This website uses cookies to ensure you get the best experience on our website. Learn more

How we use Threat Intelligence to find new breached passwords
Table of Contents
What makes a good breached password list? Numbers are a good start – the more breached passwords you can cross-reference against your Active Directory, the better. You want to maximize your chances of detecting end users who are using compromised passwords.
However, quality matters too. Take Rockyou2024, a password list claimed by a poster on an underground forum to be the biggest list of breached passwords ever. But when analyzed by one our technicians, the Rockyou2024 database dump was found to be mostly garbage data.
In contrast, the Specops breached password database contains over 4 billion unique passwords that are known to have been breached or compromised. Our database is made up of three key sources:
- Publicly-available breached password lists from reputable sources such as Haveibeenpwned
- Passwords from our real-time attack monitoring system that monitors live brute force attacks. Specops maintains a global honeypot system which collects passwords used in real attacks on the system’s endpoints
- Malware-stolen data from our human-led Threat Intelligence team
This third data source (Threat Intelligence) is particularly interesting, as it contains passwords stolen from real people that you’re unlikely to find in publicly available lists. We’ll explain how our team uses threat intelligence to find breached credentials and how this help keep our customers’ Active Directories secure from password-related breaches.
How do we use threat intelligence to find breached passwords?
Outpost24 (Specops’ parent company) has a dedicated team of Threat Intelligence analysts called KrakenLabs. They continuously search the open, deep, and dark web to discover customer-specific threat information, using automated technology to help with speed and scale. The team retrieve and deliver this intelligence in a modular format, giving customers a straightforward way to confront external cyberthreats and manage their digital risk. On top of that, they contribute valuable information to the Specops team in the form of malware-stolen credentials.
KrakenLabs have infiltrated several botnets (groups of internet-connected devices infected by malware and under the control of a malicious actor) where they are able to intercept communications. Among other information, passwords harvested by the malware are collected. They have also established communication with insiders who provide plenty of valuable information, including lists of breached credentials. On top of that, they have several operatives infiltrated in underground forums and dark net organizations. For example, traffer groups who use malware infection to harvest credentials and profit from them.
The Threat Intelligence team are constantly monitoring public spaces where this kind of information might be shared, such as underground forums and marketplaces on the dark web. There are also some methods we can’t share in this post – the team’s knowledge of the inner workings of malware, cybercriminal enterprises, and the infrastructures they use has also allowed them to create both secret and patented methods of credential gathering and information curation.
How does access to malware-stolen credentials help Specops customers?
The breached passwords turned up by our Threat Intelligence team are real credentials, actively being used by real people at the moment we obtain them. This differentiates them from passwords found in wordlists or a dictionary, which might have been generated by applying algorithms or based in previous and provably outdated data. These are real passwords in active use. The freshness and genuineness of these legitimate credentials helps in curating a more comprehensive database, providing more value to our Specops Password Policy customers.
Specops Password Policy with Breached Password Protection allows organizations to continuously scan their Active Directory against our database of 4 billion breached passwords. The continuous scan feature checks all Active Directory passwords against the Breached Password Protection API for compromise once a day. The API is updated daily with newly discovered compromised passwords from our password honeypot system, newly discovered password leaks when they occur, and malware-stolen credentials from the KrakenLabs team.
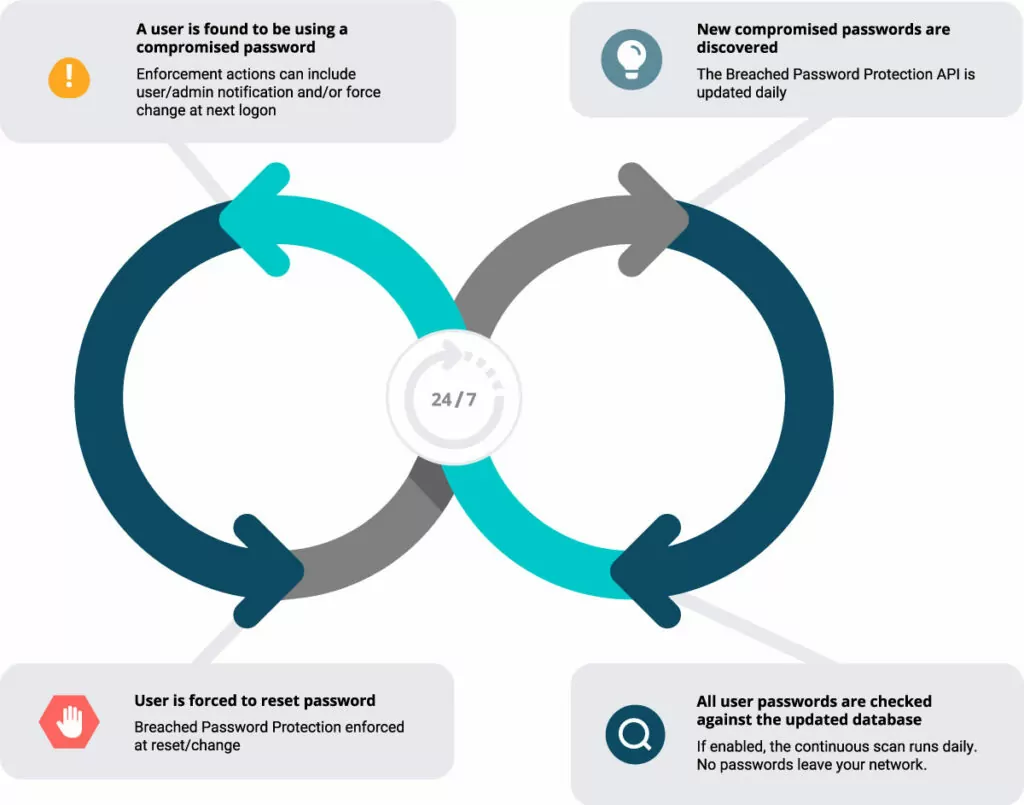
If an end user is found to be using a breached password, they’re notified and forced to change. This closes off compromised passwords as simple attack routes into your organization for hackers.
Interested to see how Specops Password Policy could fit in with your organization? Try it for free today.
(Last updated on May 14, 2025)

