This website uses cookies to ensure you get the best experience on our website. Learn more
NIST Password Reset Guidelines
Table of Contents
Passwords are necessary for authentication to different types of technology systems used in businesses today. Yet, they are a dangerous form of information from a security perspective. To strengthen password security, organizations want to take note of password best practices noted by security organizations.
The National Institute of Standards and Technology (NIST) has long provided guidance on securing authentication to critical, or sensitive systems. What NIST best practices can your organization adopt to help bolster security for the passwords used in your environment?
Why passwords are dangerous
Passwords are a dangerous form of information that can lead to all kinds of risks for your data and services. Compromised credentials are noted as one of the primary culprits in major data breaches. According to the 2020 IBM Cost of a Data Breach report, “stolen or compromised credentials were the most expensive cause of malicious data breaches.”
You may wonder, how are end-user credentials compromised? Attackers use many different types of techniques to compromise credentials. Cybercriminals may harvest passwords by installing malware on end-user PCs, using keyloggers, or other malicious code. Phishing emails attempt to persuade end-users to click malicious links or divulge their credentials through an online web form. Attackers may use social engineering attacks to convince end-users to disclose security information inadvertently. Cybercriminals also perform many types of password attacks to compromise credentials. These include using lists of breached passwords in a password spraying attack to compromise user accounts with known passwords.
NIST recommended password best practices
Let’s examine a few of the NIST password recommendations that can help bolster password security in your environment. You may notice that NIST is advocating newer concepts as part of the latest recommendations.
- End-users should have clear direction on memorized secrets (passwords) and how to change those effectively.
- Allow at least 64 characters in length to support the use of passphrases. Encourage users to make memorized secrets as lengthy as they want, using any characters they like (including spaces), thus aiding memorization.
- Do not impose other composition rules (e.g., mixtures of different character types) on passwords.
- Do not require that passwords be changed arbitrarily (e.g., periodically) unless there is a user request or evidence of authenticator compromise. (See Section 5.1.1 for additional information).
Another important password security best practice to note is expressed in the following recommendation in section 5.1.1.2. Note the following regarding breached passwords, dictionary, repetitive or context-specific passwords:
When processing requests to establish and change memorized secrets, verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised. For example, the list MAY include, but is not limited to:
- Passwords obtained from previous breach corpuses.
- Dictionary words.
- Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’).
- Context-specific words, such as the name of the service, the username, and derivatives thereof
As you can see, many of the recommendations help to mitigate the different types of attacks that are commonly used by attackers today.
Another security threat around password resets
With the global pandemic and a large remote workforce, service desk professions have to work with remote end-users to reset forgotten passwords or locked accounts due to too many failed logins. Service desk technicians who interact with remote employees will generally work with the end-user over the phone.
What if an attacker calls into the service desk and poses as a legitimate employee? How can service desk professionals validate the identity of the remote end-user? Some organizations use a very basic set of questions to help validate the identity of an end-user. However, attackers can scrape much of the commonly used information from social media sites or other personal information posted elsewhere by end-users. In its latest recommendations, NIST no longer recognizes security questions as an acceptable authenticator, for the same reasons mentioned above.
Specops Secure Service Desk provides a solution that allows helpdesk technicians to reset end-user passwords via human interaction in a secure way. When working with end-users on the phone, service desk technicians can use the Secure Service Desk solution to verify their identity by enforcing the use of the identity services to which the end-user has enrolled. Users can enroll with multi-factor technologies such as authenticator apps and mobile codes. When a user registers with a mobile code linked to their account in Active Directory, the helpdesk technician sends the code to the end user’s phone, allowing identity verification.
The workflow for the Specops Secure Service Desk looks like the below. The helpdesk technician has initiated the mobile code push to the end user’s phone. Once the user receives the code, they repeat the code back to the technician. The technician enters the code, validates the identity, and continues with the password reset. This identity verification ensures that attackers cannot effectively use a social engineering attack to compromise an account password.
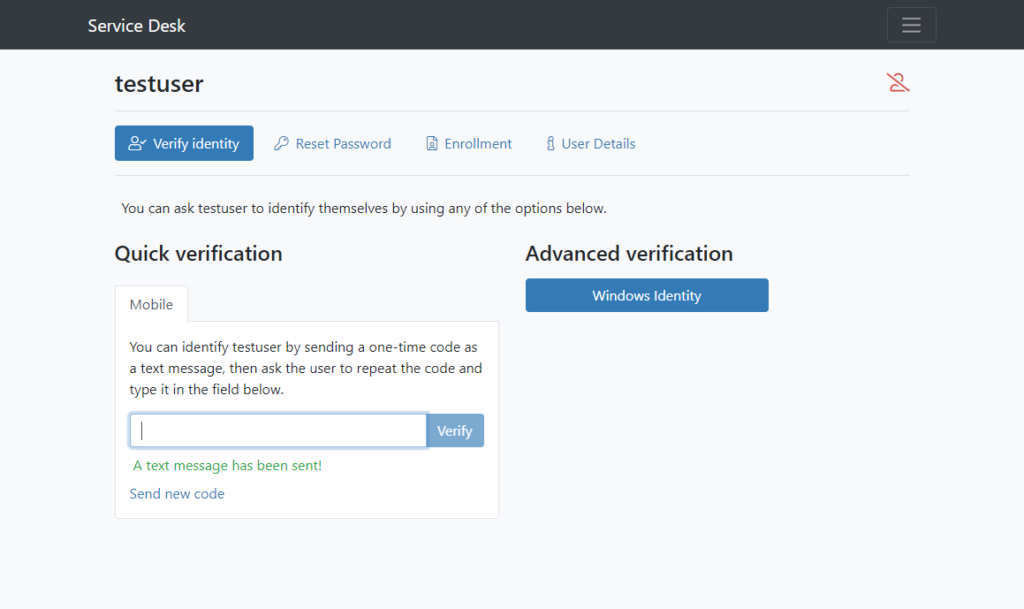
Besides offering the Secure Service Desk solution, Specops provides a fully-featured Password Policy solution that provides the additional protection needed in Active Directory environments against breached and weak passwords.
Concluding thoughts
There are many different dangers to account passwords. By following the latest NIST password recommendations, among others, organizations can bolster account security. Traditional password security techniques fall short in protecting user accounts. For example, forcing periodic password changes does not strengthen password security, especially if the password has not been compromised. Instead, remediating password breaches as soon as they happen or checking for breached passwords proactively and preventing these from being used is the better approach. Organizations must also keep password reset security in mind with remote end-users. Cybercriminals may use social engineering attacks to pose as a legitimate end-user to compromise a password with a password reset request. Using effective tools such as Specops Secure Service Desk and Specops Password Policy can help organizations protect against social engineering attacks and breached passwords in the environment.
(Last updated on March 18, 2025)


