How to check the health of your Password Policy config
*This article applies to version 7.11 or later*
This article will walk you through the steps we would check to verify a Specops Password Policy configuration.
Checking Specops Password Policy Administration Tools
We will start by checking the Password Policy Administration Tools to see if there are any errors.
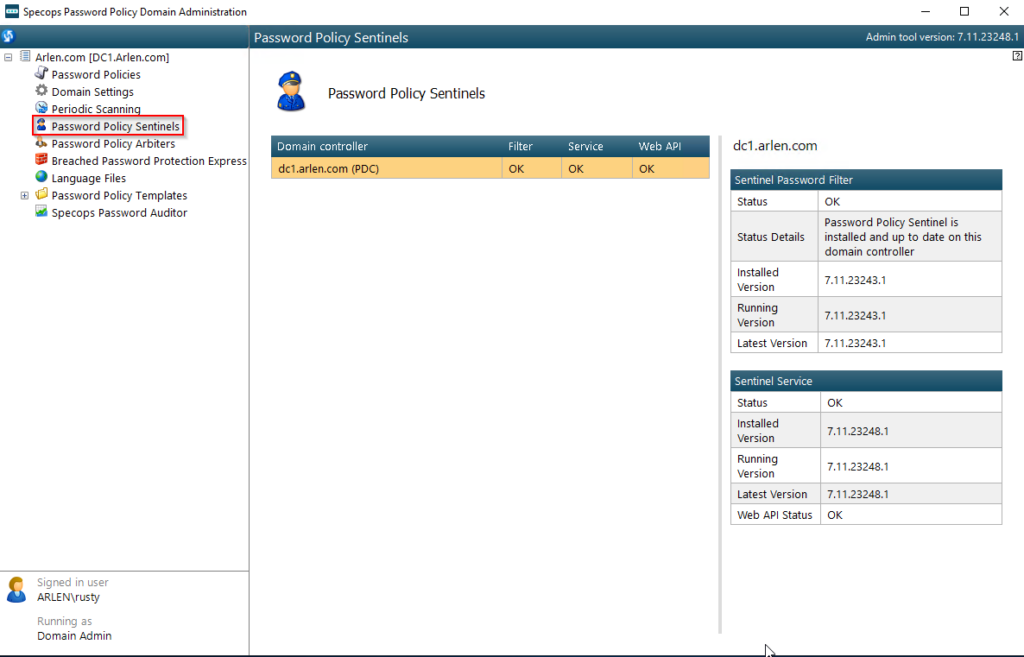
Now, let’s click on Password Policy Sentinels: This will do a check of all your writeable Domain Controllers, and report on the version of Sentinel installed. Any DC listed here should have the Specops Password Policy Sentinel installed as it is a requirement of the product. They should also be the same version. When users change passwords the Sentinel is what checks the password and evaluates against Specops Password Policy. It is critical that the Specops Password Policy Sentinel is on all of your writeable DCs!
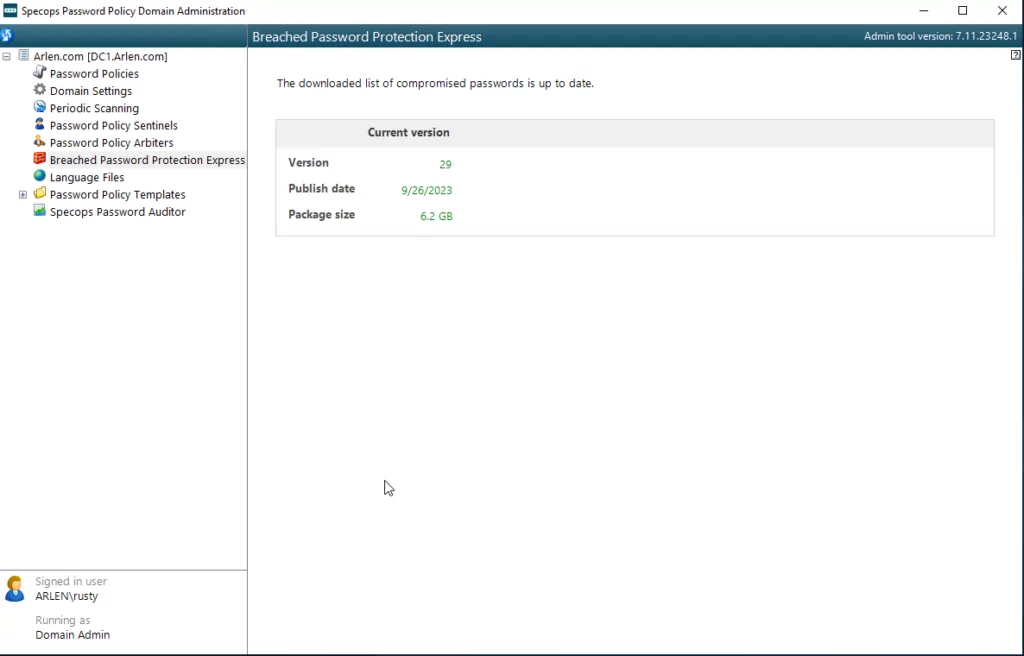
Optional for Breached Password Protection Licensed customers:
Under Breached Password Protection Express, we see the version of the Express List. If the version is out of date, we can update by clicking on “Download latest version” to ensure we have the latest list of leaked passwords for BPP Express. (This list is updated every 1-2 Months)
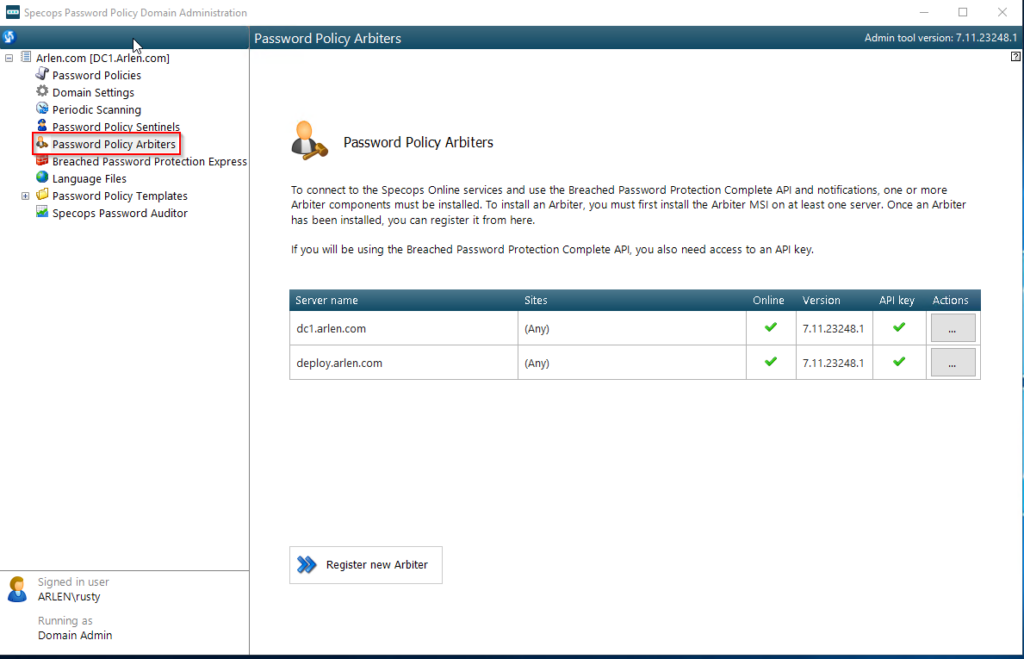
Under Password Policy Arbiters, the server(s) where your arbiter(s) is(are) installed, and green checks for Online, and API key.
Next, click on Password Policies near the top left. The Admin Tools do a query to check for any group policies that contain any Specops Password Policy settings within them. These will be the policies that drive Specops Password Policy. You will want to validate that your group policy being used for Specops Password Policy is listed.
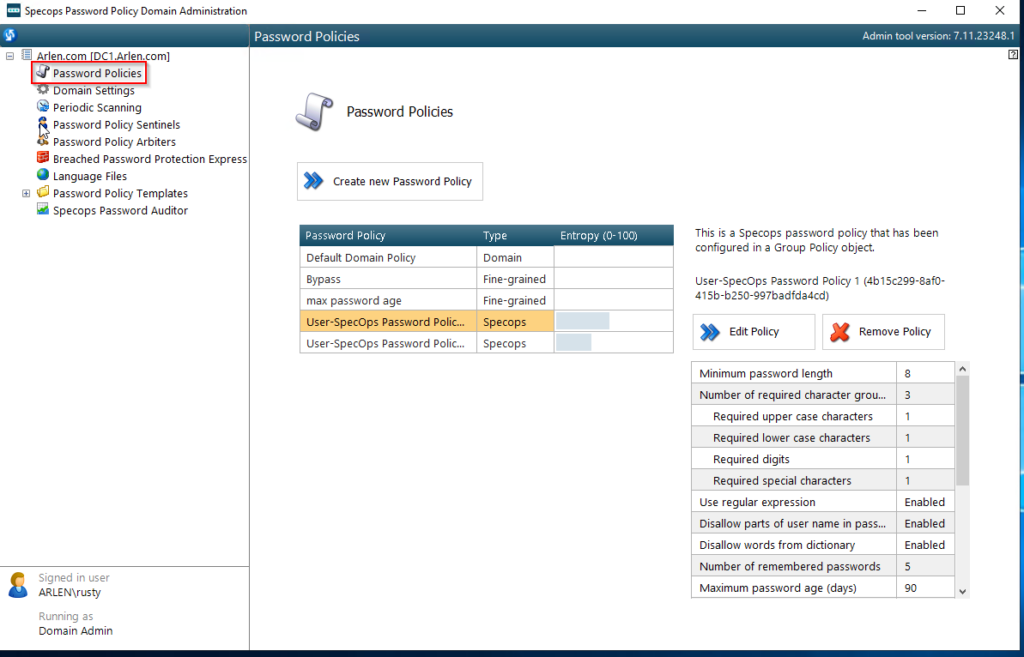
If your policy is not listed above, ensure that in Group Policy Management the GPO that has Specops Password Settings is still there, and that User Settings for that GPO are enabled. If your GPO exists, but the User Settings are disabled, they will not show up here as Specops Password Policy is user settings based. They will need to be enabled.
From there, we can select the policy (shown in orange) and look at a summary of settings. You can also click on Edit Policy to make changes to your Specops Password Policy.
Check that our Specops Password Policy is assigned to our users
We now should check that are policy is applied correctly.
Check the scopes/links of our group policy.
- Open Group Policy Management.
- Expand Domains, and then your domain.
- Look under Group Policy Objects for the GPO with the name we identified in the Password Policy Administration Tools / Password Policies screen and click on it.
- Once selected, you can take a look at the Scopes of your policy, and any filtering. This should tell you which OUs/Users have your Specops Password Policy GPO assigned to it.
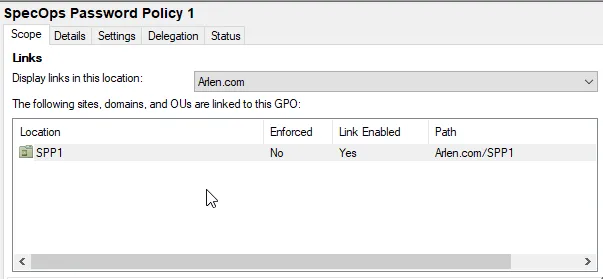
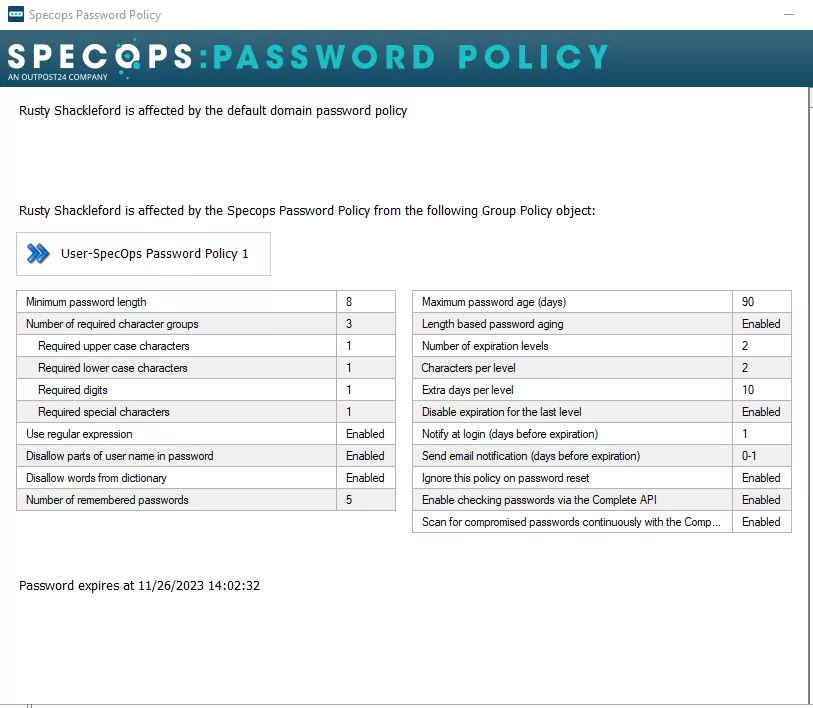
Use Active Directory Users and Computers to validate that our Specops Password Policy is being applied to particular users.
A good idea is to install Active Directory Users and Computers on the server which has your Password Policy Domain Admin Tools. This will give the ability to check individual users by right clicking them in Active Directory Users and Computers, and using the context menu.
For further documentation on scoping users and to adjust user counts, view this article
Check Domain Controllers for Specops Password Policy Events and Sentinel Service status
Check Domain Controllers for Specops Password Policy Events
Another item to check is your Domain Controllers(any DCs where users would authenticate against), for events that Specops Password Policy logs when it evaluates a password change.
- Open up Event Viewer, Windows Logs, Application.
- Filter events to show from source “Specops Password Policy Sentinel”
- If Specops Password Policy is applying, I would expect some events to the ones below:
| Event Source | Event ID | Description |
|---|---|---|
| Specops Password Policy Sentinel | 102 | Successful Password change performed by user. |
| Specops Password Policy Sentinel | 103 | Failed Password change performed by user. |
| Specops Password Policy Sentinel | 202 | Successful Password reset performed by administrator. |
| Specops Password Policy Sentinel | 203 | Failed Password reset performed by administrator. |
If you do not see these events then there are a few common reasons why you would not:
- Default Domain Policy is rejecting the password first, and Specops Password Policy is not getting to evaluate the password. It’s important to under Default Domain Policy and Specops Password Policy precedence as described here.
- The user you are checking is not being affected by Specops Password Policy. See the section on checking to see if Specops Password Policy GPOs are being applied to a specific user.
- The particular DC you are checking was not the one that handled the password change request.
For more information on tracking why a password might be getting rejected you can review the knowledgebase article here.
Check Specops Password Policy Sentinel service is running
Specops Password Policy expiration notification emails go out on your PDC by default via a service called Specops Password Sentinel Service. This service should be up and running on your PDC(and ideally all DCs).
Note: The Specops Password Sentinel Service is not required to enforce policy rules.
