Updating the Specops Arbiter Server Certificate
The Specops Arbiter service uses a self-signed certificate to encrypt communications from domain controllers to query the Specops API. If this certificate is expired or inadvertently deleted, the Arbiter server may not be able to start.
Table of contents
Identify the Certificate Currently In Use
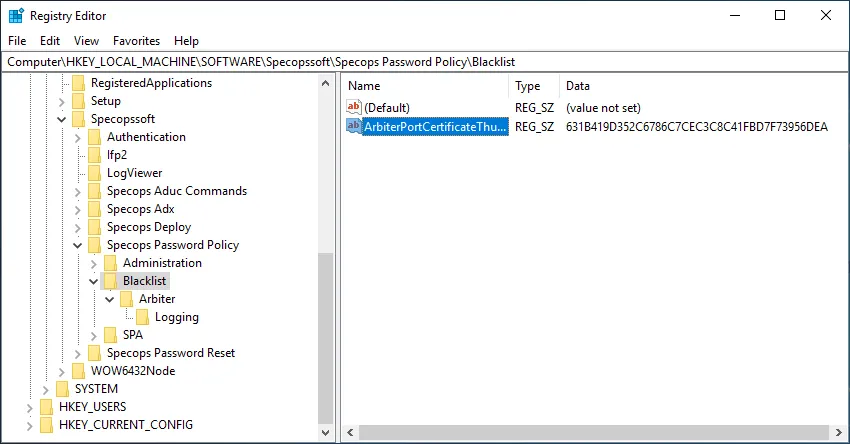
The Arbiter uses the certificate identified by the thumbprint stored in the registry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Specopssoft\Specops Password Policy\Blacklist]
"ArbiterPortCertificateThumbprint"="<certificate thumbprint>"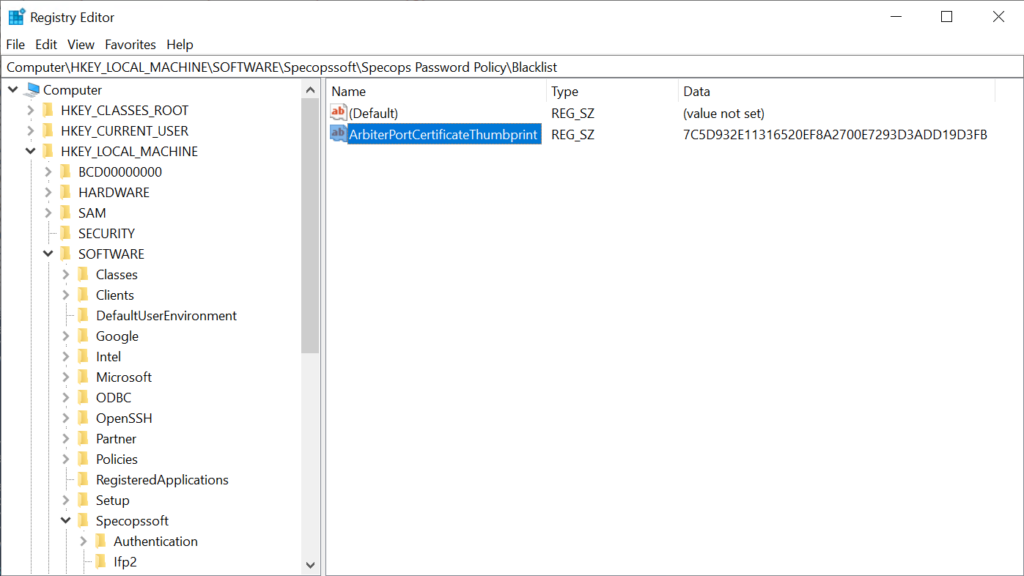
The value of this parameter indicates the thumbprint of the certificate currently in use. Check the computer account personal certificate store for the corresponding certificate. To find the certificate via an admin PowerShell:
dir cert:\localmachine\my\<certificatethumbprint> | fl
Substituting <certificatethumbprint> with the value from the config file, e.g.
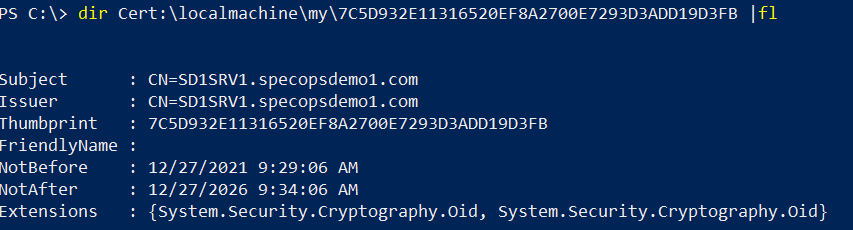
The certificate subject should match the FQDN of the server; the certificate dates should also be valid for the current date. If the certificate has expired it must be renewed. If no results are returned, this indicates the certificate no longer exists and must be replaced.
