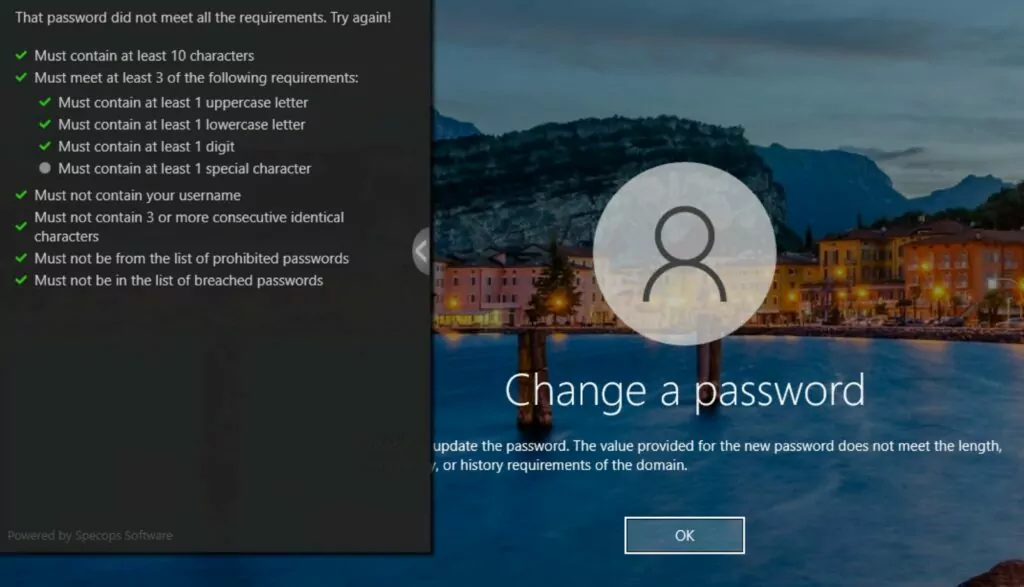
Specops Client RulesUI Troubleshooting
The Specops Client (version 7.15 and later) provide real-time feedback to end users as they are changing their passwords through CTRL+ALT+DEL Change Password…
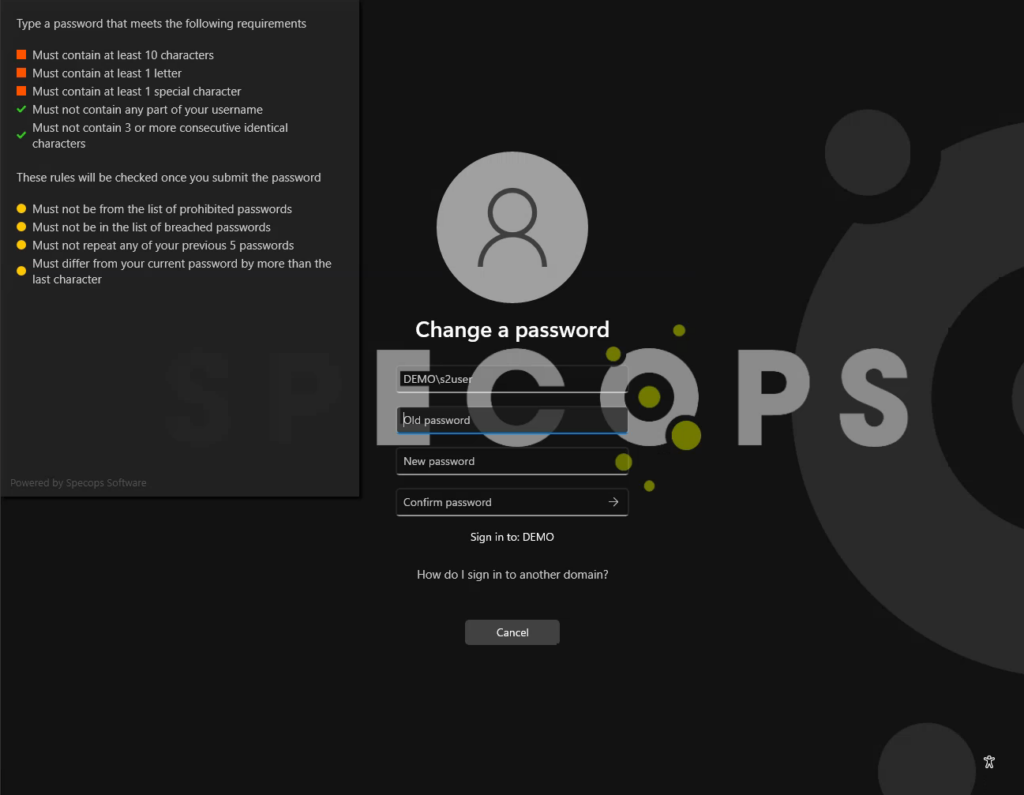
The client runs under the context of the machine’s system account and uses the computer account in Active Directory to resolve information about the end user and applied password policies.
In most environments, this behavior will work out of the box with no additional changes in Active Directory. In certain high security requirements, the client may be unable to provide the rules feedback. Known issues that may occur:
Username Not Found
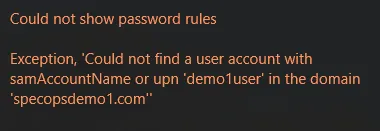
Could not show password rules Exception, 'Could not find a user with the samAccountName or upn 'username' in the domain 'domain.com'
This error can occur if the computer account cannot find the user in AD. The following permissions are required to look up users:
- OUs containing users:
- List contents
- Read all properties
- User accounts
- Read general information
- Read public information
- Read userAccountControl
To grant these permissions to Domain Computers, use the following PowerShell as a domain admin from a command prompt on a domain controller. Update the OU path in the script to match your environment.
$userOU = "OU=Users,OU=Specops,DC=specopsdemo1,DC=com" $domainNetBIOSName = $(get-addomain).netBIOSName # Grant read access to root OU dsacls $userOU /G "$domainNetBIOSName\Domain Computers:RP" "$domainNetBIOSName\Domain Computers:LC" | out-null # Grant read access to sub-OUs dsacls $userOU /I:S /G "$domainNetBIOSName\Domain Computers:RP;;organizationalUnit" "$domainNetBIOSName\Domain Computers:LC;;organizationalUnit" | out-null # Grant read access to user objects dsacls $userOU /I:S /G "$domainNetBIOSName\Domain Computers:RP;userAccountControl;user" "$domainNetBIOSName\Domain Computers:RP;general information;user" "$domainNetBIOSName\Domain Computers:RP;public information;user" | out-null
Specops Password Policy rules are not displayed
In this case the client loads the policy rules, however only the rules from the Active Directory policy are shown. This typically happens when your Specops Password Policy is filtered on a security group and the client cannot resolve the user’s group membership. To resolve this, grant domain computers access to read the tokenGroups attribute on user accounts. Update the OU path in the script to match your environment:
$userOU = "OU=Users,OU=Specops,DC=specopsdemo1,DC=com" $domainNetBIOSName = $(get-addomain).netBIOSName dsacls "OU=Users,OU=Specops,DC=specopsdemo1,DC=com" /I:S /G "$domainNetBIOSName\Domain Computers:RP;tokenGroups;user" | out-null
Fine-Grained Policy cannot be read
In this case the user is affected by an Active Directory fine-grained password policy and either the rules from that policy are not displayed at all, or the client reports that the fine-grained policy could not be read:
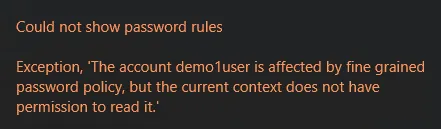
Could not show password rules Exception, 'The account username is affected by a fine grained password policy, but the current context does not have permission to read it.'
In this case, we must ensure Domain Computers have explicit rights to read fine-grained policies in Active Directory by granting read access to the System\Password Settings Container object in Active Directory and all descendant objects.
$domain = get-addomain $domainNetBIOSName = $domain.netbiosname $psoContainer = "CN=Password Settings Container,$($domain.systemscontainer)" dsacls $psoContainer /I:T /G "$domainNetBIOSName\Domain Computers:RP" | out-null
3rd party Password Filters
If everything comes back green, check for 3rd party password filters rejecting the password (including but not limited to Azure Password Protection)