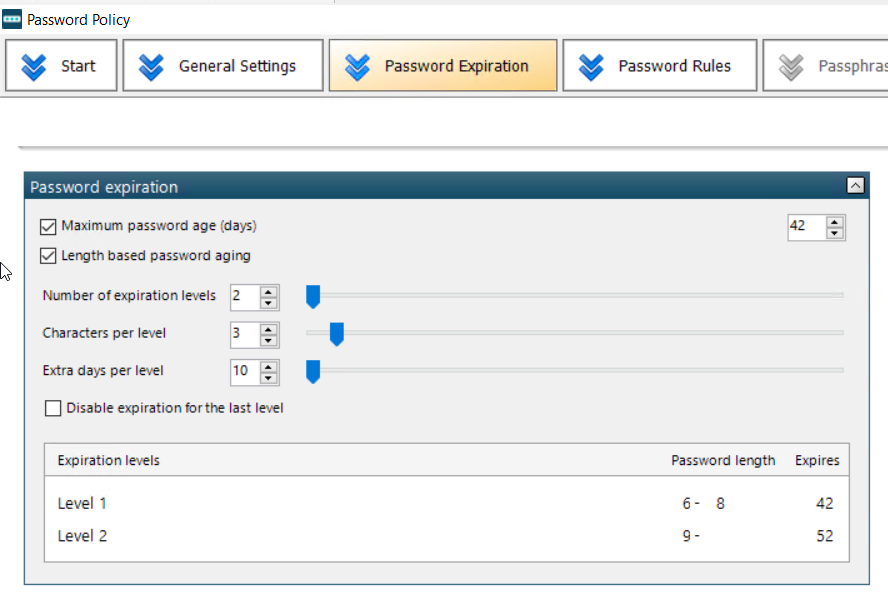
- Adjusting a length-based password aging policy (example below)
If the user sets their password based on this current policy, we see their sub-object has a flag value of 52 (representing the number of days of till expiry based which will calculate from the pwdlastset date). If we adjust the level 2 tier to a different number of days, this will not modify this flag value and the password will still expire based on the initial expiry date calculated from the old policy. If the user changes their password, they will then be subjected to the new length-based aging policy.

Situations where the user will be forced to change their password:
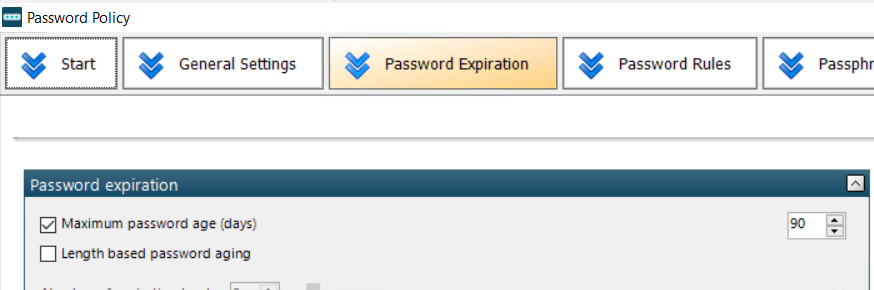
Max Password Age without length-based password aging.
If Max password age is adjusted from what the setting is currently to something lower and the user meets said threshold, they will be required to change their password.
Here is an example with 90 days as an example. The user will have to change their password on 3/29/2024.

If the Max password age is adjusted to lower the threshold to 42 days, as seen below:
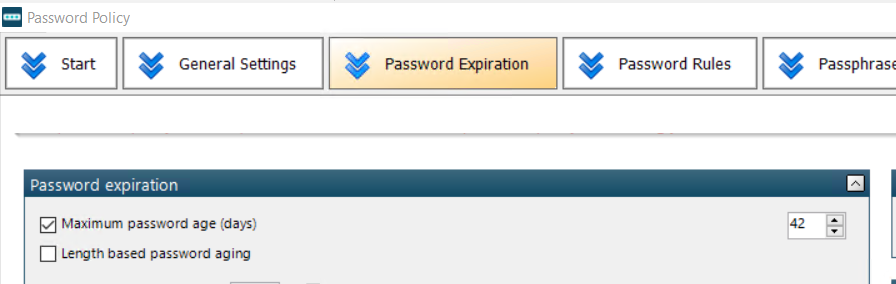
The password will have expired as the date has already passed and after the sentinel performs periodic scanning at midnight (by default) user will be forced to then change their password at next logon:
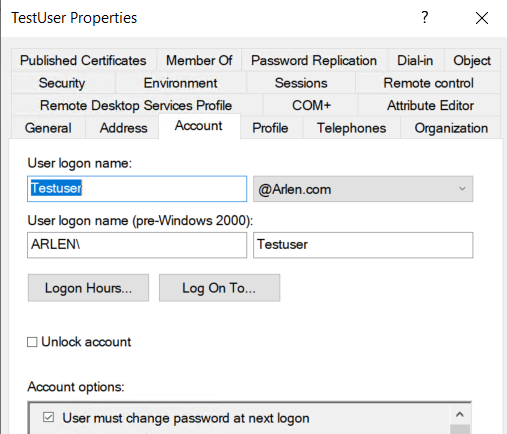
For a more detailed guide on password expiration, please view this article
Breached Password Protection Continuous
If the “Check for leaked passwords continuously” using either the complete api or the express list and “Force users to change compromised passwords” options are enabled and periodic scanning runs at midnight (by default), then any users with passwords found on this list will be forced to change them at next logon:

