This website uses cookies to ensure you get the best experience on our website. Learn more
Are password reset solutions still relevant?
Table of Contents
In case you haven’t been keeping up with the latest password guidance from noted cybersecurity organizations, it has changed from the traditional advice given regarding password security and password security policies. There are new and better ways to protect and secure account passwords than legacy password policy configurations.
One of the areas of password policy guidance that been the subject of changes in recommendations is password expiration. How have standards regarding password expiration changed in recent years? Even if the password expiration guidance has changed, your business may still be subject to password changes for various reasons, such as compliance regulations.
New guidance on password expiration
The National Institute of Standards and Technology (NIST) is one source of the changed guidance regarding password expiration policies.
NIST is a leading authority in the realm of cybersecurity recommendations and policy frameworks. The NIST Special Publication 800-63B Digital Identity Guidelines SP 800-63B Section 5.1.1.2 paragraph 9 states:
Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
In the NIST Special Publication 800-63: Digital Identity Guidelines Frequently Asked Questions, NIST explains the change in guidance this way:
Users tend to choose weaker memorized secrets when they know that they will have to change them in the near future. When those changes do occur, they often select a secret that is similar to their old memorized secret by applying a set of common transformations such as increasing a number in the password. This practice provides a false sense of security if any of the previous secrets has been compromised since attackers can apply these same common transformations. But if there is evidence that the memorized secret has been compromised, such as by a breach of the verifier’s hashed password database or observed fraudulent activity, subscribers should be required to change their memorized secrets. However, this event-based change should occur rarely, so that they are less motivated to choose a weak secret with the knowledge that it will only be used for a limited period of time.
What about Microsoft who developed Active Directory Domain Services (ADDS) that provides the majority of enterprise environments today with password policy?
Microsoft’s Security baseline for Windows 10 v1903 and Windows Server v1903 has dropped password expiration policies. Why is this the case?
As quoted from Microsoft regarding the new guidance:
Recent scientific research calls into question the value of many long-standing password-security practices such as password expiration policies, and points instead to better alternatives such as enforcing banned password lists (a great example being Azure AD password protection) and multi-factor authentication. While we recommend these alternatives, they cannot be expressed or enforced with our recommended security configuration baselines, which are built on Windows’ built-in Group Policy settings and cannot include customer-specific values.
A key takeaway from the guidance published by both NIST and Microsoft is that banned password lists, including breached password protection, is the recommendation moving forward. However, are there situations and regulations that may still require your organization to make use of password expiration policies?
When password expiration is still needed
Regardless of new guidance in the cybersecurity industry, some situations and regulations require organizations to give attention to password expiration policies. The Payment Card Industry Data Security Standard (PCI-DSS) is a set of requirements to help protect customer credit card information for companies that process, store, or transmit credit card information. For businesses under the regulatory purview of PCI compliance, password expiration policies are a component of the overall security required by PCI standards. Under Section 7.2 Password Control of the document Payment Card Industry (PCI) Card Production and Provisioning – Logical Security Requirements, the following password expiration requirement is set forth by PCI: Passwords have a maximum life not to exceed 90 days and a minimum life of at least one day.
Even with the updated guidance leaning towards eliminating password expiration policies, businesses who are obliged to comply with PCI-DSS must follow the requirements as defined by the PCI Security Standards Council. Time will tell if the next draft of PCI recommendations will see new requirements based on the industry’s latest guidance.
Implement banned-password list and breached password protection
For businesses who fall under regulatory compliance such as PCI-DSS, and must currently use a password expiration policy, a custom dictionary and breached password protection can significantly bolster password security. However, this can be challenging since there is no native way to do this in Active Directory Domain Services (ADDS).
Using Specops Password Policy, organizations can quickly implement password rules for custom dictionaries and breached password protection. With Specops you can check passwords against the latest breached password information, and require users with leaked passwords to change them.
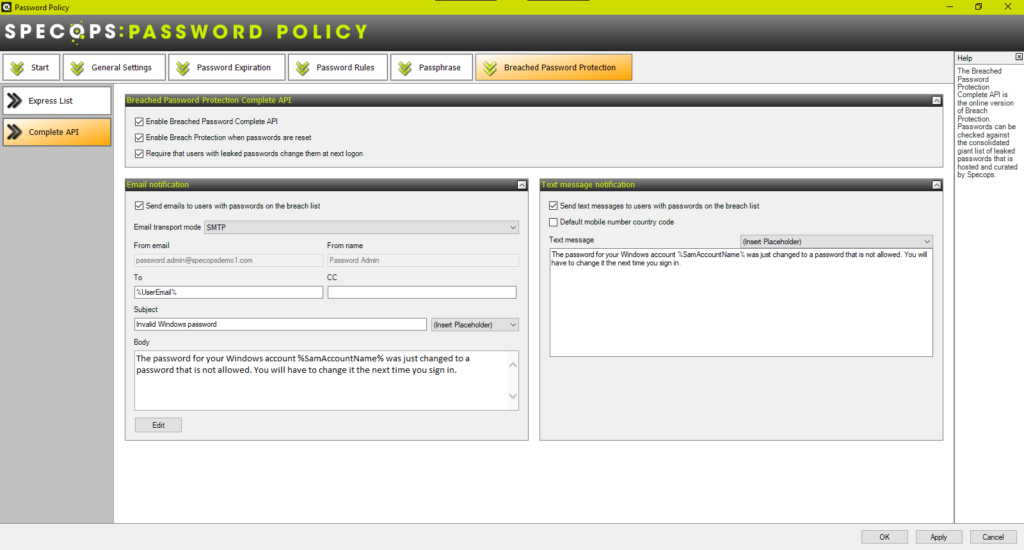
Concluding thoughts
Both NIST and Microsoft have changed the recommendations regarding compulsory password changes at specified intervals. Yet, regulatory compliance frameworks such as PCI-DSS still require the use of password expiration. Introducing banned-password lists and breached password protection significantly bolsters password security. Specops Password Policy allows implementing both banned-password lists and breached password protection with little effort.
(Last updated on November 8, 2024)