Create A New Self-Signed Certificate
A new self-signed certificate can be created through any means available (e.g. an AD-integrated Certificate Authority); our only requirement is that the certificate subject matches the FQDN of the Arbiter server. The following PowerShell command creates the appropriate certificate good for ten years:
New-SelfSignedCertificate -Subject "$env:computername.$env:userdnsdomain" -NotAfter (Get-Date).AddYears(10) -friendlyname "Arbiter $(get-date)"
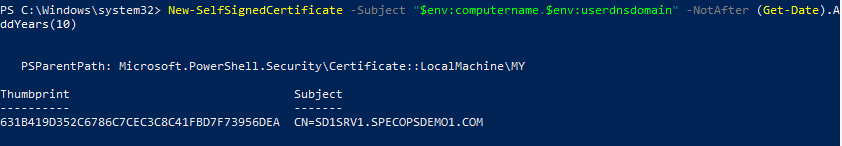
The command will create the cert and output the thumbprint.
Install The New Certificate Manually
Manual Install
Update the Registry
Update the registry value mentioned earlier with the new thumbprint.
Update the netsh http bindings
The old certificate will remain bound in Windows; we must update this binding manually. To view the current binding from an admin command prompt:
netsh http show sslcert 0.0.0.0:4383
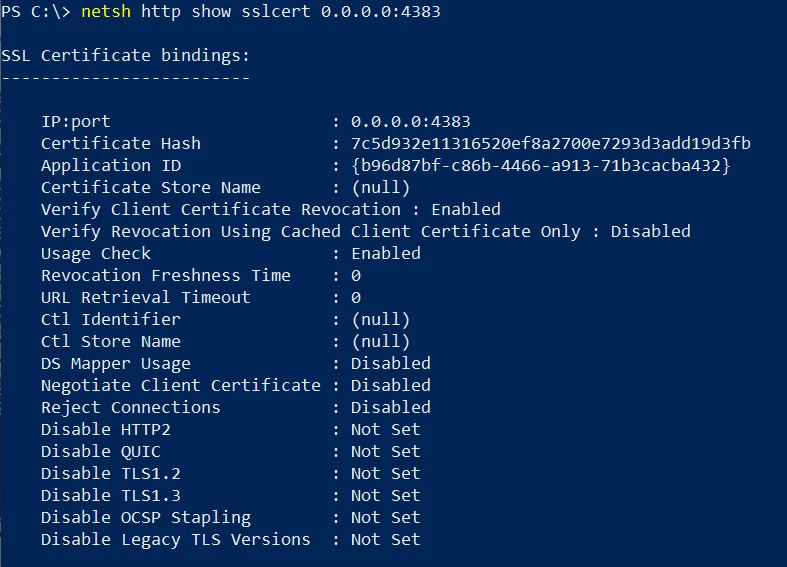
Note our old cert thumbprint still appears as “Certificate Hash” here. Also note the Application ID which will be unique to each Arbiter server installation.
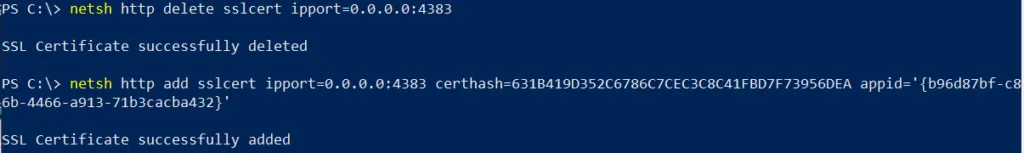
We must delete this binding and recreate it with our new cert thumbprint from earlier.
netsh http delete sslcert 0.0.0.0:4383 netsh http add sslcert 0.0.0.0:4383 certhash=<CERT_THUMBPRINT> appid=<YOUR_APP_ID>
For example:
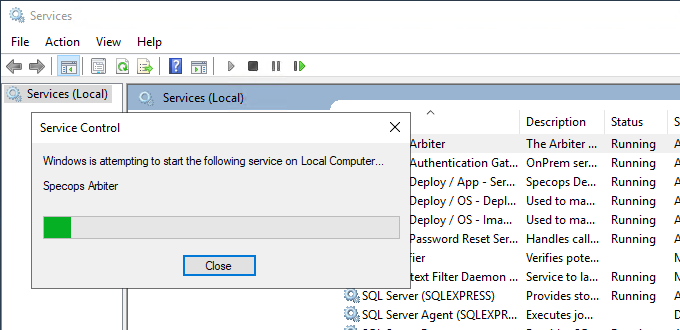
Restart the Service
Restart the Specops Arbiter service for the change to take effect.
PowerShell Scripted Install
The following PowerShell script will update the registry and bindings with a specified certificate and restart the service for you:
function Update-ArbiterBinding () {
$arbiterIPport = "0.0.0.0:4383"
$certThumbprintRegistryPath = "REGISTRY::HKEY_LOCAL_MACHINE\SOFTWARE\Specopssoft\Specops Password Policy\Blacklist"
try {
$appID = $($(netsh http show sslcert "$arbiterIPport" | findstr "Application ID").split(' ') | ? { $_ -match '\S' })[3]
}
catch [System.Management.Automation.RuntimeException] {
write-verbose -verbose "Did not find netsh cert binding $arbiterport. Aborting."
exit
}
catch {
write-verbose -verbose $_
exit
}
if (test-path $certThumbprintRegistryPath) {
$certThumbprint = $(get-itemproperty -path "$certThumbprintRegistryPath").ArbiterPortCertificateThumbprint
} else {
write-verbose -verbose "Failed to get thumbprint from registry"
exit
}
if (test-path Cert:\LocalMachine\my\"$certThumbprint") {
write-verbose -verbose "Will update binding for app ID $appID with certificate $certThumbprint"
netsh http delete sslcert "$arbiterIPport"
netsh http add sslcert ipport="$arbiterIPport" certhash="$certThumbprint" appid="$appID"
} else {
write-verbose -verbose "Thumbprint from registry not found, will not update binding"
exit
}
}
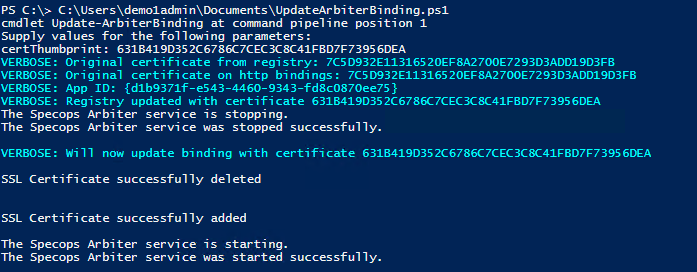
Update-ArbiterBinding
Sample output:
Validate the Certificate Install
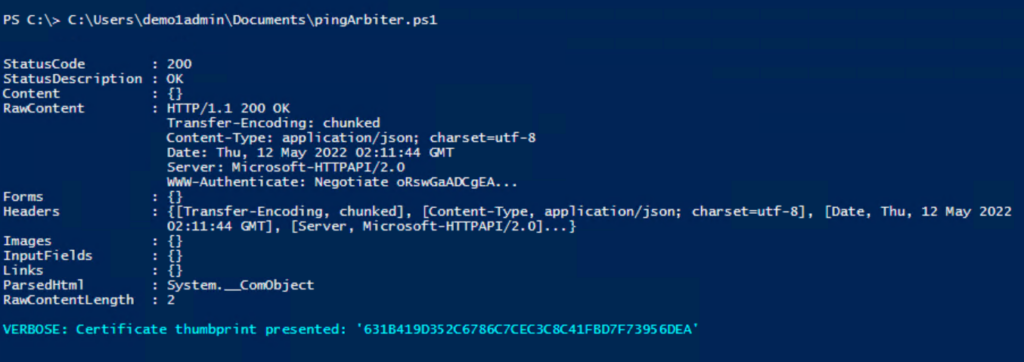
The following PowerShell script will connect to the local Arbiter server and confirm it is operational, as well as display the thumbprint of the certificate currently in use:
function Ping-Arbiter($hostname) {
Add-Type @"
using System.Net;
using System.Security.Cryptography.X509Certificates;
public static class LastCertificateUsedPersister
{
public static string Thumbprint;
}
public class AllowAllCertificatesPolicy : ICertificatePolicy {
public bool CheckValidationResult(ServicePoint srvPoint,
X509Certificate certificate,
WebRequest request, int certificateProblem) {
LastCertificateUsedPersister.Thumbprint = ((X509Certificate2)certificate).Thumbprint;
return true;
}
}
"@
[System.Net.ServicePointManager]::CertificatePolicy = New-Object AllowAllCertificatesPolicy
Invoke-WebRequest -UseDefaultCredentials "https://$($hostname):4383/Diagnostics/Ping"
Write-Verbose -Verbose ("Certificate thumbprint presented: '{0}'" -f [LastCertificateUsedPersister]::Thumbprint)
}
Ping-Arbiter "$env:computername.$env:userdnsdomain"
Sample output: