This website uses cookies to ensure you get the best experience on our website. Learn more
How to evaluate breached password detection services
Table of Contents
Keeping tabs on breached passwords is a must for those embroiled in the IT security battle. According to the 2020 Data Breach Investigations Report, 80% of data breaches in 2020 stemmed from stolen or brute-forced credentials. The stakes are high. Just one problematic endpoint in your environment can cause far-reaching consequences.
Consequently, organizations have come to rely on breached password detection or banned password lists. Active Directory (AD) remains a leading player for scalable infrastructure management. What does it offer out of the box? Microsoft maintains an integrated, global list of banned passwords based on AD telemetry data.
While useful, this default list only includes about 1,000 terms. Additionally, the list doesn’t compile data from external sources, ultimately limiting its breadth and responsiveness to industry breaches. The custom banned password list is more IT-configurable and carries more contextual value. However, it only includes 1,000 terms, while placing the update onus on administrators.
We thus have two main problems at hand. Banned password lists are limited in their scope, and require frequent, manual upkeep.
Teams already have enough on their plates. It’s a major reason why companies are supporting their password policies with third-party tools. So, what should you look for when evaluating these solutions? We’ll discuss what to look for in this guide to breached password detection services.
Breached password detection: key features
Managed password list updates
Almost all sysadmins working within AD can benefit from some type of automation. There’s plenty of lost time to gain back in making common tasks more efficient, or eliminating them from the to-do list altogether.
Let’s first zero in on passwords lists. Manual list updates can be a pain, and doubly so when admins have to gather data themselves. Maintaining banned passwords lists can be challenging.
Furthermore, teams must remember to push these updates to their respective domain controllers. That’s not as straightforward as it seems. Applying updates means rebooting controllers and other resources, contributing to environmental downtime, since these processes can take hours.
What you should seek is a third-party solution that handles password list updates in the background. That includes server-based additions to external lists, combing for breached passwords, and applying dictionary updates to all user accounts.
Don’t forget network visibility, either. While inspecting your domain trees is fairly straightforward, drilling down into groups, users, and credentials is relatively tedious. Manual assessment of password policy adherence is time consuming.
As an admin, you might have to inspect hundreds of accounts and compare them against checklists. External tools can do this legwork for you. Look for something that can inspect domain policies, fine-grained password policies, and generate reports on password vulnerabilities. That time saved can be poured into immediate remediation.
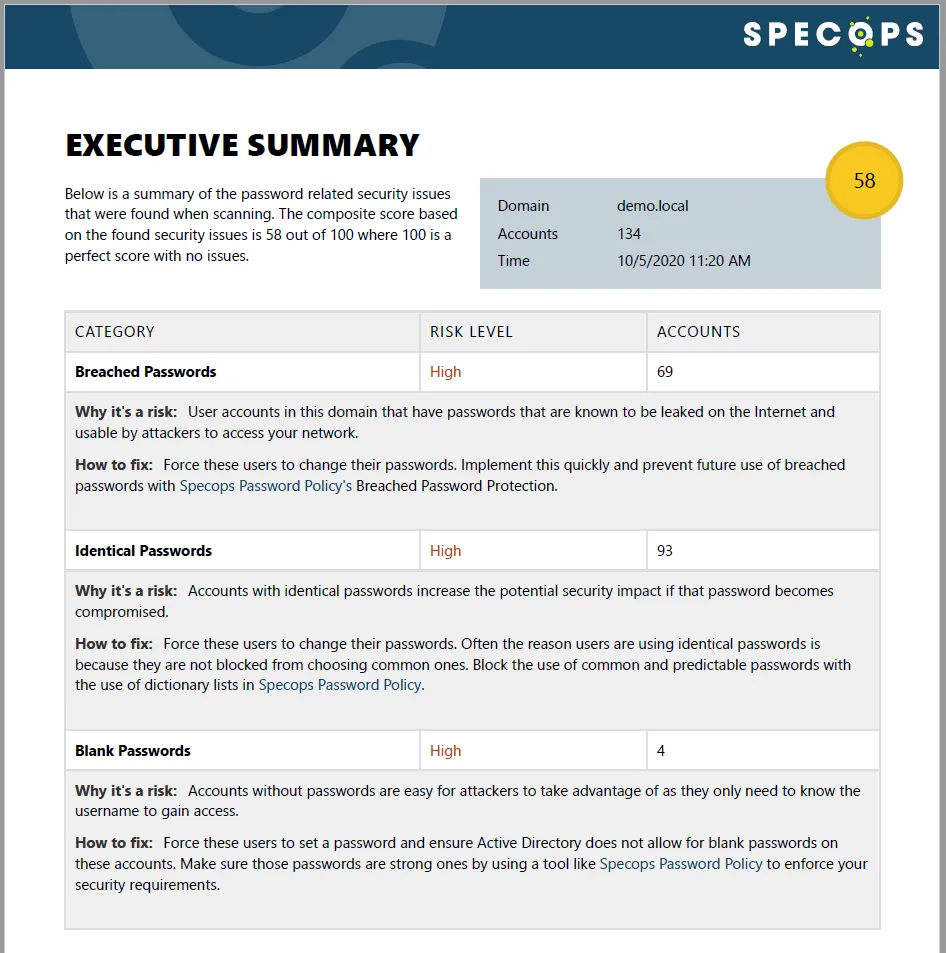
Comprehensive banned passwords databases
So, we know all of these banned passwords are floating around out there. Additionally, Microsoft’s global lists, while helpful, aren’t nearly adequate enough to mitigate the lingering effects of past breaches.
Consider this: if Microsoft’s global list were entirely devoted to passwords from Yahoo’s breaches, it wouldn’t even include 0.000033% of those compromised passwords! It’s clear that third-party tools are necessarily to supplement Active Directory’s own databases. Who keeps tabs on these leaked passwords?
Firstly, companies that develop these security solutions maintain their own lists. These dictionaries may be downloadable and applicable to your environment. Popular passwords, patterns, and leetspeak are critically-important inclusions.
Some tools even pull from databases like Have I Been Pwned, via APIs. This popular website alone currently tracks over 613,000,000 compromised passwords across the web. Others might opt to pull information from alternatives like BreachAlarm. Either way, there’s a mountain of supplemental data that can help bolster your password security. Specops Password Policy, for example, checks your passwords against over 4 billion leaked passwords (via the breached password detection add-on).
Compliance-centered
While putting together strong password policies should be ubiquitously crucial, some industry requirements are more stringent than others. PCI, HIPAA, SOX, and NIST mandate strong password security (among other controls). Banned passwords are huge no-no, and password breaches have heavily impacted these industries in the past.
Past, high-profile breaches of Yahoo, Equifax, and LinkedIn come to mind, which account for the theft (and sale) of billions of passwords. In many cases, these passwords weren’t hashed.
Why does that matter? A massive chunk of these passwords is now in the wild, often because those companies and others have failed to follow best practices. There’s a reason why many breaches incur fines. Conversely, a quality password auditor can compare your policies to existing standards, and clearly display fine-grained compliance levels. Just make sure industry-relevant analysis is provided.
The best tools are feature rich
Whether you opt for a free or paid tool, there are numerous options to satisfy diverse preferences. One tool might have a subjectively-better GUI than another. One might present data more clearly. Another might be more performant than its competitors. These ancillary benefits support the primary mission at hand: improving password security. You’ll want to choose a tool that’s easy to use, presents its findings clearly, and casts a wide net. We recommend Specops Password Policy and even Specops Password Auditor (Free) for breached password detection.
(Last updated on February 19, 2025)