uReset Could Not Load the SPP Policy Content
This article applies to uReset when used in a multi-domain environment.
When using uReset and Password Policy in multiple trusted domains/forests, you may find that users accessing uReset from domains other than the Gatekeeper domain do not see the Password Policy rules when setting their new password. When this occurs, you will find event ID 2037 logged in the Specops application event log on the Gatekeeper server:
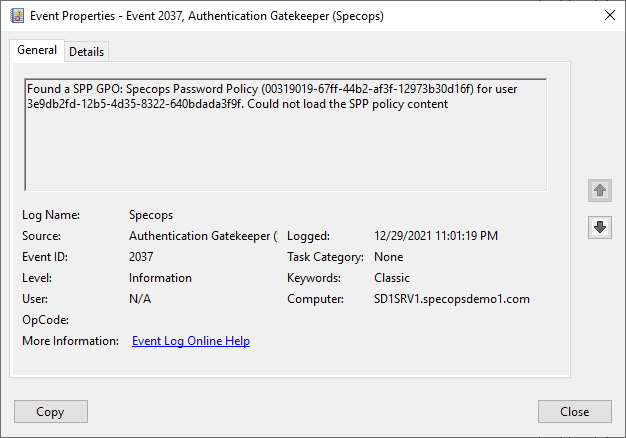
This error indicates the Gatekeeper was able to identify a Password Policy GPO applied to the end user but was unable to read the details of that policy from SYSVOL. The Gatekeeper is attempting to read the policy INI file in SYSVOL in the trusted domain but is unable to do so.
To validate this issue, attempt to browse to the SYSVOL share in a DC in the user domain. For example, if your Gatekeeper is in specopsdemo1.com, your user is in specopsdemo2.com, and there is a domain controller in specopsdemo2.com named SD2DC1, then browse to \\SD2DC1.specopsdemo2.com\SYSVOL. If you are prompted for credentials and/or receive an access denied message, this confirms we have an issue connecting to SYSVOL in that domain.
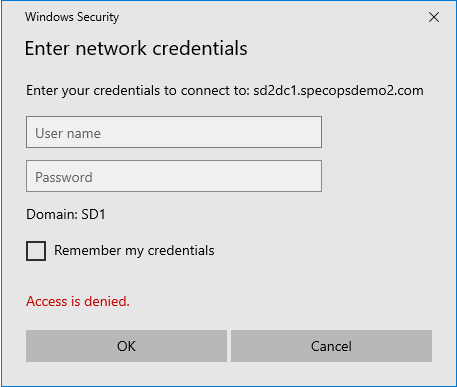
The reason for this typically comes down to Kerberos authentication. Modern versions of Windows require Kerberos mutual authentication to connect to the SYSVOL share.
To determine how to proceed from here, we should check the type of trust used between the Gatekeeper domain and the user domain. Open Active Directory Domains and Trusts on a domain controller in the Gatekeeper domain, right-click Properties on the domain, and go to the Trusts tab:
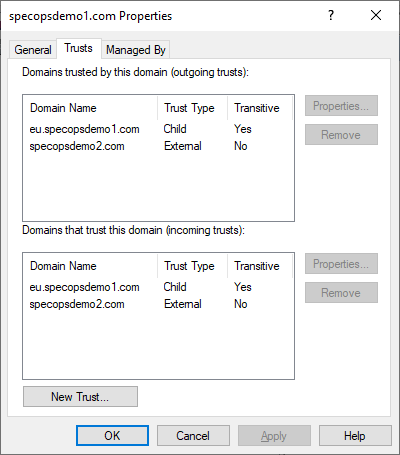
External Trusts
If the user domain (specopsdemo2.com in this example) is listed as an external trust, it is expected that Kerberos mutual authentication to SYSVOL there will fail by default. To correct this, we must make a change to the local group policy on the Gatekeeper (or a GPO applied to the Gatekeeper server(s) from Active Directory). Here we will make the change locally on the Gatekeeper:
- Run gpedit.msc
- Navigate to Computer Configuration/Administrative Templates/System/Kerberos
- Edit the Use Forest Search Order setting.
- Enable the setting and add the external trusted domain to the list of forests to search. Note: you do not need to add the Gatekeeper domain to this list.
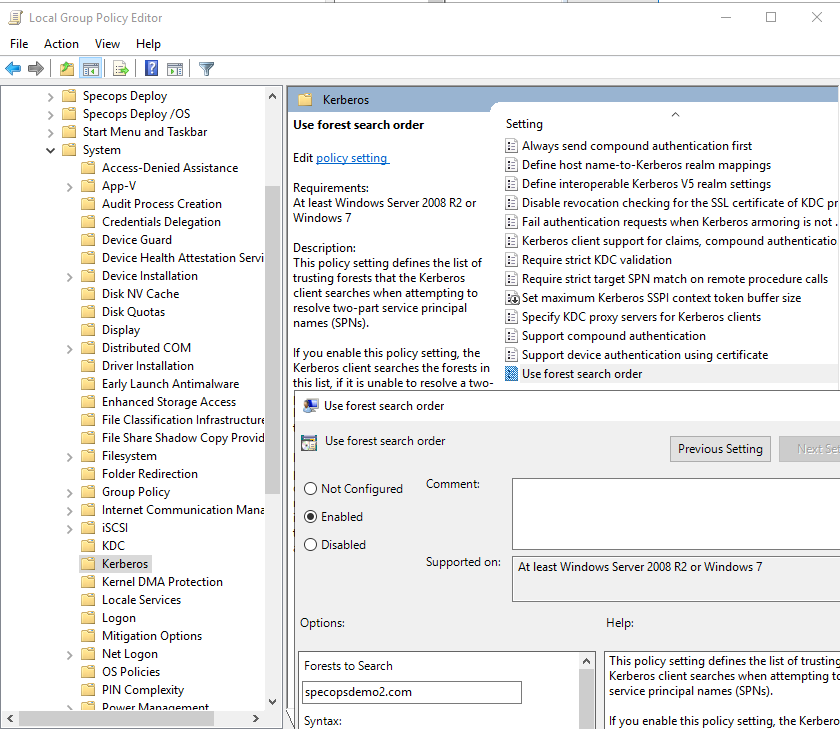
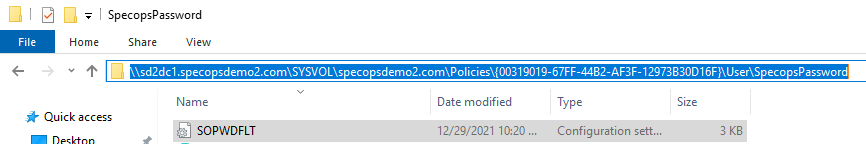
Once this policy is applied, you should now be able to open the Password Policy INI file in the trusted domain. In this example, the file is \\sd2dc1.specopsdemo2.com\SYSVOL\specopsdemo2.com\Policies{00319019-67FF-44B2-AF3F-12973B30D16F}\User\SpecopsPassword\SOPWDFLT.INI
Child and Forest Trusts
If you cannot browse SYSVOL in a domain that has a child or forest trust with the Gatekeeper domain, this is a bit unusual. Specops recommends investigating the reason for this failure as it may also cause and/or be the result of other unexpected issues in your environment. As a workaround, you can disable the requirement for Kerberos mutual authentication from your Gatekeeper server to the trusted domain.
In the local group policy editor (run gpedit.msc) on the Gatekeeper server, navigate to Computer Configuration/Administrative Templates/Network/NetworkProvider and edit the Hardened UNC Paths setting.
Enable the setting, then under Hardened UNC Paths, set a value name of \\*.trustedomain.com\SYSVOL and a value of RequireMutualAuthentication=0,RequireIntegrity=1
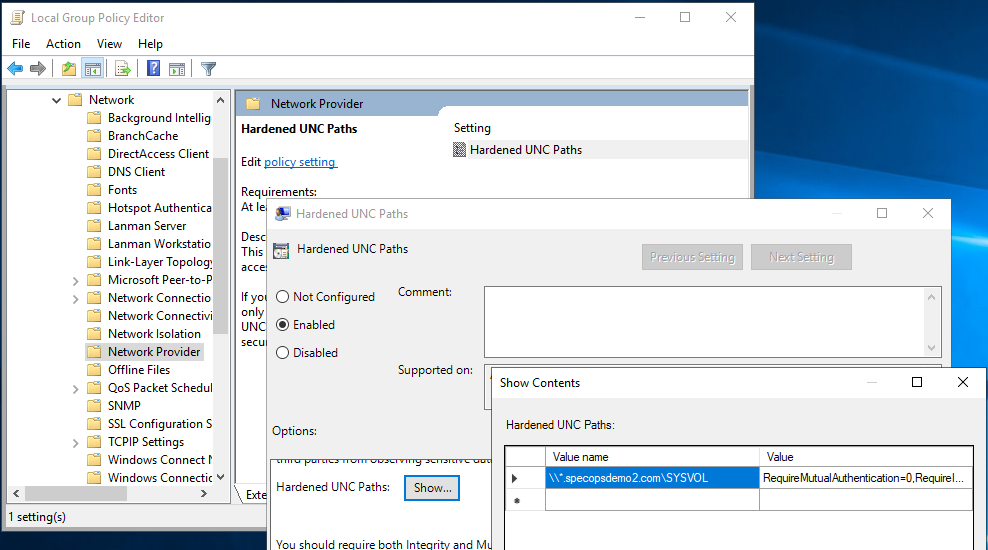
Once this setting is applied, you should be able to browse to the Password Policy INI file in the trusted domain. In this example, the file is \\sd2dc1.specopsdemo2.com\SYSVOL\specopsdemo2.com\Policies{00319019-67FF-44B2-AF3F-12973B30D16F}\User\SpecopsPassword\SOPWDFLT.INI

