See what passwords are exposing your business
Specops Password Auditor scans your Active Directory in minutes.

Block weak and common passwords, simplify password policy management, enforce compliance requirements, and block over 4 billion compromised passwords 24/7 from your Active Directory.
IT security starts with strengthening the weakest link – passwords.
Specops Software is a leading password management and authentication solution vendor. We protect business data by blocking weak passwords and securing user authentication. Our solutions are natively integrated with Active Directory, ensuring all sensitive data is stored on-premises.
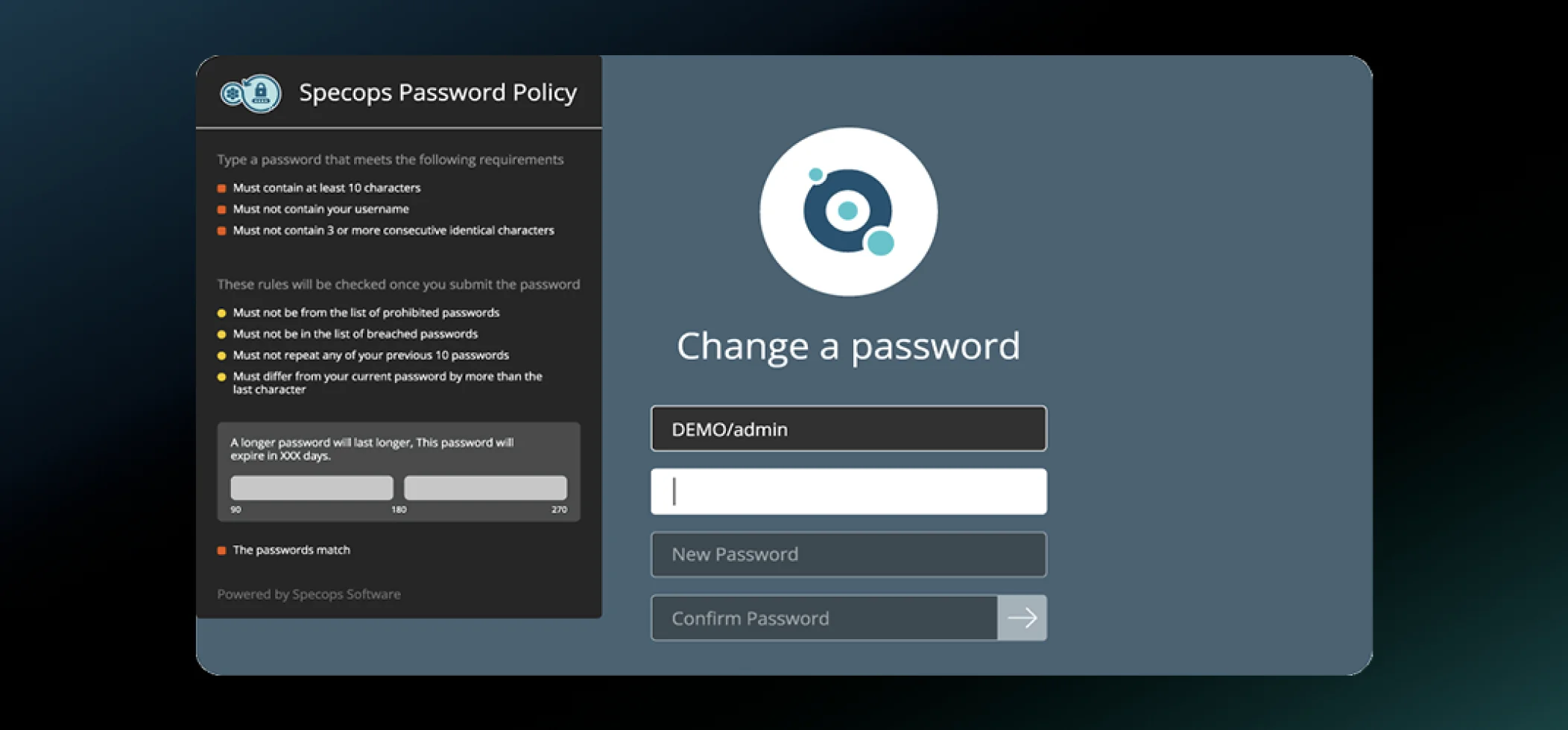
Eliminate weak and leaked passwords from your environment.
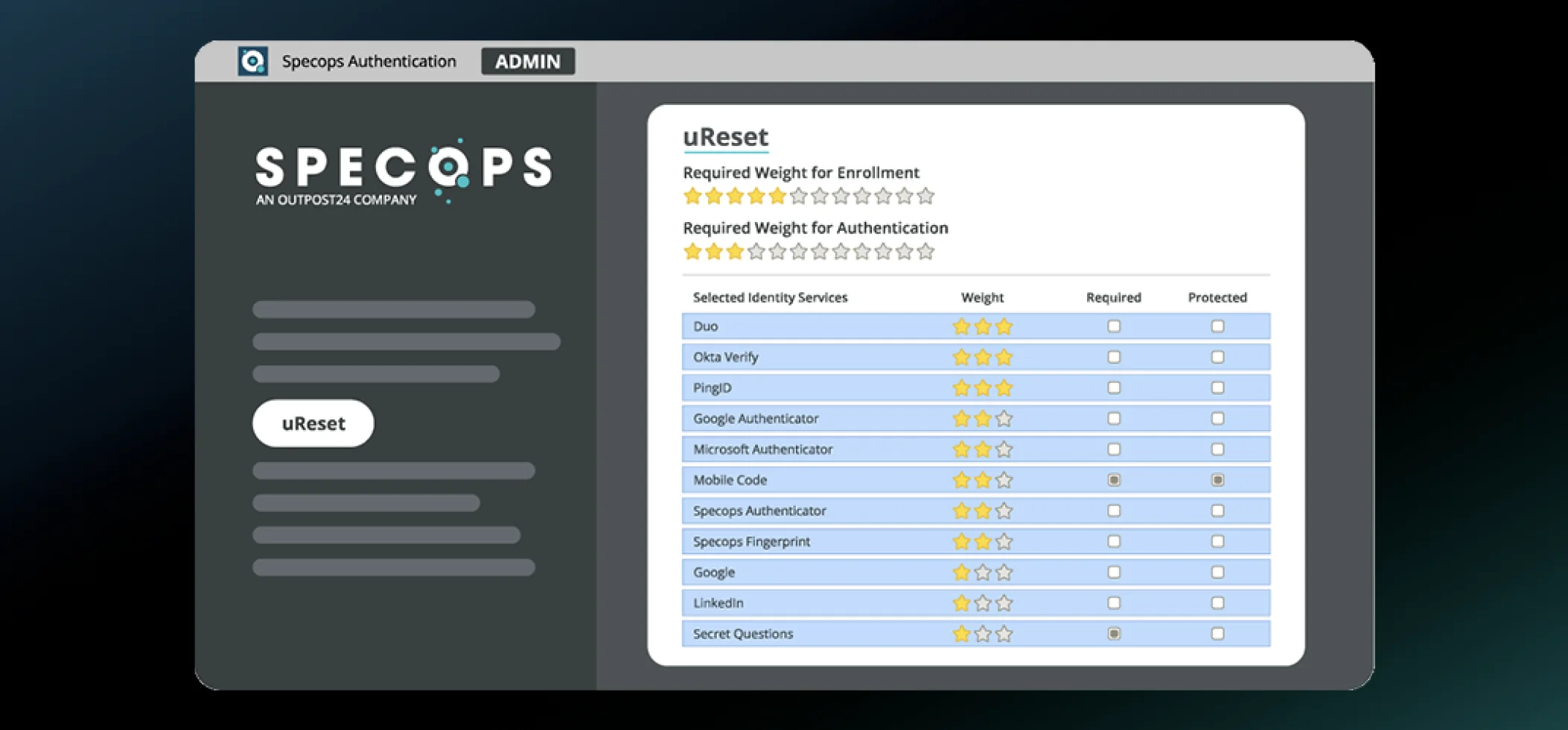
Stop password resets and lockouts from exhausting valuable IT resources.
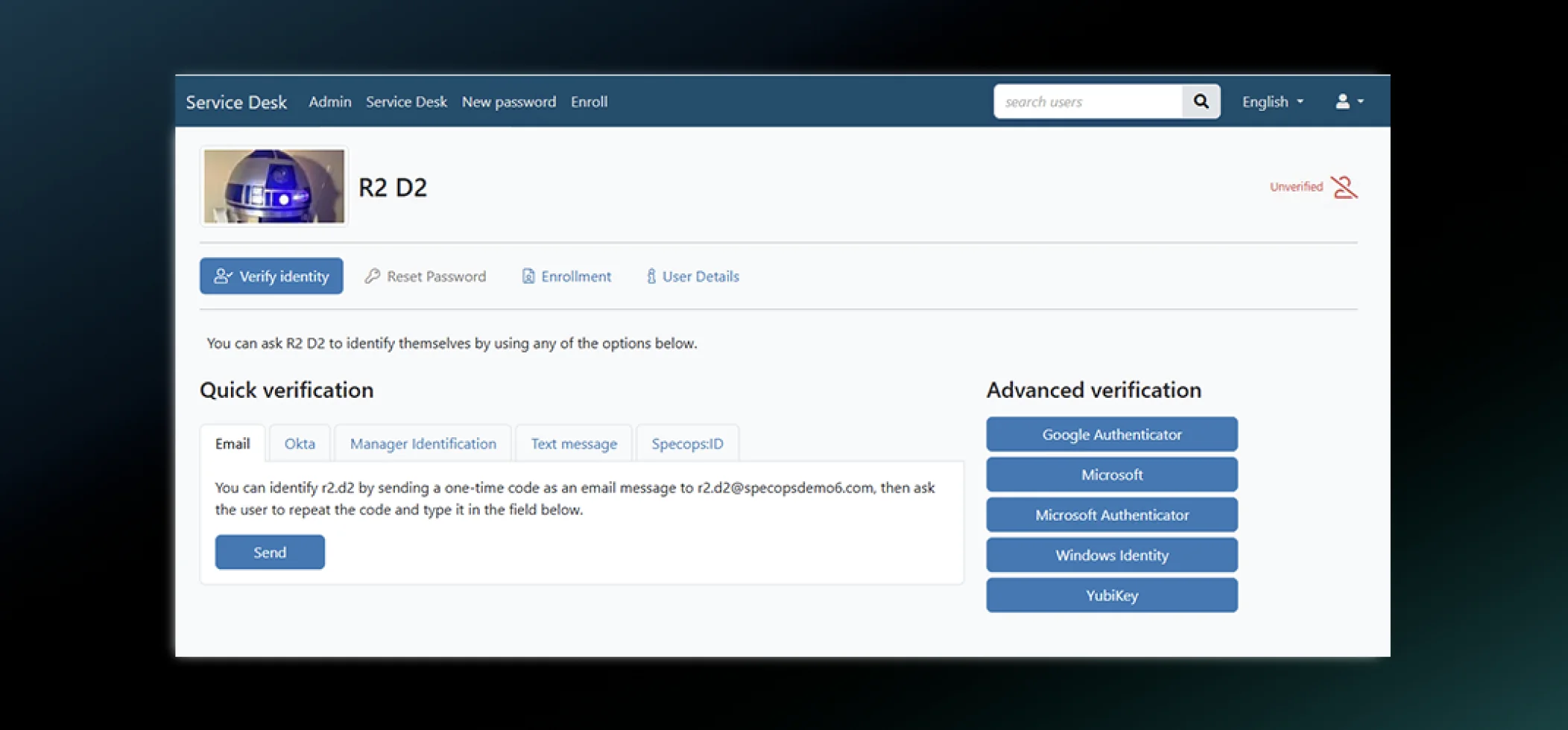
Authenticate users at the service desk to prevent social engineering attacks.
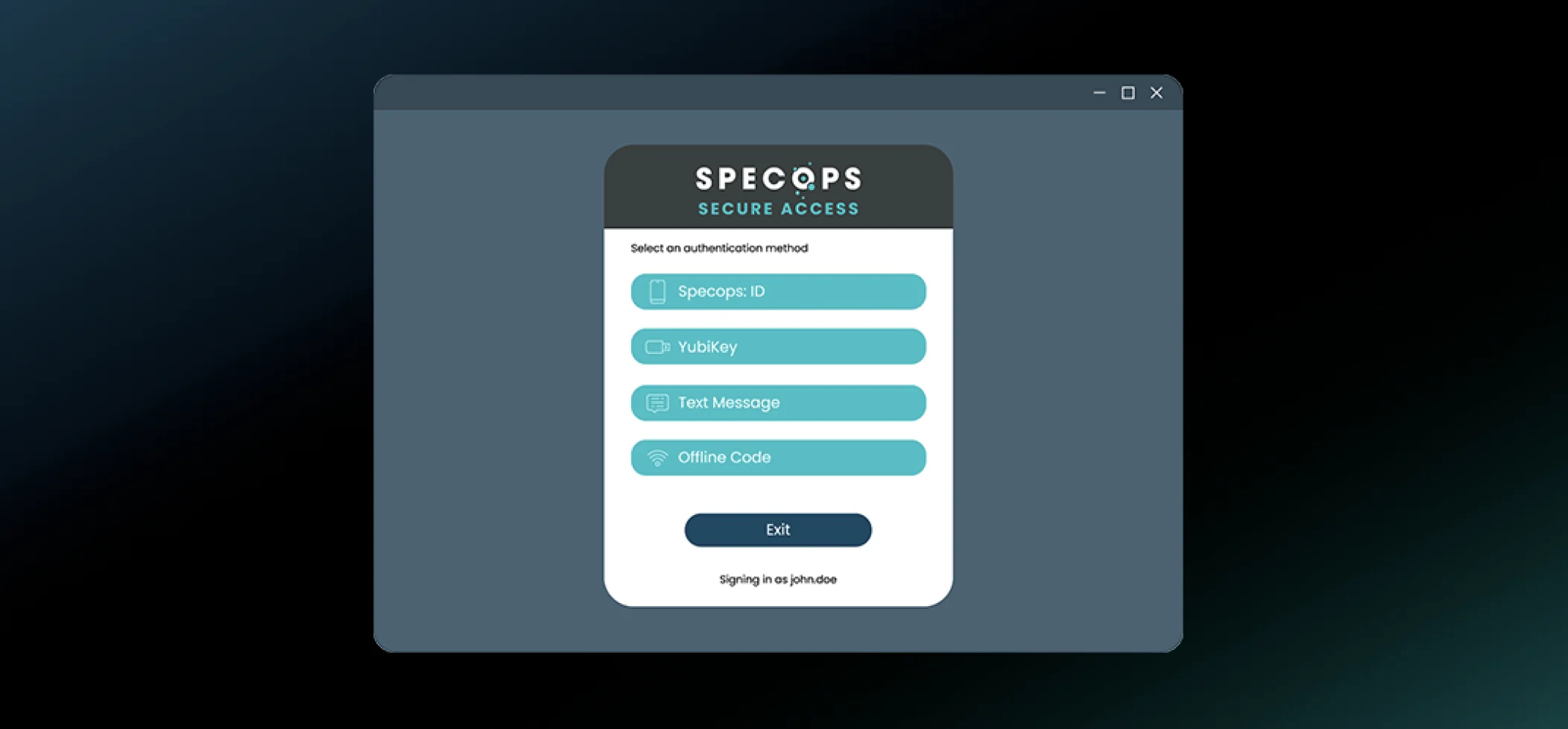
Safeguards your business from unauthorized access and password related threats when users login into Windows environments, VPNs and RDP connections.
Specops Password Auditor scans your Active Directory in minutes.
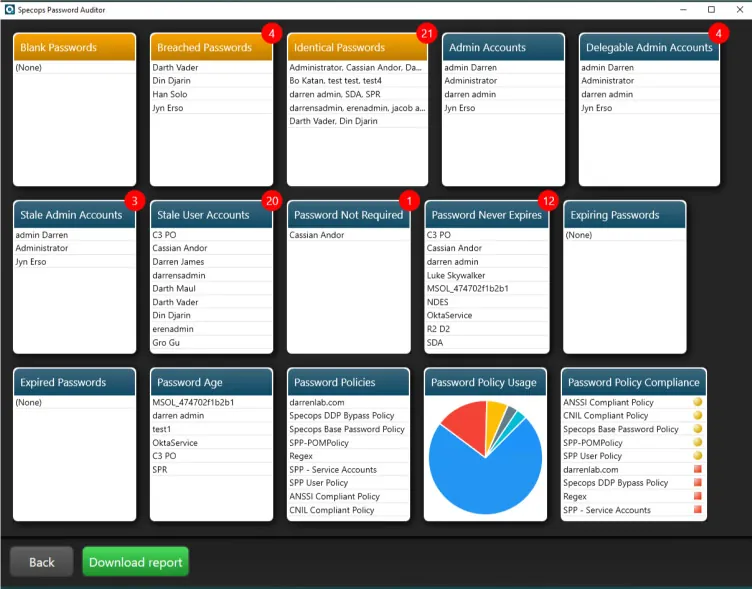
The Specops research team has analyzed 10 million random passwords from the 1 billion+ breached password list used by Specops Password Auditor. These are all real compromised passwords that have been captured by Specops, which you can scan your own Active Directory against right now. Our team have mapped out the most common length and…
Read MoreAuthentication and password security is more important than ever. Our password audit tool scans your Active Directory and identifies password-related vulnerabilities. The collected information generates multiple interactive reports containing user and password policy information.
Try It Now